Scoping and Tailoring
Establishing the baseline of security controls begins the scoping and tailoring process. Because every organization has unique factors that impact how it values assets, the threats it faces, and what level of security it can afford, in terms of both resources and business operation impact, refining individual controls is an important role for the security professional. A CISSP has to help build the plan to clarify and limit the general recommendations of guidelines and frameworks to be applicable to the organization.
Scoping and tailoring are not synonymous, but the concepts work together to build the security baseline. Scoping is the process the organization undertakes to consider which security controls apply and what assets they need to protect. Tailoring is the process of modifying the set of controls to meet the specific characteristics and requirements of the organization. As each organization is different, some controls in a framework may not apply. Those controls can be removed from the baseline. Sometimes a security control does apply, but implementation should be altered based on the information asset or information use within the organization. In that case, tailoring the controls is done to eliminate unnecessary requirements or to incorporate compensating controls when needed based on organizational variables. The scoping and tailoring activities must be well documented with appropriate justification. Figure 2.5 illustrates the tailoring process according to best practices, including NIST SP 800-53.le for the security professional. A CISSP has to help build the plan to clarify and limit the general
recommendations of guidelines and frameworks to be applicable to the organization.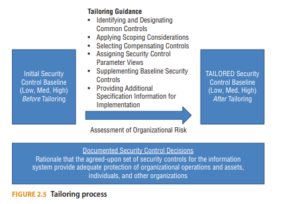
Tip Convenience is not a factor for removing or altering security controls. Make sure any changes to baseline requirements are rationalized against operational requirements and are analyzed for impact to risk.
Common Controls
In any enterprise, security controls may safeguard multiple assets. These controls are considered common controls and are typically implemented as part of the organization’s control architecture. The security benefits of implementing common controls are inheritable across the assets in scope for the baseline assessment. Effective use of common controls can potentially reduce the overall resource expenditures by organizations. The following are examples of common controls within the types of controls:
- Physical controls: The access controls for physical entry are shared by all systems located in a data center. The environmental controls maintain proper conditions and suppression of fire for all computing equipment.
- Technical controls: Firewalls, intrusion detection systems, and data loss prevention appliances are types of security devices that provide network boundary defense for all assets. Public key infrastructure (PKI) and network security monitoring are also examples of inheritable technical controls from which all assets benefit.
- Administrative controls: Policy for initial and annual information security training applies equally to all users of network and application resources in the organization.
Compensating Security Controls
In some cases, the prescribed or recommended security controls are applicable but cannot be scoped or tailored sufficiently to meet the control objective. When baseline controls have potential to degrade or obstruct business operations or are cost-prohibitive, we have to explore compensating controls. This category of security controls augments the primary control’s ability to achieve the control objective or replaces the primary control in order to meet the control objective.
To illustrate this point, segregation of duties for security personnel is a prescribed security control. In some organizations with small security staffs, segregation of duties may be too costly in terms of needing more employees. In this case, a compensating control can be increased collection and review of security activity logs.
Tip Integrating compensating controls into a security baseline requires documentation of why the compensating controls are necessary and how they provide equivalent mitigation of the risk.
Supplementing Security Control Baselines
As a reminder, a security baseline is a minimum set of security controls that are required. You may want to implement additional security controls. Supplemental controls are based on the specific threats or regulatory requirements of an organization or an industry.
Providing Additional Specification Information for Control Implementation
Additional detail may be necessary to fully define the intent of a security control, e.g., directions on how to apply the control in different situations. Organizations may allow additional implementation data per department, business unit, or other subordinate component of the enterprise, but they may not change the intent of the security control or modify the original language in the control.
A resource that highlights supplemental security controls that can be considered is the U.S. National Security Agency Methodology for Adversary Obstruction (https://www.cdse.edu/documents/cdse/nsa-methodology-for-adversaryobstruction.pdf).
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


