Susan, a software developer, wants her web API to update other applications with the latest information. For this purpose, she a user-defined HTTP callback or push APIs that are raised based on trigger events; when invoked, this feature supplies data to other applications so that users can instantly receive real-time information. Which of the following techniques is employed by Susan?
Option 1 : RESET API
Option 2 : SOAP API
Option 3 : Web shells
Option 4 : Webhooks
1. RESET API
One of the most popular types of API is REST or, as they’re sometimes known, restful apis. REST or restful apis were designed to take advantage of existing protocols. while REST – or representational State Transfer – can be used over nearly any protocol, once used for net apis it usually takes advantage of http. this means that developers have no need to install additional software or libraries once additional a REST API.
One of the key advantages of REST apis is that they provide a great deal of flexibility. knowledge isn’t tied to resources or ways, thus REST will handle multiple kinds of calls, come back different data formats and even change structurally with the proper implementation of hypermedia. This flexibility allows developers to make an API that meets your wants diverse diverse meeting the wants of while numerous customers.
There are six key constraints to think about once considering whether a relaxing API is that the right style of API for your needs:
- Client-Server: This constraint operates on the idea that the client and the server should be separate from each other and allowed to evolve individually.
- Stateless: REST apis are stateless, meaning that calls can be made severally of one another, and each call contains all of the info necessary to complete itself successfully.
- Cache: because a stateless API will increase request overhead by handling massive different incoming and outward-bound calls, a REST API should be designed to encourage the storage of cacheable data.
- Uniform Interface: The key to the decoupling client from server is having a uniform interface that allows freelance evolution of the application while not having the application’s services, or models and actions, tightly coupled to the API layer itself.
- Layered System: REST APIs have different layers of their architecture working together to build a hierarchy that helps create a more scalable and modular application.
- Code on Demand: Code on Demand allows for code or applets to be transmitted via the API for use among the application.
Unlike SOAP, REST isn’t constrained to XML, but instead will come back XML, JSON, YAML or the other format counting on what the client requests. and unlike RPC, users aren’t required to grasp procedure names or specific parameters in a specific order.
One of the disadvantages of restful Apis is that you will lose the ability to maintain state in REST, like among sessions. It may also be tougher for newer developers to use.
It’s important to understand what makes a REST API restful, and why these constraints exist before building your API.
2. SOAP API
SOAP is a very important protocol that helped introduce the widespread use of web Services, also called apis. based on XML, the SOAP protocol is still in wide usage. many organizations use the more flexible REST API pattern, control others like the structure, datatype management, and control standard of SOAP.
This guide will cover an introduction to SOAP apis, including the way to decision them, how to describe them, and other common topics that will help you perceive the basics of the protocol’s history and place within web Service apis.
What is SOAP
SOAP is the simple Object Access Protocol, a messaging standard outlined by the world Wide net consortium and its member editors. SOAP uses consortium XML data format to declare its request and response messages, relying on XML Schema and other technologies to enforce the structure of its payloads.
Both public and private Application Programming Interfaces (APIs) use SOAP as an interface. while more common in giant enterprises, organizations of all sizes produce and consume SOAP apis.
SOAP is uses the Remote Procedure call (RPC) pattern, where functions or methods ar passed parameters and return a result. many RPC solutions prior to SOAP were dependent on specific programming languages or technology stacks. as an example, previous RPC implementations usually needed each side of the RPC to use the C programming language, that predates the modern web. Even an Internet-era language, Java, has its own RPC model called Remote methodology Invocation (RMI), that originally was tightly as well as the Java Virtual Machine (JVM).
Among the important aspects of SOAP apis are their independence from programming language and even underlying transport protocol. The sender will use C#, as an example, whereas the recipient’s stack depends on Java. whereas these more enterprise-oriented languages ar most typical with SOAP, there ar SOAP implementations in Python, Ruby, and all trendy programming languages.
A final advantage to SOAP is its extensibility. As a standard, its specification is deliberately limited on constraints. As such, the extensibility model at intervals the SOAP specification provides for customization.
How to decision a SOAP API
In order to decision a SOAP API, you’ll most likely got to include a SOAP library together with your programming language. though it’s possible to form SOAP API calls while not SOAP libraries, it’s a lot of efficient to work with an abstraction rather than crafting the messages yourself. The SOAP messages are verbose, chiefly due to reliance on XML.
3. Web shells
A web shell is a malicious script utilized by an attacker with the intent to escalate and maintain persistent access on an already compromised web application. a web shell itself cannot attack or exploit an vulnerability, so it’s forever the second step of associate degree attack (this stage an stated as post-exploitation).
