Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications . He installed a fake communication tower between two authentic endpoints to mislead the victim. The Bobby used the virtual tower to interrupt the data transmission between the user and real tower, attempting to hijack an active session. Upon receiving the user’s request. Bobby manipulated the traffic with the virtual tower and redirected the victim to a malicious website.
What is the attack performed by Bobby in the above scenario?
Option 1 : KRACK attack
Option 2 : aLTEr attack
Option 3 : Wardriving
Option 4 : Jamming signal attack
1. KRACK attack
We discovered serious weaknesses in WPA2, a protocol that secures all trendy protected Wi-Fi networks. an attacker within range of a victim will exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers will use this novel attack technique to scan info that was previously assumed to be safely encrypted. this will be abused to steal sensitive info like mastercard numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks. depending on the network configuration, it’s additionally doable to inject and manipulate information. as an example, an attacker can be ready to inject ransomware or alternative malware into websites.
The weaknesses are within the Wi-Fi standard itself, and not in individual products or implementations. Therefore, any correct implementation of WPA2 is likely affected. to forestall the attack, users should update affected products as soon as security updates become offered. Note that if your device supports Wi-Fi, it’s most likely affected. during our initial analysis, we have a tendency to discovered ourselves that android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, area unit all affected by some variant of the attacks. For more info about specific products, consult the info of CERT/CC, or contact your merchant.
The analysis behind the attack are presented at the pc and Communications Security (CCS) conference, and at the Black Hat Europe conference. Our detailed analysis paper will already be downloaded.
Update October 2018: we’ve a follow-up paper wherever we generalize attacks, analyze additional handshakes, bypass Wi-Fi’s official defense, audit patches, and enhance attacks using implementation-specific bugs.
DEMONSTRATION
As a proof-of-concept we have a tendency to executed a key reinstallation attack against an robot smartphone. during this demonstration, the attacker is in a position to decrypt all information that the victim transmits. For an attacker this is often straightforward to accomplish, as a result of our key reinstallation attack is exceptionally devastating against UNIX system and robot half dozen.0 or higher. this is} as a result of robot and UNIX system can be tricked into (re)installing an all-zero encryption key (see below for additional info). once offensive other devices, it’s harder to decrypt all packets, though an outsized variety of packets will nevertheless be decrypted. In any case, the subsequent demonstration highlights the kind of knowledge that an attacker will acquire once activity key reinstallation attacks against protected Wi-Fi networks:
Our attack isn’t restricted to sick login credentials (i.e. e-mail addresses and passwords). In general, any information or info that the victim transmits may be decrypted. in addition, counting on the device being employed and also the network setup, it’s additionally doable to decipher information sent towards the victim (e.g. the content of a website). though websites or apps might use HTTPS as a further layer of protection, we have a tendency to warn that this additional protection will (still) be bypassed during a worrying variety of things. as an example, HTTPS was previously bypassed in non-browser package, in Apple’s iOS and OS X, in robot apps, in robot apps once more, in banking apps, and even in VPN apps.
DETAILS
Our main attack is against the 4-way handshake of the WPA2 protocol. This handshake is executed once a consumer needs to hitch a protected Wi-Fi network, and is employed to confirm that each the consumer and access purpose possess the right credentials (e.g. the pre-shared secret of the network). At identical time, the 4-way handshake additionally negotiates a recent encoding key that may be wont to write all sequent traffic. Currently, all trendy protected Wi-Fi networks use the 4-way handshake. this suggests of these networks area unit suffering from (some variant of) our attack. for example, the attack works against personal and enterprise Wi-Fi networks, against the older WPA and also the latest WPA2 normal, and even against networks that solely use AES. All our attacks against WPA2 use a completely unique technique known as a key reinstallation attack (KRACK):
Key reinstallation attacks: high level description
In a key reinstallation attack, the adversary tricks a victim into reinstalling an already-in-use key. this is often achieved by manipulating and replaying science handshake messages. once the victim reinstalls the key, associated parameters like the progressive transmit packet variety (i.e. nonce) and receive packet variety (i.e. replay counter) area unit reset to their initial price. primarily, to ensure security, a key ought to solely be put in and used once. sadly, we have a tendency to found this is often not secure by the WPA2 protocol. By manipulating cryptographic handshakes, we are able to abuse this weakness in observe.
