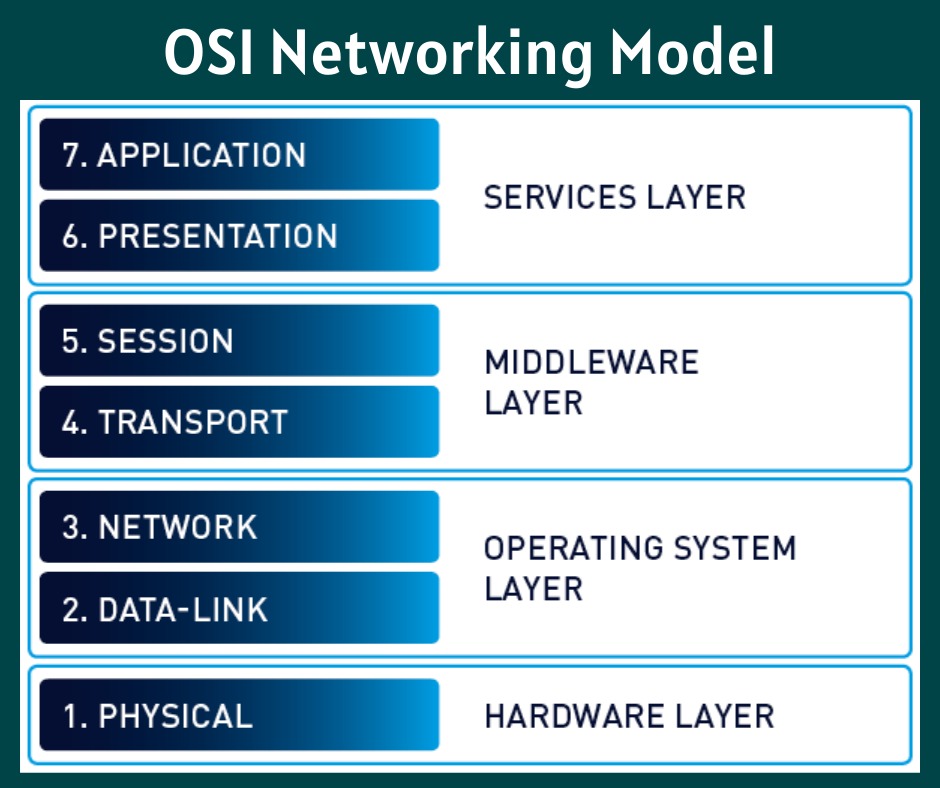
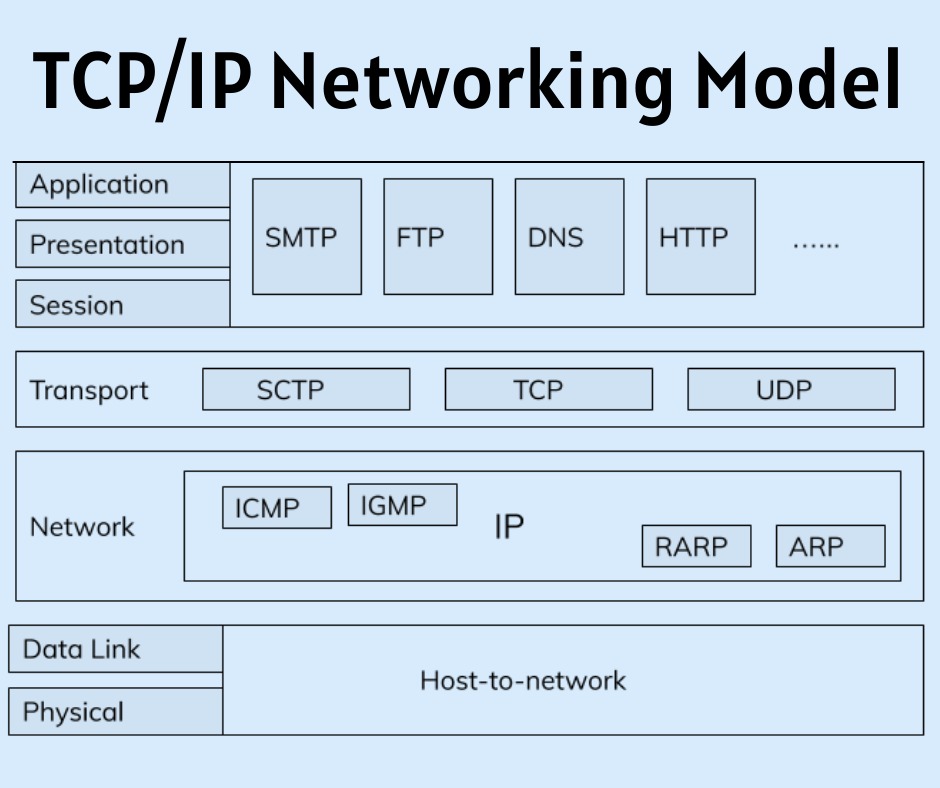
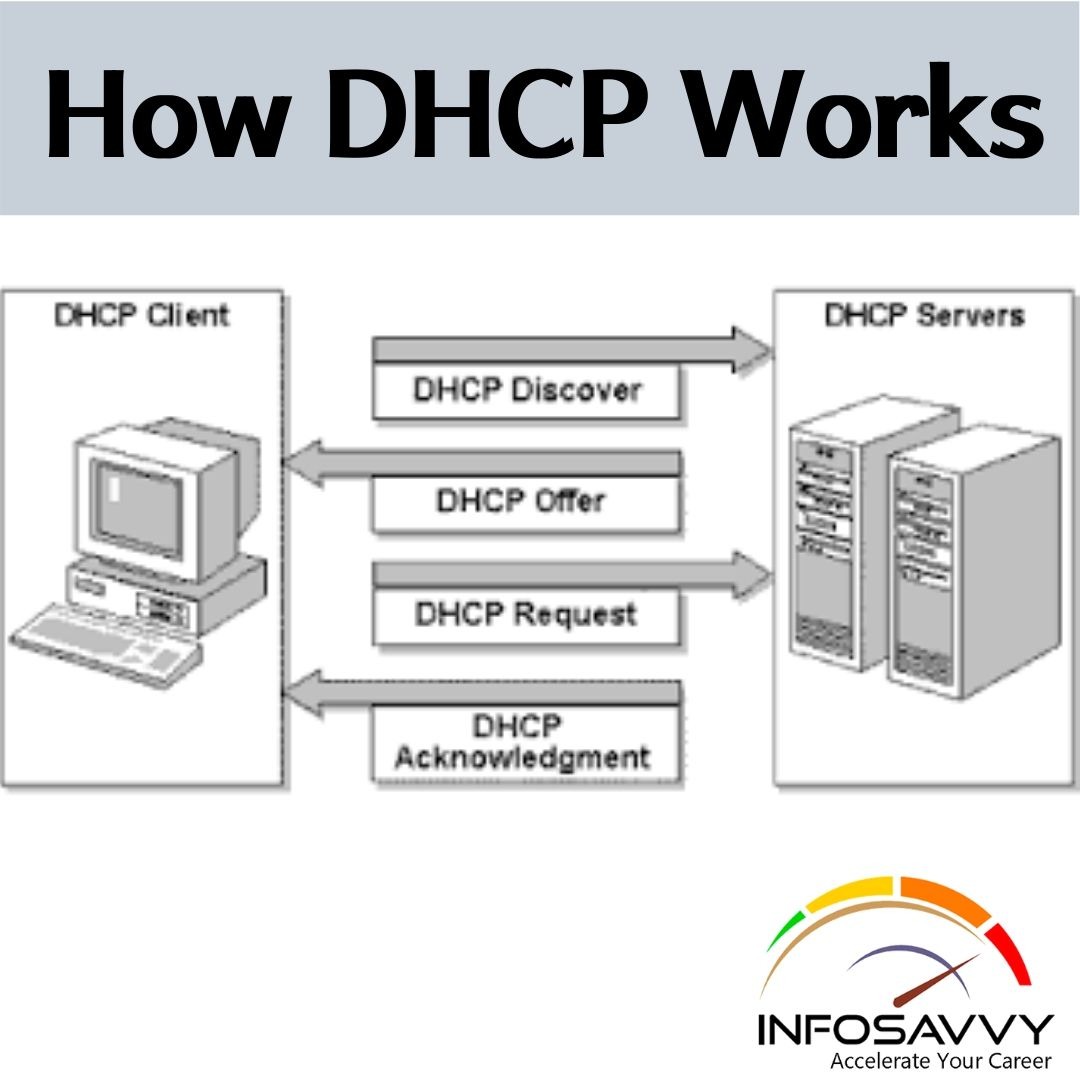
Introduction of OSI Networking Model
Introduction of OSI Networking Model this blog is written on OSI Networking Model with it’s layer description as well as function and compared OSI with TCP/IP model. OSI Networking Model At one point within the history of the OSI model, many of us thought that OSI would win the battle of the networking models discussed earlier. If that had occurred, rather than running TCP/IP on every computer within the world, those computers would be running …