Robin, a professional hacker, targeted an organization’s network to sniff all the traffic. During this process, Robin plugged in a rough switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network. What is the attack performed by Robin in above scenario?
Option 1 : ARP spoofing attack
Option 2 : VLAN hopping attack
Option 3 : DNS poisoning attack
Option 4 : STP attack
1. ARP spoofing attack
ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. Once the attacker’s MAC address is connected to an authentic IP address, the attacker will begin receiving any data that is intended for that IP address. ARP spoofing can enable malicious parties to intercept, modify or even stop data in-transit. ARP spoofing attacks can only occur on local area networks that utilize the Address Resolution Protocol.
The effects of ARP spoofing attacks can have serious implications for enterprises. In their most basic application, ARP spoofing attacks are used to steal sensitive information. Beyond this, ARP spoofing attacks are often used to facilitate other attacks such as:
- Denial-of-service attacks: DoS attacks often leverage ARP spoofing to link multiple IP addresses with a single target’s MAC address. As a result, traffic that is intended for many different IP addresses will be redirected to the target’s MAC address, overloading the target with traffic.
- Session hijacking: Session hijacking attacks can use ARP spoofing to steal session IDs, granting attackers access to private systems and data.
- Man-in-the-middle attacks: MITM attacks can rely on ARP spoofing to intercept and modify traffic between victims.
2. VLAN hopping attack
VLAN Hopping is an attack where the attacker is able to send traffic from one VLAN into another. There are two different methods to accomplish this:
- Double tags: the idea behind the attack is that the attacker is connected to an interface in access mode with the same VLAN as the native untagged VLAN on the trunk. The attacker sends a frame with two 802.1Q tags, the “inner” VLAN tag is the VLAN that we want to reach and the “outer” VLAN tag is the native VLAN. When the switch receives the frame, it will remove the first (native VLAN) 802.1Q tag and forwards the frame with the second 802.1Q tag on its trunk interface(s). The attacker has now “jumped” from the native VLAN to the victim’s VLAN.It’s a one way trip but it could be used perhaps for a DOS attack.
- Switch spoofing: the attacker will send DTP packets and tries to negotiate a trunk with the switch, this is possible when you use the default “dynamic auto” or “dynamic desirable” switchport mode. Once you have a trunk to your computer, you will have access to all VLANs. This is basically a misconfiguration since you should never configure your interfaces to use the dynamic switchport modes.
Here’s an illustration for the double tag method:
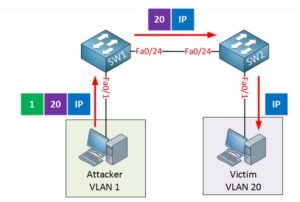
In the picture above we have two switches, SW1 and SW2. The attacker is in VLAN 1 and our victim is in VLAN 20. Here are the configurations of the switches:
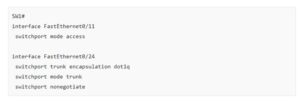
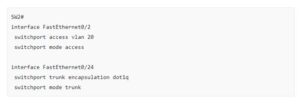
As you can see above the interfaces that connect to the computers are in access mode, the attacker is in VLAN 1 while our victim is in VLAN 20. The interface between the two switches is a 802.1Q trunk.
Does the double tagging method actually work? The idea is that the switch will just accept any frames even if it’s in access mode. I tried this on a Cisco Catalyst Switch 3560 running the IP services 12.2(55)SE10 image.
To test this, I used scapy on a computer running Kali:
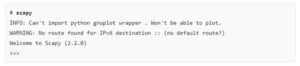
Let’s craft a nice frame:

Here’s what you see above:
- Source MAC address: 00:17:5a:ed:7a:f0
- Destination MAC address: broadcast
- Inner VLAN tag 20
- Outer VLAN tag 1
- Destination IP address: broadcast
- Source IP address: 192.168.1.1
- Outgoing interface: eth2
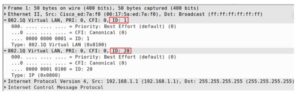
Here’s a capture of this packet in wireshark:
3. DNS poisoning attack
Domain Name Server (DNS) spoofing (a.k.a. DNS cache poisoning) is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination.
Once there, users are prompted to login into (what they believe to be) their account, giving the perpetrator the opportunity to steal their access credentials and other types of sensitive information. Furthermore, the malicious website is often used to install worms or viruses on a user’s computer, giving the perpetrator long-term access to it and the data it stores.
Methods for executing a DNS spoofing attack include:
- Man in the middle (MITM)– The interception of communications between users and a DNS server in order to route users to a different/malicious IP address.
- DNS server compromise– The direct hijacking of a DNS server, which is configured to return a malicious IP address.
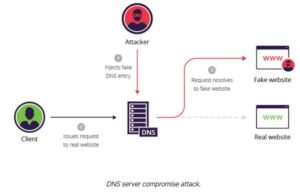
DNS cache poisoning example
The following example illustrates a DNS cache poisoning attack, in which an attacker (IP 192.168.3.300) intercepts a communication channel between a client (IP 192.168.1.100) and a server computer belonging to the website www.estores.com (IP 192.168.2.200).
In this scenario, a tool (e.g., arpspoof) is used to dupe the client into thinking that the server IP is 192.168.3.300. At the same time, the server is made to think that the client’s IP is also 192.168.3.300.
Such a scenario would proceed as follows:
- The attacker uses arpspoof to issue the command: arpspoof 192.168.1.100 192.168.2.200. This modifies the MAC addresses in the server’s ARP table, causing it to think that the attacker’s computer belongs to the client.
- The attacker once again uses arpspoof to issue the command: arpspoof 192.168.2.200 192.168.1.100, which tells the client that the perpetrator’s computer is the server.
- The attacker issues the Linux command: echo 1> /proc/sys/net/ipv4/ip_forward. As a result, IP packets sent between the client and server are forwarded to the perpetrator’s computer.
- The host file, 192.168.3.300 estores.com is created on the attacker’s local computer, which maps the website www.estores.com to their local IP.
- The perpetrator sets up a web server on the local computer’s IP and creates a fake website made to resemble www.estores.com.
- Finally, a tool (e.g., dnsspoof) is used to direct all DNS requests to the perpetrator’s local host file. The fake website is displayed to users as a result and, only by interacting with the site, malware is installed on their computers.
4. STP attack
STP prevents bridging loops in a redundant switched network environment. By avoiding loops, you can ensure that broadcast traffic does not become a traffic storm.
STP is a hierarchical tree-like topology with a “root” switch at the top. A switch is elected as root based on the lowest configured priority of any switch (0 through 65,535). When a switch boots up, it begins a process of identifying other switches and determining the root bridge. After a root bridge is elected, the topology is established from its perspective of the connectivity. The switches determine the path to the root bridge, and all redundant paths are blocked. STP sends configuration and topology change notifications and acknowledgments (TCN/TCA) using bridge protocol data units (BPDU).
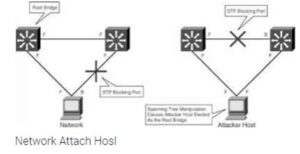
An STP attack involves an attacker spoofing the root bridge in the topology. The attacker broadcasts out an STP configuration/topology change BPDU in an attempt to force an STP recalculation. The BPDU sent out announces that the attacker’s system has a lower bridge priority. The attacker can then see a variety of frames forwarded from other switches to it. STP recalculation may also cause a denial-of-service (DoS) condition on the network by causing an interruption of 30 to 45 seconds each time the root bridge changes. An attacker using STP network topology changes to force its host to be elected as the root bridge.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



