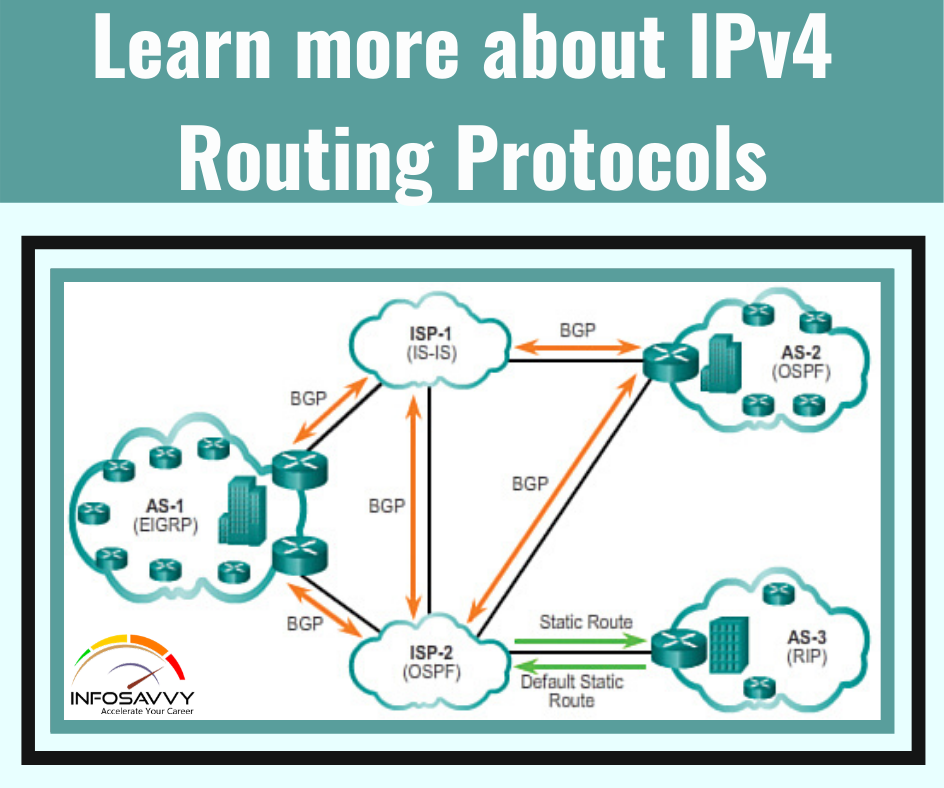
Learn about IPv4 Routing Protocols
Learn about IPv4 Routing Protocols in this the routing (forwarding) process depends heavily on having an accurate and up-to-date IP routing table on each router. This section takes another check out routing protocols, considering the goals of a routing protocol, the methods routing protocols use to teach and learn routes, and an example. First, consider the goals of a routing protocol, no matter how the routing protocol works: To dynamically learn and fill the routing …