Data Owner
An important component of understanding privacy principles and data protection is to start with clear roles and responsibilities for the assets. One important role is the data owner. Data owners can have legal rights and complete control over information and can authorize or deny access to that information. Their role in the context of privacy is central. The data owner is the person or group of individuals in an organization responsible and accountable for the data. In most organizations, this responsibility is a senior position, to include a CEO or president of the company, but particular data-related tasks can be delegated. The data owner is where the accountability resides ultimately. The data owner can be held liable for negligence in the event that sensitive data that they own is misused or disclosed in an unauthorized way. The extent of a data owner’s responsibility can be established and enforced through legal or regulatory measures. The organization’s data policy will outline the manner in which the data owner may use, collect, share, and store data that they own. All data, but especially data with a sensitivity level, must be assigned to an owner.
Tip A data owner sets data use and asset protection rules. In collaboration with information system owners, the data owner will determine the security controls for access and use for data within the system.
Note Data owner has synonymous terms used in other guidelines. Consider information owner or steward as interchangeable terms, for instance.
Expectations for the data owner are to provide due care and due diligence. These are primarily legal terms that guide information protection activities. Due care, in terms of asset management, is using reasonable measures and efforts to protect assets deemed valuable or assigned sensitivity levels. An example of providing due care is keeping and maintaining an accurate asset inventory. Additionally, due care extends to ensuring that all assets are classified appropriately and the classifications are accurate based on the information contained on the asset.
Due diligence is taking all expectable or practical steps to maintain due care. The importance of due care and due diligence is in incident response or data breach investigation. Organizations that demonstrate due care and due diligence may be able to reduce culpability and liability. An example of due diligence begins with an acknowledgment that valuable assets are found throughout an organization and significant effort must be made to account for and assess them. This will allow the organization to properly evaluate risk and protection strategies. Assets are no longer relegated to stationary boundaries. Assets like laptops, thumb drives, and portable devices are mobile. As data moves to the cloud, tangible and intangible assets and, therefore, due diligence extend to the cloud environment too.
Related Product : Personal Data Protection & General Data Protection Regulation Training & Certification
Data Controllers
The data controller is the natural or legal person, public authority, agency, or other body that, alone or jointly with others, determines the purposes and means of the processing of personal data. The controller is responsible for adhering to the principles relating to processing personal data. To that end, the controller has to be able to demonstrate compliance with the principles of lawfulness, fairness, transparency, data minimization, accuracy, storage limitation and integrity, and confidentiality of personal data. Data controllers negotiate privacy protections for personal data with data processors via secure contractual terms and assurances, called data processing agreements.
Data Processors
The value in data is often in the sharing or exchange of the information between authorized entities. The party responsible for transferring, transmitting, or otherwise sharing data on behalf of a data owner is a data processor. Data processors have a distinct role in the protection of data. In a healthcare setting, data exchange can be important in the safe and proper conduct of patient care, appropriate treatment, managing billing, and other organizational operations. In banking, the data supports business and individual investments as well as creditworthiness. The regulatory focus in GDPR and HIPAA, as examples, reflects the importance of data processing responsibilities.
Note A data processor is not synonymous with a data controller. The key difference is a data processor does not have legal responsibility and accountability for the data, as does a data controller. The processor performs data manipulation on behalf of the data controller. A data controller is an entity that determines the purposes, conditions, and means of processing the personal data. Figure 2.3 depicts the relationship between data processors and data controllers.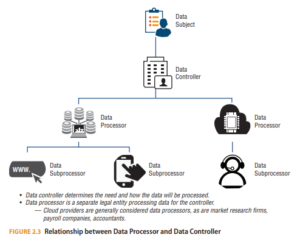
In some instances, people in organizations play both roles as data processor and data controller. For instance, a human resources firm would have data about their own employees and would be a data controller in this sense. However, if the firm provides outsourced human resource actions for other clients, the human resources firm would be a data processor for the client data, while the individual clients remain the data controllers.
