Robin, an attacker, is attempting to bypass the firewalls of an organization through the DNS tunneling method in order to exfiltrate data. He is using the NSTX tool for bypassing the firewall.
On which of the following ports should Robin run the NSTX tool?
Option 1 : Port 53
Option 2 : Port 80
Option 3 : Port 50
Option 4 : Port 23
1. Port 53
DNS uses Ports 53 which is almost always open on systems, firewalls, and clients to transmit DNS queries. instead of the more familiar Transmission Control Protocol (TCP) these queries use User Datagram Protocol (UDP) due to its low-latency, bandwidth and resource usage compared TCP-equivalent queries. UDP has no error or flow-control capabilities, nor does it have any integrity checking to make sure the info arrived intact.
How is internet use (browsing, apps, chat etc) so reliable then? If the UDP DNS query fails (it’s a best-effort protocol after all) within the first instance, most systems will retry variety of times and only after multiple failures, potentially switch to TCP before trying again; TCP is additionally used if the DNS query exceeds the restrictions of the UDP datagram size – typically 512 bytes for DNS but can depend upon system settings.
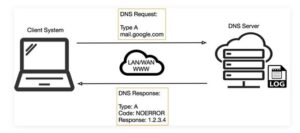
Figure 1 below illustrates the essential process of how DNS operates: the client sends a question string (for example, mail.google[.]com during this case) with a particular type – typically A for a number address. I’ve skipped the part whereby intermediate DNS systems may need to establish where ‘.com’ exists, before checking out where ‘google[.]com’ are often found, and so on.
Many worms and scanners are created to seek out and exploit systems running telnet. Given these facts, it’s really no surprise that telnet is usually seen on the highest Ten Target Ports list. Several of the vulnerabilities of telnet are fixed. They require only an upgrade to the foremost current version of the telnet Daemon or OS upgrade. As is usually the case, this upgrade has not been performed on variety of devices. this might flow from to the very fact that a lot of systems administrators and users don’t fully understand the risks involved using telnet. Unfortunately, the sole solution for a few of telnets vulnerabilities is to completely discontinue its use. the well-liked method of mitigating all of telnets vulnerabilities is replacing it with alternate protocols like ssh. Ssh is capable of providing many of an equivalent functions as telnet and a number of other additional services typical handled by other protocols like FTP and Xwindows. Ssh does still have several drawbacks to beat before it can completely replace telnet. it’s typically only supported on newer equipment. It requires processor and memory resources to perform the info encryption and decryption. It also requires greater bandwidth than telnet thanks to the encryption of the info . This paper was written to assist clarify how dangerous the utilization of telnet are often and to supply solutions to alleviate the main known threats so as to enhance the general security of the web
Once a reputation is resolved to an IP caching also helps: the resolved name-to-IP is usually cached on the local system (and possibly on intermediate DNS servers) for a period of your time . Subsequent queries for an equivalent name from an equivalent client then don’t leave the local system until said cache expires. Of course, once the IP address of the remote service is understood , applications can use that information to enable other TCP-based protocols, like HTTP, to try to to their actual work, for instance ensuring internet cat GIFs are often reliably shared together with your colleagues.
So, beat all, a couple of dozen extra UDP DNS queries from an organization’s network would be fairly inconspicuous and will leave a malicious payload to beacon bent an adversary; commands could even be received to the requesting application for processing with little difficulty.
2. Port 80
The number that identifies Internet packets as Web transactions (HTTP transactions). All ports numbers reside within the header of the packets, and requests that are marked port 80 are processed by the online server (see TCP/IP port). Port 80 requests may activate any number of various server-side processes before an internet page or another file is returned to the user.
Port 80 represents the non-secure HTTP protocol, while port 443 is HTTPS, the secure version. Increasingly, internet sites are configured for HTTPS. For an inventory of common port numbers, see well-known port. See ports forwarding, HTTP and HTTPS.
In a PC, port 80h is an input/output address that’s wont to send power-on codes. See POST code and PC I/O addressing.
3. Port 50
TCP port 50 uses the Transmission Control Protocol. TCP is one among the most protocols in TCP/IP networks. TCP may be a connection-oriented protocol, it requires handshaking to line up end-to-end communications. only a connection is about up user’s data are often sent bi-directionally over the connection.
Attention! TCP guarantees delivery of knowledge packets on port 50 within the same order during which they were sent. Guaranteed communication over TCP port 50 is that the main difference between TCP and UDP. UDP port 50 wouldn’t have guaranteed communication as TCP.
UDP on port 50 provides an unreliable service and datagrams may arrive duplicated, out of order, or missing all of sudden . UDP on port 50 thinks that error checking and correction isn’t necessary or performed within the application, avoiding the overhead of such processing at the network interface level.
UDP (User Datagram Protocol) may be a minimal message-oriented Transport Layer protocol (protocol is documented in IETF RFC 768).
Application examples that always use UDP: voice IP (VoIP), streaming media and real-time multiplayer games. Many web applications use UDP, e.g. the name System (DNS), the Routing Information Protocol (RIP), the Dynamic Host Configuration Protocol (DHCP), the straightforward Network Management Protocol (SNMP).
4. Port 23
TCP port 23 may be a frequent member of the incidents.org Top Ten Target Ports list1 . Incidents.org (or dshield.org) collects intrusion detection data from the Intrusion Detection Systems of volunteer’s round the globe. This information is consolidated to make reports of the highest ports attacked and therefore the top attackers. These reports are posted on the dshield website. graph from the incidents.org website outlining the activity logs for April 25th 2002. On today TCP port 23 is shown because the forth most ordinarily scanned ports on the web . breakdown of activity on port 23 for the month of April. Port 23 is usually employed by the Telnet protocol. Telnet commonly provides remote access to a spread of communications systems. Telnet is additionally often used for remote maintenance of the many networking communications devices including routers and switches. Unlike many other common protocols, like HTTP or FTP, telnet often provides access to a foreign system with administrator privileges. Given access to a server, or a network router of a company network or ISP, an attacker can perform an excellent deal of mischief. the extent of access provided by telnet makes it a valuable commodity for people attempting to realize unauthorized access to systems or networks. This makes port 23 a really common target of attackers during network scans and reconnaissance attempts. Over the previous couple of years, several vulnerabilities are discovered that effect telnet. These vulnerabilities haven’t been limited to one implementation of the telnet daemon or one OS . Unix, Microsoft, BSD, Cisco routers and most other equipment with a telnet daemon installed are subject to vulnerabilities. Many systems are installed or delivered from the factory with telnet enabled by default. Several vendors even set the passwords to a default setting.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



