For a better understanding of Denial-of-Service Attack & Distributed Denial of Service (DoS/DDoS) attacks, one must be familiar with their concepts beforehand. This module discusses what a DoS attack is, what a DDoS attack is, and how the DDoS attacks work.

What is a Denial-of-Service Attack?
DoS is an attack on a computer or network that reduces, restricts, or prevents accessibility of system resources to its legitimate users. In a DOS attack, attackers flood a victim’s system with non-legitimate service requests or traffic to overload its resources, bringing the system down, leading to unavailability of the victim’s website or at least significantly slowing the victim’s system or network performance. The goal of a DoS attack is not to gain unauthorized access to a system or to corrupt data; it is to keep legitimate users away from using the system.
Following are the examples of types of DoS attacks:
- Flooding the victim’s system with more traffic than can be handled
- Flooding a service (e.g., internet relay chat (IRC)) with more events than it can handle
- Crashing a transmission control protocol (TCP/Internet protocol OP) stack by sending corrupt packets
- Crashing a service by interacting with it in an unexpected way
- Hanging a system by causing it to go into an infinite loop
DoS attacks come in a variety of forms and target a variety of services. The attacks may cause the following:
- Consumption of scarce and nonrenewable resources
- Consumption of bandwidth, disk space, CPU time, or data structures
- Actual physical destruction or alteration of network components
- Destruction of programming and files in a computer system
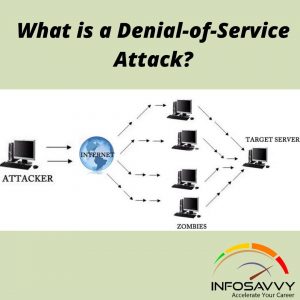
In general, Denial-of-Service Attack DoS attacks target network bandwidth or connectivity. Bandwidth attacks overflow the network with a high volume of traffic using existing network resources, thus depriving legitimate users of these resources, Connectivity attacks overflow a computer with a large number of connection requests, consuming all available resources of the OS so that the computer cannot process legitimate users’ requests.
Imagine a pizza delivery company, which does much of its business over the phone. If an attacker wanted to disrupt this business, he could figure out a way to tie up the company’s phone lines, making it impossible for the company to do business. That is how a DoS attack works—the attacker uses up all the ways to connect to the system, making legitimate business impossible, DoS attacks are a kind of security break that does not generally result in the theft of information. However, these attacks can harm the target in terms of time and resources. However, failure might mean the loss of a service such as email. In a worst-case scenario, a DOS attack can mean the accidental destruction of the files and programs of millions of people who happen to be surfing the Web at the time of attack.
A Distributed Denial of Service DDoS attack is a large-scale, coordinated attack on the availability of services on a victim’s system or network resources, launched indirectly through many compromised computers (botnets) on the Internet.
“The International Paralyzing of a Computer Network by flooding it with data sent simultaneously from many individual Computers”
As defined by the World Wide Web Security FAQ “A distributed denial-of-service (DDoS) attack uses many computers to launch a coordinated DoS attack against one or more targets. Using client/server technology, the perpetrator is able to multiply the effectiveness of the denial of service significantly by harnessing the resources of multiple unwitting accomplice computers, which serve as attack platforms,” The flood of incoming messages to the target system essentially forces it to shut down, thereby denying service to the legitimate users.
The services under attack are those of the “primary victim,” whereas the compromised systems used to launch the attack are the “secondary victims.” The use of secondary victims in performing a DDoS attack provides the attacker with the ability to wage a larger and more disruptive attack while making it more difficult to track down the original attacker.
The primary objective of any DDoS attacker is to first gain administrative access on as many systems as possible. In general, attackers use customized attack script to identify potentially vulnerable systems. Once the attacker gains access to the target systems, he or she will upload DDoS software and run it on these systems but not until the time chosen to launch the attack.
DDoS attacks have become popular because of the easy accessibility of exploit plans and the negligible amount of brain work required while executing them. These attacks can be very dangerous because they can quickly consume the largest hosts on the Internet, rendering them useless. The impact of DDoS includes loss of goodwill, disabled network, financial loss, and disabled organizations.
