Scenaro : 1. Victim opens the attacker’s web site.
2. Attacker sets up a web site which contain interesting and attractive content like ‘Do you want to make $1000 in a day?
3. Victim clicks to the interesting and attractive content URL.
4. Attacker creates a transparent ‘iframe’ in front of the URL which the victim attempts to click, so the victim thinks that he/she clicks on the ‘Do you want to make $1000 in a day?’ URL but actually he/she clicks on the content or URL that exists in the transparent ‘iframe’ which is setup by the attacker. What is the name of the attack which is mentioned in the scenario?
Option 1 : Clickjacking attack
Option 2 : Session Fixation
Option 3 : HTML injection
Option 4 : HTTP parameter Pollution
1. Clickjacking attack
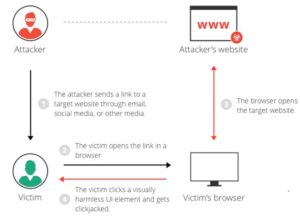
Clickjacking is an attack that tricks a user into clicking a web page element which is invisible or disguised as another element. this will cause users to unwittingly download malware, visit malicious sites , provide credentials or sensitive information, transfer money, or purchase products online.
Typically, clickjacking is performed by displaying an invisible page or HTML element, inside an iframe, on top of the page the user sees. The user believes they’re clicking the visible page but actually they’re clicking an invisible element within the additional page transposed on top of it.
The invisible page might be a malicious page, or a legitimate page the user didn’t shall visit – for instance , a page on the user’s banking site that authorizes the transfer of cash .
There are several variations of the clickjacking attack, such as:
- Likejacking – a way during which the Facebook “Like” button is manipulated, causing users to “like” a page they really didn’t shall like.
- Cursorjacking – a UI redressing technique that changes the cursor for the position the user perceives to a different position. Cursorjacking relies on vulnerabilities in Flash and therefore the Firefox browser, which have now been fixed.
2. Session Fixation
Session Fixation is an attack that allows an attacker to hijack a legitimate user session. The attack explores a limitation within the way the online application manages the session ID, more specifically the vulnerable web application. When authenticating a user, it doesn’t assign a replacement session ID, making it possible to use an existent session ID. The attack consists of obtaining a legitimate session ID (e.g. by connecting to the application), inducing a user to authenticate himself thereupon session ID, then hijacking the user-validated session by the knowledge of the used session ID. The attacker has got to provide a legitimate Web application session ID and check out to form the victim’s browser use it.
3. HTML injection
Hypertext terminology (HTML) injection may be a technique wont to cash in of non-validated input to switch an internet page presented by an internet application to its users. Attackers cash in of the very fact that the content of an internet page is usually associated with a previous interaction with users. When applications fail to validate user data, an attacker can send HTML-fomatted text to switch site content that gets presented to other users. A specifically crafted query can cause inclusion within the website of attacker-controlled HTML elements which change the way the appliance content gets exposed to the online .
HTML is that the language that determines how application data (like a products’ catalog) gets presented to users in their browser . This language contains visualization commands, just like the color of the page’s background and therefore the size of embedded pictures. It also contains links to other sites , and extra commands intended for the user’s browser. Furthermore, automated tools that collect useful information from the online on behalf of users often do so by systematically accessing and parsing the relevant information within the application’s HTML pages.
In modern interactive sites , the content of an internet page often reflects the results of processing previous user actions. If the user’s input isn’t validated and therefore the application is vulnerable, an attacker can craft and send input to the appliance that lets him inject pieces of his HTML code into the HTML content of the application’s response.
HTML injection attack is closely associated with Cross-site Scripting (XSS). HTML injection uses HTML to deface the page. XSS, because the name implies, injects JavaScript into the page. Both attacks exploit insufficient validation of user input.
A simple example of potential HTML Injection is an application’s “Search” form, during which the user enters a question text. When the user submits the query, the appliance responds by dynamically generating an internet page that shows matching results. This results page often shows the first query text to let the user see the context of those results. If the embedded query text contains syntactically correct HTML, it’s going to add attacker-controlled text, images and links to the present generated response page.
4. HTTP parameter Pollution
HTTP Parameter Pollution (HPP) may be a Web attack evasion technique that permits an attacker to craft a HTTP request so as to control or retrieve hidden information. This evasion technique is predicated on splitting an attack vector between multiple instances of a parameter with an equivalent name. Since none of the relevant HTTP RFCs define the semantics of HTTP parameter manipulation, each web application delivery platform may affect it differently. especially , some environments process such requests by concatenating the values taken from all instances of a parameter name within the request. This behavior is abused by the attacker so as to bypass pattern-based security mechanisms.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web-Server Concept
- Web-Server Attacks
- Web-Server Attack Tools
- Web-Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com




Wonderful work!
This is really interesting, You are an overly skilled blogger.
My brother suggested I might like this blog. He was entirely right.
This post actually made my day. You cann’t imagine just how much time I
had spent for this info! Thanks!
Thanks for a marvelous posting! I actually enjoyed reading it,
you’re a great author.
great blog!
I really like your blog..
I enjoy what you guys tend to be up too. This sort of clever work and coverage!
Keep up the fantastic works guys I’ve added you guys to blogroll.
This article is really a pleasant one !!!
Normally I don’t read article on blogs, but I wish to
say that this write-up very forced me to take a look
at and do it! Your writing taste has been surprised me.
Thank you, quite great article.
Hi my family member! I wish to say that this article is
awesome, nice written and come with approximately all important infos.
I would like to see extra posts like this .
Hi everybody, here every person is sharing such know-how, thus
it’s pleasant to read this blog, and I used to go to see this blog
daily.