Data Stewards
In the various functional areas of a business such as finance, human resources, sales, or IT, the organization will assign people who are responsible for the formation and execution of policies for the management of data and metadata. These individuals play an important role in the data governance process as subject-matter experts on the categorization of the data, data definitions for its use, and implementing the data governance policies in their area of responsibility. They manage the data quality requirements to ensure fitness of data that is within their business area. Fitness of data includes concerns such as the ability to use the data for its intended purpose in a format that is readable. Data stewards establish internal and external data access requirements for data in their functional area.
Data Custodians
In an organization, the data governance process should include a role for the data custodian. The data custodian role differs from the data steward. Data custodians implement the data delivery process in partnership with the data steward. However, the data custodian is much more concerned with the technologies used in data management and the tools that assist data users with the secure use of the data. There may be one or more people assigned as data custodians.
Data Remanence
Although many popular crime shows on TV depict a fictitious ability to recover any digital data on any medium, it is true that insufficient deletion of data can result in the compromise of the information. Residual data can remain on media if not disposed of properly, and recovery of that data by unauthorized viewers is possible. Data remanence occurs when data destruction efforts were insufficient to prevent the reconstruction of the data.
The underlying principle is that data simply deleted from a hard drive, CD, DVD, USB drive, or backup tape is not sufficiently discarded; in using the deletion command, only the pointers to the data are removed, not the data itself. Data with higher sensitivity classifications, marked as confidential or labeled as PHI, for instance, must follow rigorous destruction methods. The destruction must be certified, and evidence of the destruction/certification must be kept as a proper documentation of the process. A certificate of destruction from the entity that destroyed the data, signed by the persons who oversaw the data destruction, is usually sufficient.
The use of cloud providers has introduced some challenges with respect to data remanence. It takes significant collaboration from the cloud provider to make secure data destruction possible. The cloud user or tenant is not given access to the physical drive, only to a higher-level abstraction like file systems. Techniques such as overwriting file sectors are not possible as they are with on-premises data centers that the organization owns and operates. In SaaS/PaaS (Platform as a Service) environments, access happens only on the data level. In cloud environments, the alternative is to encrypt the data and keep the key outside the cloud environment where the data resides. When the data is no longer needed and the key is deleted, the data is rendered unusable and unreadable. This is not a perfect solution, but because cloud providers allocate resources and cloud users cannot control where the physical assets that house the data reside, overwrite methods are impossible.
The rules and regulations that govern the destruction of data often dictate the level of protection that must be applied to various types of sensitive information. Several U.S. federal laws are potentially applicable to organizations relative to data destruction, including the GLBA, which limits the disclosure and use of customer information and imposes a security rule for financial institutions. HIPAA regulates the handling of customer medical records and information. The FCRA governs the use, disclosure, and disposal of information in reports about consumer credit and credit ratings. The approved European standard BSEN 15713 defines the code of practice for the secure destruction of confidential information. It applies to any organization that collects, transports, and destroys confidential materials. BSEN 15713 can be integrated with other management system standards, most commonly ISO 9001.
The specific requirements of the frameworks and regulations are notable. For example, in the U.S. National Security Agency (NSA) Central Security Service (CSS) Policy Manual 9-12, there is guidance for countermeasures against data remanence. The requirements begin with removing all labels and markings that indicate previous use and classification. After that, the requirements vary depending on the type of medium being used.
Some of the requirements include the following:
- Sanitize magnetic tapes and disks by degaussing using an NSA/CSS–evaluated degausser and/or incinerating by burning the material, reducing it to ash. In doing so, the following criteria apply:
- It is highly recommended to physically damage the hard disk drive by deforming the internal platters prior to release by any means or by using a hard disk drive crusher.
- Hard disks can be degaussed by using a degaussing wand, disassembling the device, and erasing all surfaces of the enclosed platters.
- Disintegrate the hard disk into particles that are nominally 2 millimeter edge length in size. It is highly recommended to disintegrate hard disk drive storage devices in bulk with other storage devices.
- Shredding of smaller diskettes is allowed using an approved crosscut shredder. Remove the diskette cover and metal hub prior to shredding.
- Optical storage devices including CDs, DVDs, and Blu-ray disks (BDs) can be sanitized in the following ways:
- The only way BDs can be sanitized is by incinerating the material and reducing it to ash. The other methods listed here do not work for them. Incineration also works for CDs and DVDs.
- CDs and DVDs can be disintegrated.
