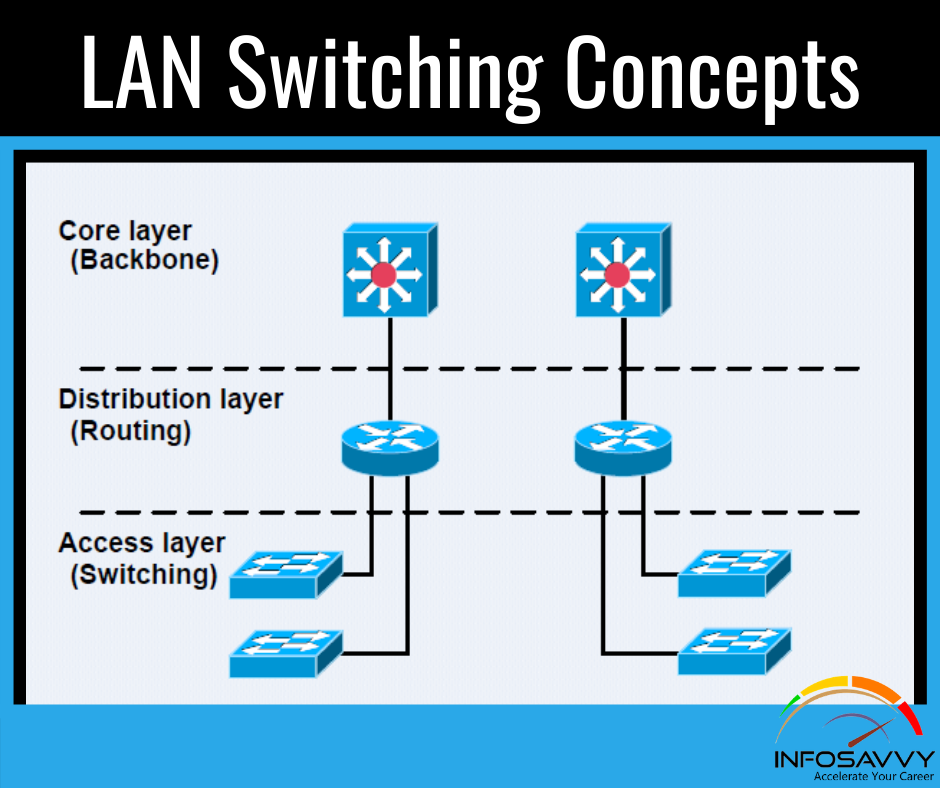
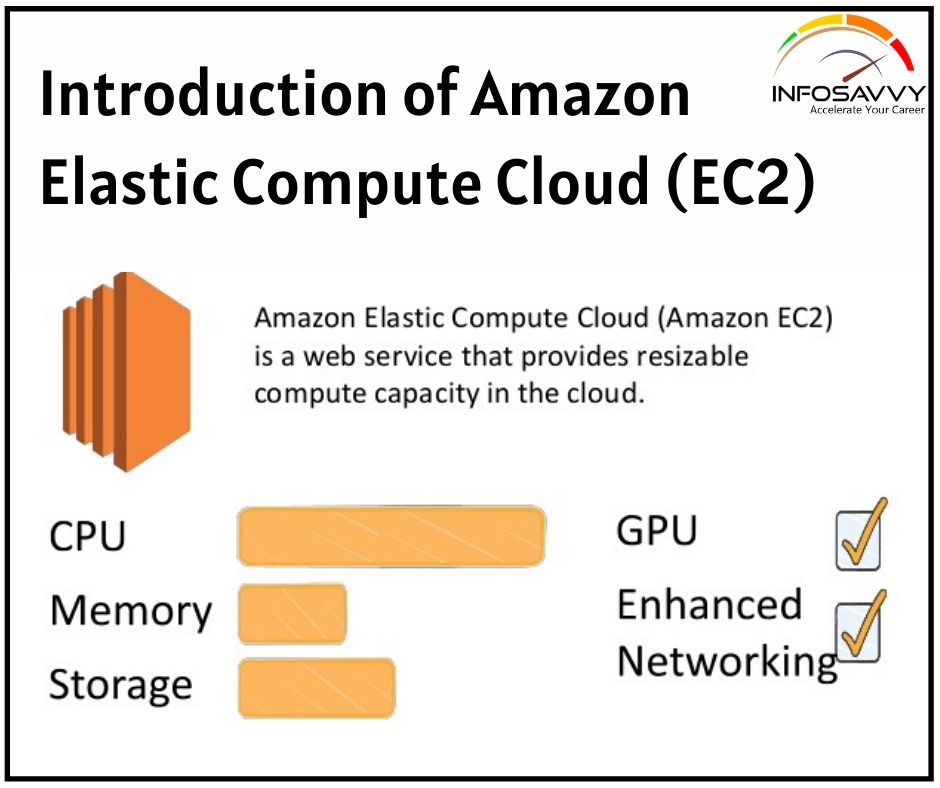
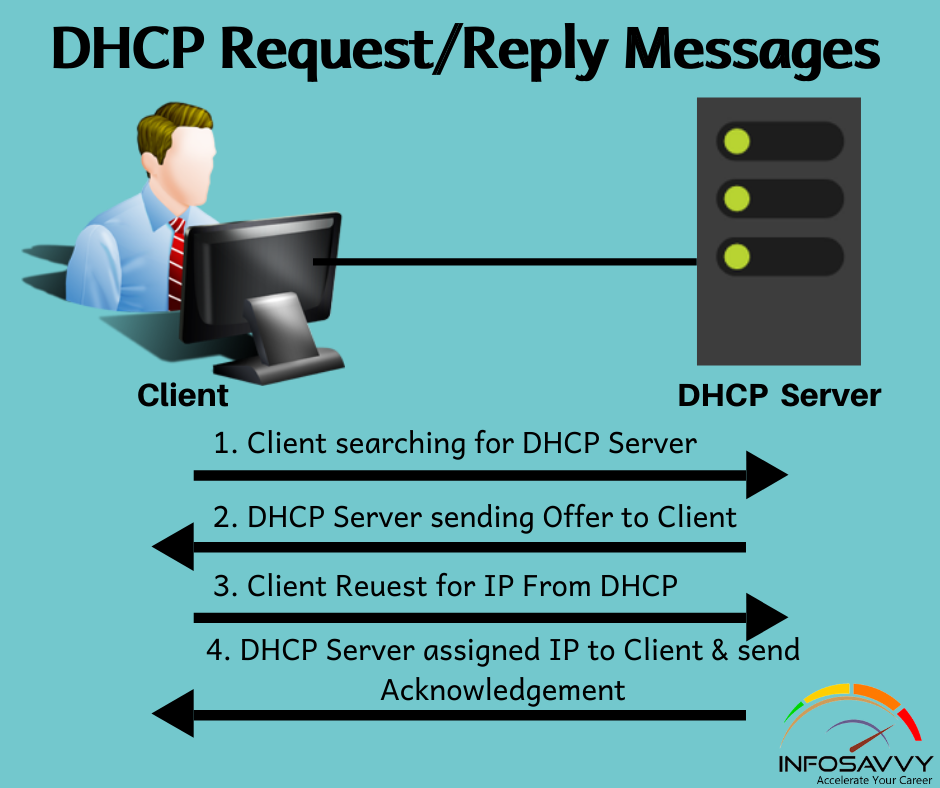
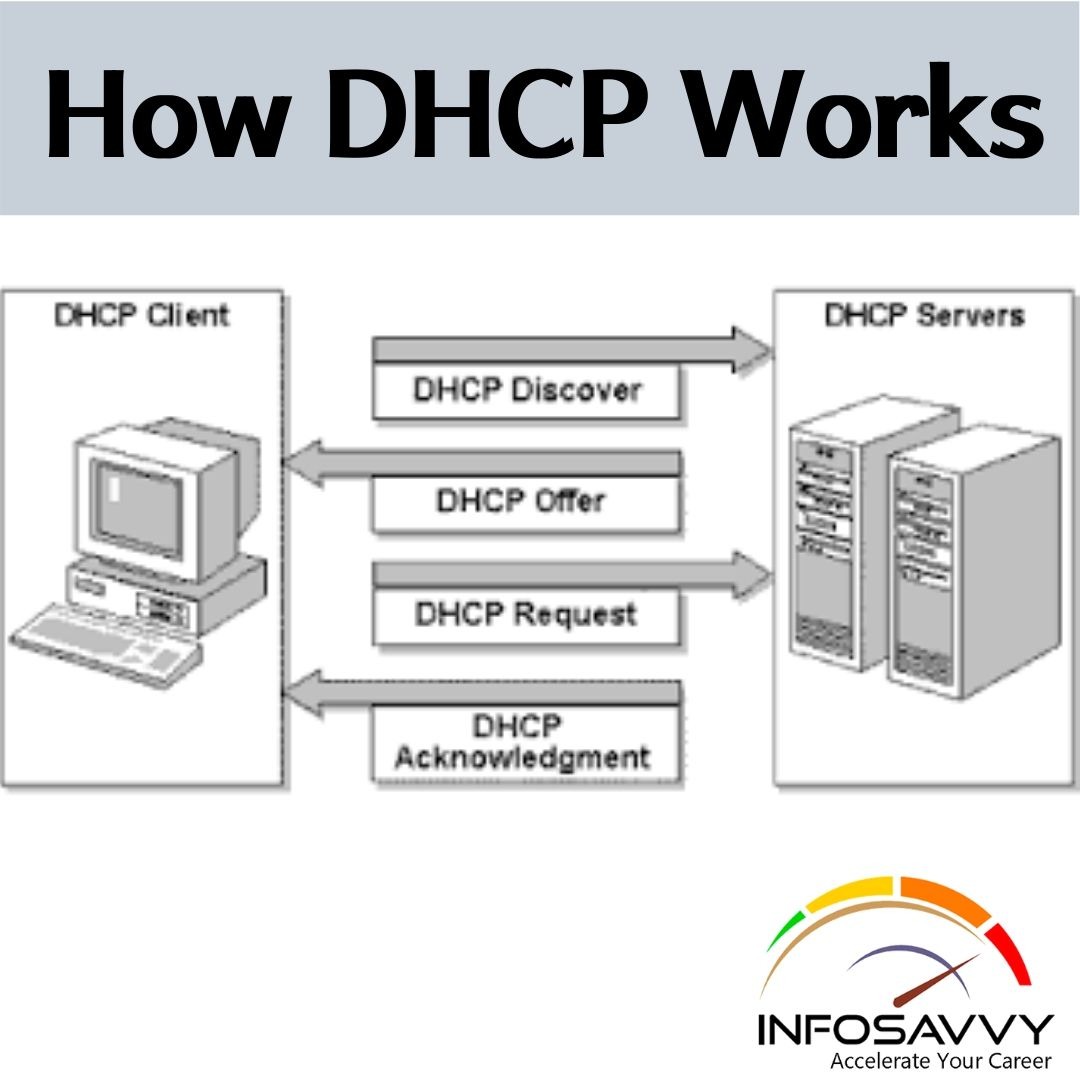
Perform MSSQL Forensics
Perform MSSQL Forensics in this SQL server is a Relational Database Management System and is being widely adopted by various organizations to store data associated with the applications. This includes sensitive data related to the web application and users’ accounts in the web application. MSSQL forensics take action when a security incident has occurred and detection and analysis of the malicious activities performed by criminals over the SQL database file are required. A forensic investigator …