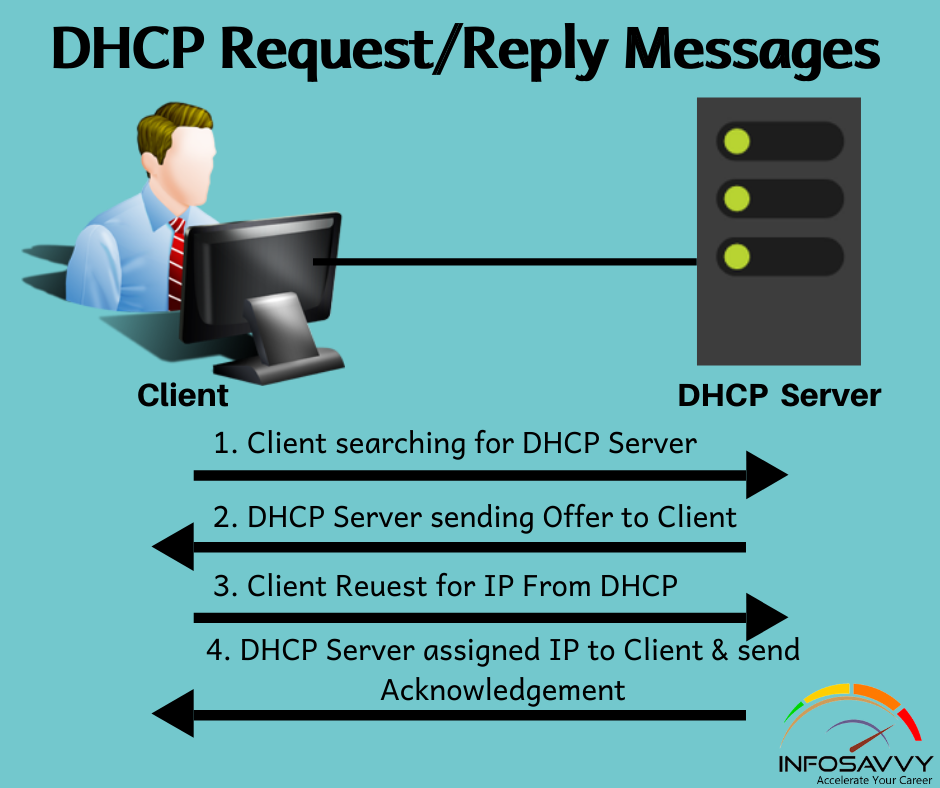
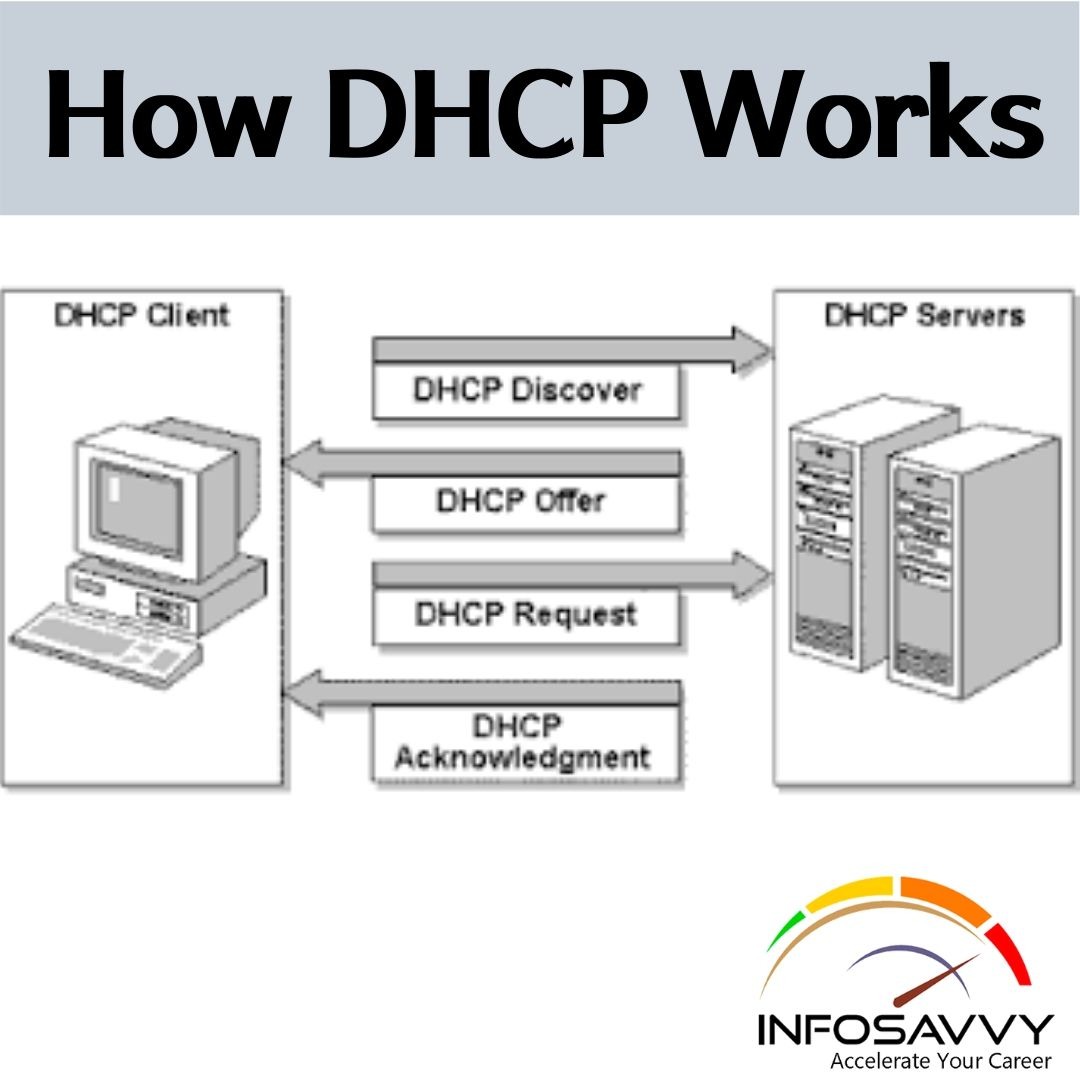
Learn Skills From Web Server Foot Printing / Banner Grapping
Learn Skills From Web Server Foot Printing / Banner Grapping By performing web server foot printing, you’ll gather valuable system-level data like account details, OS, software versions, server names, and database schema details. Use Telnet utility so as to footprint an internet server and gather information like server name, server type, operating systems, applications running, and so on. Use footprinting tools like Netcraft, ID Serve and httprecon, then on to perform web server foot printing, …
Learn Skills From Web Server Foot Printing / Banner Grapping Read More »