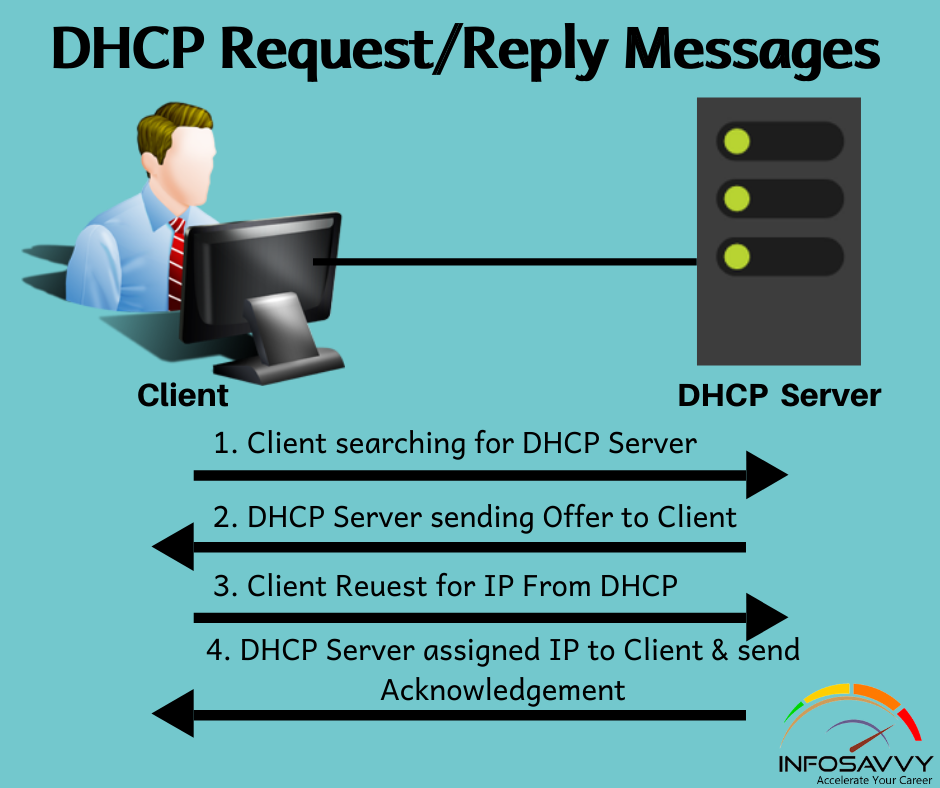
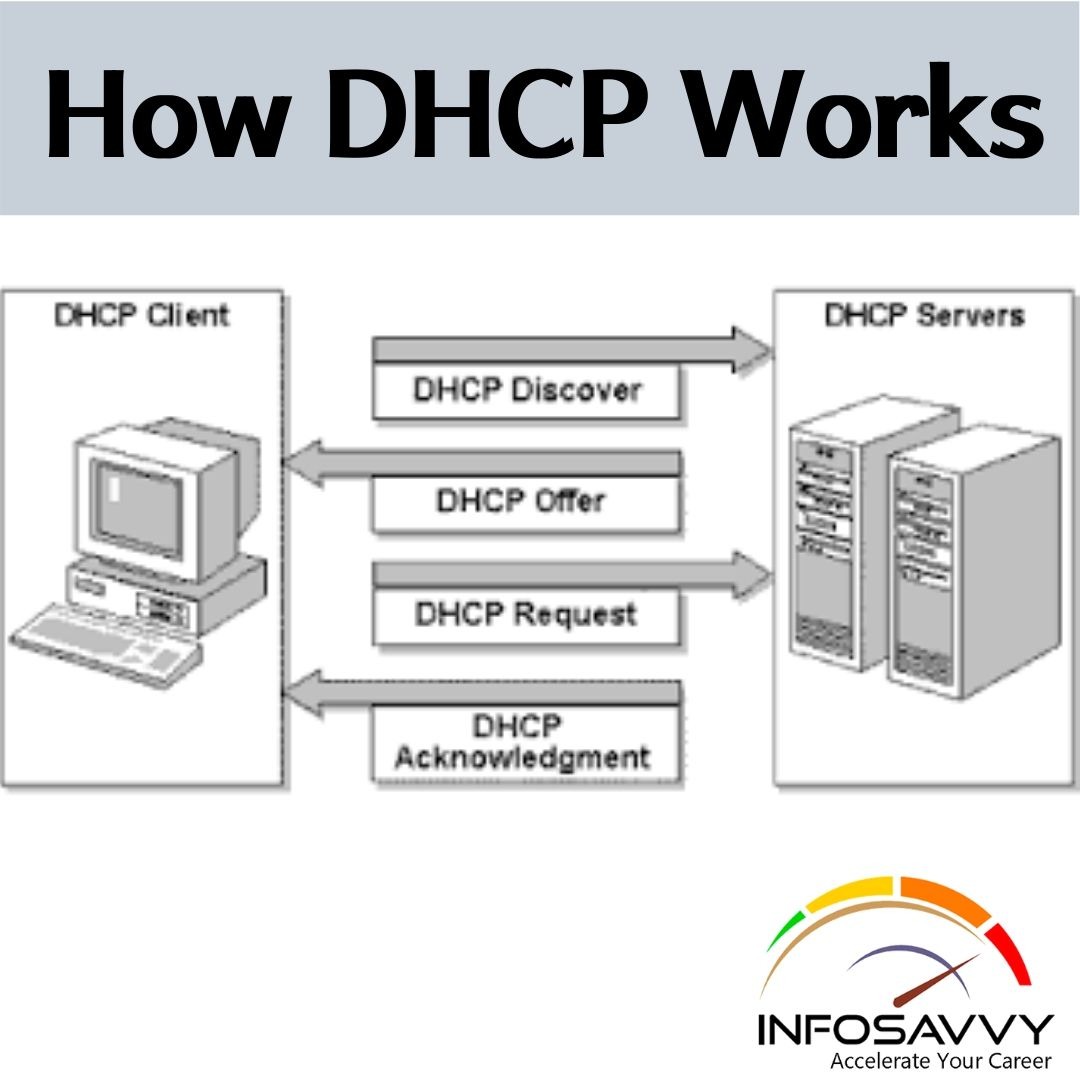
2020 Top 10 Cyber Attacks in India
2020 Top 10 Cyber Attacks in India most typical forms of It like Malware, Phishing, Man-In-The-Middle Attack, Denial-of-service attack etc. Such are the Attacks that you’ll learn in this article as well as you’ll get to understand what are cyber attacks with the assistance of its types. What are the Cyber Attacks? A Cyber Attack is defined as an attack originated by a digital system against another digital device, website, or the other digital system …