- CDs and DVDs can be shredded.
- CDs and DVDs can be embossed/knurled by using an approved optical storage device embosser/knurler.
- CDs can be sanitized by approved grinders. DVDs or BDs cannot be sanitized by grinding.
- For solid-state storage devices, including random access memory (RAM), read only memory (ROM), Field Programmable Gate Array (FPGA), smart cards, and flash memory, the following methods are acceptable:
- Disintegrate into particles that are nominally 2 millimeter edge-length in size using an approved disintegrator; it is recommended to do this in bulk with multiple storage devices together.
- Incinerate the material to ash.
- Smart cards can be sanitized using strip shredding to a maximum of 2 millimeters or cutting the smart card into strips diagonally at a 45-degree angle, ensuring that the microchip is cut through the center. Also, make sure that the barcode, magnetic strip, and written information are cut into several pieces and the written information is unreadable. Cross-cut shredders are not allowed for this shredding.
The requirements of BSEN 15713 are similar and include the following:
- There must be a confidential destruction premises.
- A written contract covering all transactions should exist between the client and the organization; subcontractors must follow the guidelines too.
- Personnel doing this work must be trained, be certified, and have passed a Criminal Records Bureau (CRB) check or Disclosure or Barring Service (DBS) check.
- Confidential material to be collected should remain protected from unauthorized access from the point of collection to complete destruction.
- The trucks that are used to collect and transport protected material have specific requirements, including being box-shaped, having the ability for drivers to communicate to base stations, being lockable, and not being left unattended, and so on.
- In addition to the destruction focus, there is consideration for environmental issues, and recycling is allowed under certain conditions.
- There are prescribed due diligence checks that should be conducted in addition to the stated requirements. These include checking the licenses of drivers, physical checking of trucks and destruction areas, and so on.
There are two general approaches to data destruction. The first approach is to render the actual device containing the media useless. Physical destruction of the media, electromagnetic degaussing, and incineration are common tactics. If the organization intends to repurpose the device after destroying the sensitive data, this approach would be appropriate. If the media is not rewritable, physical destruction is the only method that will ensure the information is destroyed.
The other type of asset disposal is by cleansing or sanitizing the media/drive. The physical media can therefore be reused, but there is no trace of data remanence after the data-wiping action. There are numerous validated processes for this objective.
Asset disposal policy should differentiate between assets being reused within the organization and those to be repurposed outside of the organization. For example, an asset to be reallocated internally may be sufficiently sanitized by a lower level of sanitization (e.g., reformatting or re-imaging the hard drive). This scenario does not preclude the organization from mandating the highest levels of sanitization if the assets are deemed critical or the data is sensitive. Some different tactics to achieve desired levels of security assurance with specific steps and instructions are available in NIST SP 800-88, “Guidelines for Media Sanitization”, at http://nvlpubs.nist.gov/nistpubs/SpecialPublications/ NIST.SP.800-88r1.pdf.
To achieve a level of assurance of adequate asset sanitization, the following techniques can be used:
- Purging: This is the indisputable erasing of data from the storage device in such a way that the data may never be recovered. It can be accomplished by overwrite, block erase, and cryptographic erasure, through the use of dedicated, standardized device sanitize commands.
- Cleansing or clearing: The organization can use software or hardware products to overwrite storage space on the media with non sensitive data, using the standard read and write commands for the device.
- Destruction: The organization can purge media before submitting it for destruction. There are numerous ways to physically destroy media. Some of the traditional and acceptable methods are drive shredders, pulverization, incineration, and acid.
Examples of specific techniques to achieve the desired level of assurance in sanitization requirements include the following:
- Zeroing: This erases data on the disk and overwrites it with all zeros.
- Degaussing: This is a process whereby the magnetic media is erased, i.e., returned to its initial blank state through the use of high-powered electromagnets.
- Overwriting: Data are written to storage locations that previously held sensitive data. To satisfy the Department of Defense (DoD) clearing requirement, it is sufficient to write any character to all data locations in question. It is typical to use random passes of 0 and 1 combinations, not patterns, to overwrite. The number of times an overwrite must be accomplished depends on storage media, sometimes on its sensitivity, and sometimes on differing organizational requirements.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


