For thousands of years, people have sought assurance that information has been captured, stored, communicated, and used securely. Depending on the context, differing levels of emphasis have been placed on the availability, integrity, and confidentiality of information, but achieving these basic objectives has always been at the heart of security practice. As we moved from the time of mud tablets and papyrus scrolls into the digital era, we watched the evolution of technology to support these three objectives. In today’s world, where vast amounts of information are accessible at the click of a mouse, our security decision-making must still consider the people, processes, and systems that assure us that information is available when we need it, has not been altered, and is protected from disclosure to those not entitled to it. This module will explore the implications of confidentiality, integrity, and availability (collectively, the CIA Triad) in current security practices. These interdependent concepts form a useful and important framework on which to base the study of information security practice.
Information Security
Information security processes, practices, and technologies can be evaluated based on how they impact the confidentiality, integrity, and availability of the information being communicated. The apparent simplicity of the CIA Triad drives a host of security principles, which translate into practices and are implemented with various technologies against a dizzying array of information sources (see Figure 1.1). Thus, a common understanding of the meaning of each of the elements in the triad allows security professionals to communicate effectively.
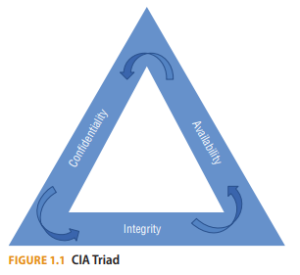
Confidentiality
Ensuring that information is provided to only those people who are entitled to access that information has been one of the core challenges in effective communications. Confidentiality implies that access is limited. Controls need to be identified that separate those who need to know information from those who do not. Once we have identified those with legitimate need, then we will apply controls to enforce their privilege to access the information. Applying the principle of least privilege ensures that individuals have only the minimum means to access the information to which they are entitled.
Information about individuals is often characterized as having higher sensitivity to disclosure. The inappropriate disclosure of other types of information may also have adverse impacts on an organization’s operations. These impacts may include statutory or regulatory noncompliance, loss of unique intellectual property, financial penalties, or the loss of trust in the ability of the organization to act with due care for the information.
Integrity
To make good decisions requires acting on valid and accurate information. Change to information may occur inadvertently, or it may be the result of intentional acts. Ensuring the information has not been inappropriately changed requires the application of control over the creation, transmission, presentation, and storage of the information. Detection of inappropriate change is one way to support higher levels of information integrity. Many mechanisms exist to detect change in information; cryptographic hashing, reference data, and logging are only some of the means by which detection of change can occur. Other controls ensure the information has sufficient quality to be relied upon for decisions. Executing well-formed transactions against constrained data items ensures the system maintains integrity as information is captured. Controls that address separation of duties, application of least privilege, and audit against standards also support the validity aspect of data integrity.
Related Product : EC-Council Certified Incident Handler | ECIH v2
Availability
Availability ensures that the information is accessible when it is needed. Many circumstances can disrupt information availability. Physical destruction of the information, disruption of the communications path, and inappropriate application of access controls are only a few of the ways availability can be compromised.
Availability controls must address people, processes, and systems. High availability systems such as provided by cloud computing or clustering are of little value if the people necessary to perform the tasks for the organization are unavailable. The challenge for the information security architect is to identify those single points of failure in a system and apply a sufficient amount of control to satisfy the organization’s risk appetite.
Taken together, the CIA Triad provides a structure for characterizing the information security implications of a concept, technology, or process. It is infrequent, however, that such a characterization would have implications on only one side of the triad. For example, applying cryptographic protections over information may indeed ensure the confidentiality of information and, depending on the cryptographic approach, support higher levels of integrity, but the loss of the keys to those who are entitled to the information would certainly have an availability implication!
Limitations of the CIA Triad
The CIA Triad evolved out of theoretical work done in the mid-1960s. Precisely because of its simplicity, the rise of distributed systems and a vast number of new applications for new technology has caused researchers and security practitioners to extend the triad’s coverage. Guaranteeing the identities of parties involved in communications is essential to confidentiality. The CIA Triad does not directly address the issues of authenticity and nonrepudiation, but the point of nonrepudiation is that neither party can deny that they participated in the communication. This extension of the triad uniquely addresses aspects of confidentiality and integrity that were never considered in the early theoretical work.
The National Institute of Standards and Technology (NIST) Special Publication 800-33,“Underlying Technical Models for Information Technology Security,” included the CIA Triad as three of its five security objectives, but added the concepts of accountability (that actions of an entity may be traced uniquely to that entity) and assurance (the basis for confidence that the security measures, both technical and operational, work as intended to protect the system and the information it processes). The NIST work remains influential as an effort to codify best-practice approaches to systems security.
Perhaps the most widely accepted extension to the CIA Triad was proposed by information security pioneer Donn B. Parker. In extending the triad, Parker incorporated three additional concepts into the model, arguing that these concepts were both atomic (could not be further broken down conceptually) and nonoverlapping. This framework
has come to be known as the Parkerian Hexad (see Figure 1.2). The Parkerian Hexad contains the following concepts:
- Confidentiality: The limits on who has access to information
- Integrity: Whether the information is in its intended state
- Availability: Whether the information can be accessed in a timely manner
- Authenticity: The proper attribution of the person who created the information
- Utility: The usefulness of the information
- Possession or control: The physical state where the information is maintained

Subsequent academic work produced dozens of other information security models, all aimed at the same fundamental issue-how to characterize information security risks. For the security professional, a solid understanding of the CIA Triad is essential when communicating about information security practice.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