Key reinstallation attacks: concrete example against the 4-way handshake
As represented within the introduction of the analysis paper, the concept behind a key reinstallation attack may be summarized as follows. once a consumer joins a network, it executes the 4-way handshake to barter a recent encoding key. it’ll install this key once receiving message three of the 4-way acknowledgement. Once the key’s put in, it’ll be wont to write traditional information frames mistreatment associate encoding protocol. However, as a result of messages is also lost or born, the Access purpose (AP) can transmit message three if it didn’t receive an appropriate response as acknowledgment. As a result, the consumer might receive message three multiple times. every time it receives this message, it’ll instal identical encoding key, and thereby reset the progressive transmit packet variety (nonce) and receive replay counter utilized by the encryption protocol. we have a tendency to show that associate attacker will force these time being resets by collecting and replaying retransmissions of message three of the 4-way handshake. By forcing time being recycle during this manner, the encoding protocol may be attacked, e.g., packets may be replayed, decrypted, and/or solid. the same technique may also be wont to attack the cluster key, PeerKey, TDLS, and quick BSS transition handshake.
2. aLTEr attack
The new aLTEr attack can be used against nearly all LTE connected endpoints by intercepting traffic and redirecting it to malicious websites together with a particular approach for Apple iOS devices.
This attack works by taking advantage of a style flaw among the LTE network — the information link layer (aka: layer-2) of the LTE network is encrypted with AES-CTR however it’s not integrity-protected, that is why an offender will modify the payload.
As a result, the offender is acting a classic man-in-the-middle wherever they’re movement as a cell tower to the victim, whereas deceit to be the $64000 subscriber to the $64000 network. The traffic from the victim is shipped to the offender wherever it’s changed and forwarded into the $64000 network.
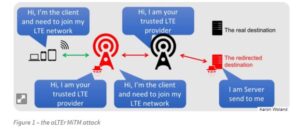
These forms of attacks are not solely restricted to LTE networks. 5G networks might also be liable to these attacks in future – if they don’t institute integrity protection.
3. Wardriving
Wireless networks have actually brought heaps of convenience to our lives, permitting us to figure and surf from virtually anywhere—home, cafes, airports and hotels round the globe. however sadly, wireless property has additionally brought convenience to hackers as a result of it offers them the chance to capture all knowledge we kind into our connected computers and devices through the air, and even take hold of them.
While it’s going to sound odd to stress concerning bad guys snatching our personal data from what looks to be nothingness, it’s additional common than we’d prefer to believe. In fact, there are hackers who drive around finding out unsecured wireless connections (networks) employing a wireless laptop and moveable world positioning system (GPS) with the only purpose of stealing your data or victimization your network to perform dangerous deeds.
We decision the act of cruising for unsecured wireless networks “war driving,” and it will cause some serious hassle for you if you haven’t taken steps to safeguard your home or tiny workplace networks.
Hackers that use this system to access knowledge from your computer—banking and private information—that may lead to fraud, loss, or maybe a listing (if they use your network for nefarious purposes). Any laptop or mobile device that’s connected to your unprotected network might be accessible to the hacker.
While these are shuddery situations, the nice news is that there are ways that to forestall “war drivers” from gaining access to your wireless network. make certain to envision your wireless router owner’s manual for directions on a way to properly alter and tack together these tips.
• Turn off your wireless network once you’re not home: this can minimize the prospect of a hacker accessing your network.
• Change the administrator’s password on your router: Router makers sometimes assign a default user name and password permitting you to setup and tack together the router. However, hackers usually know these default logins, therefore it’s vital to vary the password to one thing tougher to crack.
• Enable encryption: you can set your router to allow access solely to those users who enter the right password. These passwords are encrypted (scrambled) after they are transmitted so hackers who try and intercept your connection can’t browse the data.
• Use a firewall: Firewalls will greatly reduce the prospect of outsiders penetrating your network since they monitor makes an attempt to access your system and block communications from unapproved sources. So, check that to use the firewall that comes along with your security package to supply an additional layer of defense.
Although war driving may be a real security threat, it doesn’t need to be a hazard to your home wireless network. With some precautions, or “defensive driving” measures, you’ll be able to keep your network and your knowledge secured down.
4. Jamming signal attack
Remote control and sensing over wireless communication has been continuously increasing. This trend won’t abate with such a lot expectation for the net of Things. However, the unfold of wireless communication will produce vulnerability to varied management systems because it will simply be discontinuous by Denial-of-Service attacks through jam of transmissions. during this article, we offer a quick summary on this new essential issue and therefore the current efforts created by researchers in IFAC.
Cyber security has become an important issue for the society. data and communication technologies are heavily incorporated in several fields and nonetheless they’re exposed to cyber-attacks that threaten money losses, environmental damages, and disruption of services employed in existence.
Recent analysis indicates that industrial management systems are not any exception being below threats by malicious attackers. Communication channels used for transmission of measure and management knowledge are vulnerable against varied sorts of attacks.
jamming attacks, that are Denial-of-Service attacks on wireless channels. jam attacks are maybe the only sorts of attacks an impact system might face, however they’ll be very dangerous. Generating a jam attack doesn’t need data concerning the internals of the system. By merely emitting an interference signal, a jam attacker will effectively block the communication on a wireless channel, disrupt the traditional operation, cause performance problems, and even harm the system.