An attacker will take advantage of common web page vulnerabilities like SQL injection, remote file inclusion (RFI), or even use cross-site scripting (XSS) as part of a social engineering attack in order to attain file transfer capabilities and transfer the malicious files. The common functionality includes however is not limited to shell command execution (access to cmd/command line), code execution, database enumeration, and file management.
Web shells could be written in several internet languages, for example, PHP web shells are very common. they will have an effect on you no matter whether your system relies on custom computer code or on a common content management system like WordPress with plugins. web shells might also not get detected by antivirus or anti-malware software because they do not use typical executable file types. At the same time, they’re easily available to the public, for instance, via many GitHub projects.
In this short series, we want to explain to you in detail how web shells work (using associate degree example of a PHP shell) and the way you can detect web shells and defend your assets.
Persistent Remote Access
A web shell script usually contains a backdoor, that allows an attacker to remotely access and possibly control an Internet-facing server at any time. this would save the assailant the inconvenience of having to exploit a vulnerability whenever that access to the compromised server is required.
An attacker might also choose to fix the vulnerability themselves so as no one that nobody else can exploit that vulnerability. this way the attacker will keep a low profile an avoid any interaction with an administrator, whereas still getting a similar result.
It is also value mentioning that many in style internet shells use watchword authentication and other techniques to confirm that solely the attacker uploading the online shell has access to that. Such techniques embody locking down the script to a particular custom protocol header, specific cookie values, specific ip addresses, or a mix of those techniques. Most internet shells conjointly contain code to spot and block search engines from listing the shell and, as a consequence, blacklisting the whole domain or server that the online application is hosted on – in alternative words, obfuscation and hiding are key.
Privilege Escalation
Unless a server is misconfigured, the web shell will be running with web server software user permissions, which are (or, at least, should be) limited. Using a web shell, an attacker can attempt to perform privilege escalation attacks by exploiting local vulnerabilities on the system in order to assume root privileges, which, in Linux and other UNIX-based operating systems is the superuser.
With access to the root account, the attacker will essentially do something on the system as well as managing native files, installing computer code, dynamic permissions, adding and removing users, stealing passwords, reading emails and more.
Pivoting and Launching Attacks
A web shell are often used for pivoting within or outside a network. The attacker might want to watch (sniff) the network traffic on the system, scan the internal network to find live hosts and enumerate firewalls and routers within the network.
This method will take days, even months, predominantly as a result of an assailant usually seeks to stay a low profile and draw quantity} amount of attention doable. Once associate degree assailant has persistent access, they will with patience create their moves.
The compromised system can even be accustomed attack or scan targets that reside outside the network. This adds an extra layer of anonymity for the attacker since they’re employing a third party system to launch associate degree attack. A step any would be to pivot (tunnel) through multiple systems to create it virtually not possible to trace an attack back to its supply.
Zombie
Another use of internet shells is to create servers a part of a botnet. A botnet could be a network of compromised systems that an attacker would management, either to use themselves or to lease to other criminals. the online shell or backdoor is connected to a command and management (C&C) server from that it will take commands on what instructions to execute.
This setup is often utilized in distributed denial of service (DDoS) attacks, that need expansive amounts of bandwidth. during this case, the attacker doesn’t have any interest in harming or stealing something from the system upon that the online shell was deployed. Instead, they will simply use its resources.
4. Webhooks
Webhooks are one of a few ways internet applications will communicate with one another.
It allows you to send real-time data from one application to another whenever a given event happens.
For example, let’s say you’ve created an application using the Foursquare API that tracks when people check into your restaurant. You ideally wish to be able to greet customers by name and provide a complimentary drink when they check in.
What a webhook will is notify you any time someone checks in, therefore you’d be able to run any processes that you simply had in your application once this event is triggered.
The data is then sent over the web from the application wherever the event originally occurred, to the receiving application that handles the data.
Here’s a visual representation of what that looks like:
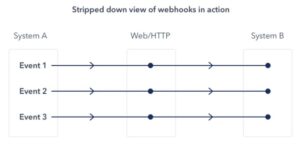
A webhook url is provided by the receiving application, and acts as a phone number that the other application will call once an event happens.
Only it’s more complicated than a phone number, because data about the event is shipped to the webhook url in either JSON or XML format. this is known as the “payload.”
Here’s an example of what a webhook url looks like with the payload it’s carrying:

Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