Related Product:- Certified Ethical Hacker | CEH Certification
How Distributed Denial-of-Service Attacks Work?
In a Distributed Denial of Service DDoS attack, many applications found the target browser or network with fake exterior requests that make the system, network, browser, or site slow, useless, and disabled or unavailable.
The attacker initiates the DDoS attack by sending a command to the zombie agents. These zombie agents send a connection request to a large number of reflector systems with the spoofed IP address of the victim. The reflector systems see these requests as coming from the victim’s machine instead of the zombie agents due to spoofing of source IP address. Hence, they send the requested information (response to connection request) to the victim. The victim’s machine is flooded with unsolicited responses from several reflector computers at once. This either may reduce the performance or may cause the victim’s machine to shut down completely.
Module Objectives
Denial-of-Service (DOS) and Distributed Denial-of-Service (DDoS) attacks became a serious threat to computer networks. These attacks attempt to make a machine or network resource unavailable to its authorized users. Usually, DoS/DDoS attacks exploit vulnerabilities within the implementation of TCP/IP model protocol or bugs in a specific OS.
This module starts with a summary of DoS and DDoS attacks. It provides an insight into different DoS/DDoS attack techniques. Later, it discusses about botnet network, DoS/DDoS attack tools, techniques to detect DoS/DDoS attacks, and DoS/DDoS countermeasures. The module ends with a summary of penetration testing steps an ethical hacker should follow to perform a security assessment of the target.
Also Read:- Types of attacks on a system
At the end of this module, you’ll be ready to perform the following:
- Describe the DoS/DDoS concepts
- Perform DoS/DDoS using various attack techniques
- Describe Botnets
- Describe DoS/DDoS case studies
- Explain different DoS/DDoS attack tools
- Apply best practices to mitigate DOS/DDOS attacks
- Perform DoS/DDoS penetration testing
Learn more about identity theft in CEH from Infosavvy.
“The first step toward change is awareness. The second step is acceptance”
-Nathaniel Branden
DDoS Case Study
DDoS may be a sophisticated and sophisticated attack supported DoS attack and multiple distributed attack sources in a DDoS attack, a large number of compromised computers (zombies) are involved to interrupt or suspend network services. This section deals with a DDoS case study.
DDoS Attack
In a DDoS attack, attackers use a group of compromised systems (bats or zombies) usually infected with Trojans to perform a DoS attack on a target system or network resource.
In the diagram above, an anonymous hacker hosts a HOIC DDoS attack tool on the webserver he/she owns or on the other compromised web server. The hacker then advertises the HOIC DDoS attack tool on the social networking sites or on search engines like Twitter, Facebook, and Google, providing a malicious download link thereto within the ad.
Users, who desire to perform the DDoS attack, may download the HOIC DDoS attack tool by clicking on the malicious link provided by the hacker. These users are termed “volunteers.” All the volunteers connect via IRC channel to the anonymous hacker and await their instructions to proceed further. The hacker instructs the volunteers to flood the target web server (e.g., PayPal, MasterCard, and PAYBACK) with multiple requests. On receiving their instructions, the volunteers take action accordingly, which results within the target server being overwhelmed. Thus, it’ll not respond to requests from even legitimate users.
Hackers Advertise Links to Download Botnet
Hackers advertise botnets on various blogs, search engines, social networking sites, emails, and so on providing download links for them. Hackers also use fake updates and security alerts to trick the victim to download the malware. The intension in doing so is to spread the botnet and increase the size of the attack network. This method of attack is extremely quick and effective.
Use of Mobile Devices as Botnets for Launching DDoS Attacks
Android devices are passively vulnerable to various malware like Trojans, buts, RATs, and so on, which are often found in third-party application stores. These unsecured android devices are becoming the primary targets for the attackers in order to enlarge their botnet network since they’re highly vulnerable to malware. Malicious android applications found in Google Play Store and drive-by download are just a few examples of methods of infection. The attacker binds the malicious APK server to the android application package (APK file), encrypts it, and removes unwanted features and permissions before distributing the malicious package to a third-party app store like Google Play Store. Once the victims are tricked to download and install such applications, the victim’s device will be taken over by the attacker, enslaving the targeted device into the attacker’s mobile botnet to perform malicious activities like launch DDoS attacks, web injections, and so on.