Typically jamming attacks are classified in two categories: active jamming and reactive jamming . An active jammer’s goal is to keep the channel busy regardless of whether the channel is being used or not. For example, the attacker can continuously send strong radio signals to increase the signal-to-noise-plus-interference ratio at the receiver side. A reactive jammer on the other hand observes the channel activity and starts jamming only when the channel is being used.
One of the key problems that create jam attacks a giant threat is that they’re straightforward to launch. As a recent survey indicates, jam devices which will target varied wireless technologies together with GPS, mobile communications, and Wi-Fi are already offered for getting. it’s mentioned that within the case of Wi-Fi, even special devices might not be required as computers may be was jammers.
On prime of this, increasing security against jam might not invariably be straightforward. sure sorts of concealed jam attacks will cause important quantity of failures in packet delivery on a wireless channel while not being detected
One in all the ways that of mitigating jam attacks is to use frequency hopping ways, wherever transmissions ar revamped a random sequence of various frequencies. however a strong wrongdoer will still overcome such ways.
There are some cases of jam incidents that indicate the criticality of the problem. In 2015, cars set close to a business establishment couldn’t be unbolted remotely victimization key fobs, that indicated the presence of a transmitter that interrupted the key fob signals . Another far more regarding case involves Associate in Nursing explosion of an oil pipeline. A recent report on the explosion of Baku-Tbilisi-Ceyhan pipeline in 2008 hints the chance of cyber-attacks that concerned jam of satellite communications to forestall transmission of alerts.
It appears that jamming can stay to be a significant issue. Researchers imply that subsequent generation traffic communication systems, vehicle platoons, the satellite navigation, and therefore the power market are all prone to jam attacks. With the growth of the web of Things, the employment of wireless communications is quickly increasing in several fields and jam is becoming a much bigger threat. This prompts a very important question: how will we be ready for jamming attacks?
Within IFAC, researchers are addressing this question from the perspective of management engineering. These efforts embody
• evaluation of the performance of existing management systems below jam attacks, and
• development of latest systems that square measure resilient to jam attacks.
We shortly introduce these lines of analysis below. it’s attention-grabbing that these researches manage cyber attacks, however the approaches aren’t supported data technology directed ways.
In a typical wireless networked system setup, remotely situated parts exchange information with one another over wireless medium. Some researchers value the performance of wireless networked management systems by investigation the extent of jam that they will tolerate while not having major problems like disruption of operation. Since emitting jam signals needs energy, it’s pricey to the aggressor. it might be ideal if a sway system will operate even below attacks from associate degree aggressor with giant resources.
The challenge in evaluating the performance of a control system under jamming attacks is that we cannot know exactly when jamming attacks may start/end. Another issue is that the power of the jamming signal used by the attacker may be changing each time there is an attack. Therefore, it is also not clear how likely a transmission failure might occur when there is jamming. One of the approaches to understand the effects of jamming even in this uncertainty is to consider the worst-case scenarios that may happen.
To identify the worst case, it’s of interest to explore the question: What would be the best strategy of the attacker? The attacker would need to disrupt the traditional operation of a system while not victimisation excessive resources. as an example, in many analysis articles, jam energy is taken into account as a constraint within the downside, and it’s assumed that the aggressor tries to create the maximum amount harm as doable among such energy limits. Another approach is to think about jam energy as a district of the aggressor’s value operate in associate degree optimisation downside wherever the attacker tries to attenuate the energy usage. Some researchers additionally use game-theoretic ways for understanding however best ways of the aggressor would relate to the best strategy for the transmission of the activity and therefore the management information.
Designing management systems that square measure resilient to jam attacks is additionally a very important analysis theme among IFAC. as an example, some researchers studied management systems that incorporate mechanisms to discover the presence of associate degree attack. moreover, recently researchers additionally developed supposed event-triggered controllers to select times of knowledge transmissions therefore on cut back the impact of jam on the operation. If a selected transmission try faces a jam attack, a replacement TRM may be regular supported the performance needs.
Literature on the cyber security of management systems indicates that as associate degree aggressor becomes a lot of experienced the system, additionally to jam, a lot of refined attacks may additionally become associate degree possibility. The aggressor will alter the info being transmitted, and in sure cases inject false information into the system while not being noticed . additionally, management systems may additionally face replay attacks, wherever the aggressor intercepts the transmissions and sends a sound however recent measurement/control information to cause damages whereas still following the communication protocol.
As the risk of jam and different kinds of attacks is increasing quickly, ensuring cyber security of management systems are going to be a challenge of growing importance.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