Dyn DDoS Attack
Dyn is an Internet Performance Management (IPM) company, which is believed to be a pioneer domain name system service provider. They also offer internet infrastructure services and products like monitoring and analytics, control, online infrastructure optimization, and email.
The Dyn attack, which happened on 21 October 2016, is one among the largest data breaches in history. This attack overturned a large portion of the internet within the United States and Europe and affected plenty of services. The source of the attack was the Mirai botnet. This botnet is unlike other botnets, consisting of loT devices like IF cameras, printers, and digital video recorders. The objective of a DoS attack is to deny or disrupt authorized users from accessing a resource or service.
According to Dyn, Mirai botnets have contributed to a serious volume of attack traffic. Mirai may be a piece of malware, which infects and exploits the vulnerable network devices on the internet, preferably loT devices. Upon successful infection, the bat gets registered to a C&C which controls the botnet during attacks, Mirai malware exploits those network devices that authenticate using default credentials.
-
Attack Timeline
The first attack was staged between approximately 11:10 UTC to 13:20 UTC. Initially, a huge inclination within the bandwidth consumption was witnessed at various locations of Dyn DNS infrastructure, which imitated a situation like that of a DDoS attack. The attack began to focus on the US-East region. This large volume of data originated from various source IP addresses and was destined for destination port 53, where the data packets were composed of TCP and UDP packets.
The next attack was performed between 15:50 UTC and 17:00 UTC. Unlike the previous attempt, this attack was targeting most the available Managed Infrastructures of Dyn around the globe. Though the second attempt consisted of same set of attack vectors and protocols used during the first attack, it still managed to disrupt the functionalities of the service provider despite the deployed incident response mechanism.
-
Attack Mechanism
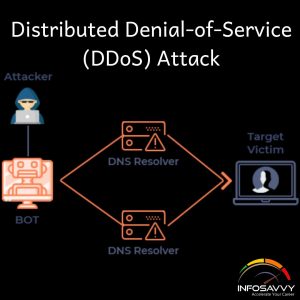
A DNS protocol was used to perform the DDoS attack on the DNS servers of the Dyn. The attack vectors used to perform ODDS attack include recursive DNS query mechanism or DNS Waterfall Torture, or authoritative DNS exhaustion attack. The architecture of DNS server infrastructure consists of Recursive DNS resolver and Authoritative DNS resolver. A recursive DNS resolver receives the DNS query from the bat to resolve a 12-digit pseudo-random host from the domain of the authoritative DNS resolver. It’s ensured that the recursive DNS resolver fails to resolve the DNS record of the random host, in order that the query gets forwarded to the authoritative resolver, as seen within the figure above.
This mechanism removes the protection of the caching layer from authoritative DNS resolvers. The aim of this attack vector is to forward an exceptionally large amount of DNS queries to the authoritative DNS resolver and exhaust the capacity of authoritative DNS resolver to resolve queries.
Impact
This DDoS attack affected the anycast servers of Dyn. It also prevented the services for resolving legitimate DNS queries. It is estimated to have generated more than 40 to 50 times the normal traffic volume, and the expected number of involved botnets during the attack amounts to 100,000. According to a few reports, the total volume of data involved during this attack is estimated to be 1.2 Tbps. A few major US websites including PayPal, Spotify, Twitter, and Amazon faced connectivity issues. The various other web services of companies such as BankWest, HSBC, and Ticketmaster were also affected. According to BitSight, approximately 8% of the Dyn DNS customer base terminated their contract after the attack.
Questions related to this topic
- How are DDoS attacks carried?
- Is DDoS illegal?
- What is an example of a DDoS attack?
- Can DDoS attacks steal information?
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Foot printing Penetration Testing
- Different types of tools with Email Foot printing
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Foot printing tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grapping
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com
https://g.co/kgs/ttqPpZ



