The Secure Cryptoprocessor challenge with standard microprocessors is that code running with the highest privilege can access any device and any memory location, meaning that the security of the system depends entirely on the security of all of the software operating at that privilege level. If that software is defective, or can be compromised, then the fundamental security of everything done on that secure Cryptoprocessor becomes suspect.
To address this problem, hardware modules called secure cryptoprocessors have been developed that are resistant to hardware tampering and that have a very limited interface (i.e. attack surface), making it easier to verify the integrity and secure operation of the (limited) code running on the secure cryptoprocessor.
Cryptoprocessors are used to provide services such as:
- Hardware-based True Random Number Generators (TRNG)
- Secure generation of keys using the embedded TRNG
- Secure storage of keys that are not externally accessible
- Encryption and digital signing using internally secured keys
- High-speed encryption, offloading the main secure cryptoprocessor from the computational burden of cryptographic operations
Features of cryptoprocessors that enhance their security over standard microprocessors (that could do most of the above in software) can include:
- Tamper detection with automatic destruction of storage in the event of tampering, and a design that makes it very difficult to tamper with the device without leaving obvious traces of the physical compromise. These protections can range from anti-tamper stickers that clearly show attempts to access the device’s internal components to secure enclosures that detect unauthorized attempts to open the device and automatically erase or destroy sensitive key material.
- Chip design features such as shield layers to prevent eavesdropping on internal signals using ion probes or other microscopic devices
- A hardware-based cryptographic accelerator (i.e. specialized instructions or logic to increase the performance of standard cryptographic algorithms such as AES, SHA, RSA, ECC, DSA, ECDSA, )
- A trusted boot process that validates the initial boot firmware and operating system load
There are many types of secure cryptoprocessors:
- Proprietary, such as Apple’s Secure Enclave Processor (SEP) found in newer iPhones
- Open standard, such as the Trusted Platform Module (TPM) as specified by the ISO/IEC 11889 standard and used in some laptops and servers
- Standalone (e.g. separate standalone device with external communications ports)
- Smartcards
Some of these are discussed further below.
Trusted Platform Module (TPM)
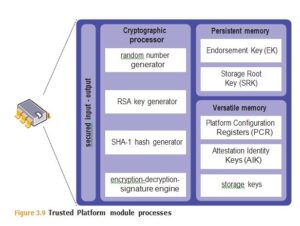
A TPM is a separate processor that provides secure storage and cryptographic services as specified by ISO/IEC 11889 (see Figures 3.9 and 3.10). A TPM can be used by the operating system, secure cryptoprocessor BIOS, or application (if the OS provides access to the TPM) to provide a number of cryptographic and security services:
- Generate private/public key pairs such that the private key never leaves the TPM in plaintext, substantially increasing the security related to the private key (Public/private keys are discussed further later in this character )
- Digitally sign data using a private key that is stored on the TPM and that never leaves the confines of the TPM, significantly decreasing the possibility that the key can become known by an attacker and used to forge identities and launch man-in-the-middle attacks (Digital signatures are discussed later in this character )
- Encrypt data such that it can only be decrypted using the same TPM
- Verify the state of the machine the TPM is installed on to detect certain forms of tampering (i.e. with the BIOS)

Potential Weaknesses
The Private Endorsement Key (PEK) is a fundamental component of a TPM’s security. This key is generated by the TPM manufacturer and burned into the TPM hardware during the manufacturing process. Because of this, the user/system owner depends upon the security of the TPM manufacturer to ensure that the PEK remains confidential.
We also depend on the quality of the TPM manufacturer’s processes. In late 2017 it was revealed that a defect in the software library used by Infineon for their line of Smart- cards and TPMs contained a flaw which made it possible to deduce the private key stored internally. As a result, there were millions of cryptographic keys made unreliable and vulnerable. Attackers were able to calculate the private portion of an account holder’s key from having access to only the public portion. What happened, unfortunately, is that hackers impersonated legitimate users with the assurance and nonrepudiation provided by having their private keys.
Cryptographic Module
A cryptographic module (see Figure 3.11) is typically a hardware device that implements key generation and other cryptographic functions and is embedded in a larger system.

The advantages of using a cryptographic module as opposed to obtaining the equivalent functionality from a cryptographic software library include the following:
- By performing critical cryptographic functions on a separate device that is dedicated to that purpose, it is much harder for malware or other software-based attacks to compromise the security of the cryptographic operation.
- By isolating security-sensitive functionality in an isolated device with limited interfaces and attack surfaces, it is easier to provide assurances about the secure operation of the device. It also makes it easier to provide secure functions to larger systems by embedding a cryptographic module within the larger systems.
- Increased availability of non-cryptographic dedicated resources.
- Most secure cryptographic modules contain physical security protections including tamper resistance and tamper detection, making it very difficult to compromise the security of the device even if the device has been physically compromised.
- Some cryptographic modules can enforce separation of duties so that certain sensitive operations, such as manipulating key storage, can only be done with the cooperation of two different individuals who authenticate to the cryptographic module separately.
Some government organizations have issued standards related to the security of cryptographic modules and have established evaluation and certification processes so that manufacturers can have the security of their devices validated by an independent third party and users can have confidence in the security that using the module will provide their larger system.
For example, the U.S. government’s FIPS 140-2, “Security Requirements for Cryptographic Modules,” specifies the requirements for cryptographic hardware and software to meet four different levels of security. It also provides for certification of products to validate they meet the requirements.
Internationally, the “Common Criteria for Information Technology Security Evaluation,” documented in the ISO/IEC 15408 standard, provides an alternate set of requirements and certification processes to validate information security products.
Hardware Security Module (HSM)
An HSM (see Figure 3.12) is a type of cryptographic module designed to stand alone as an appliance, and to provide cryptographic services over an externally accessible API (typically over a network or USB connection).

HSMs are frequently found in Certificate Authorities (CAs) that use them to protect their root private keys, and payment processors that use them to protect the symmetric encryption keys used to protect cardholder data. HSMs are also used in many national security applications or other environments where proper management of cryptographic material is critical to the business process. CAs, digital signatures, certificates, and asymmetric/symmetric encryption are discussed later in this chapter.
Smartcard
Smartcards (see Figure 3.13) are credit card–sized cryptographic modules typically used to provide portable secure storage for the purposes of identity management (used for multifactor authentication), secure transport of sensitive information (such as keys between hardware security modules), and payment processing (such as the EMV standard for credit cards).

Because of the ease with which one can access the internal electronics of a smartcard, a number of hardware-based side-channel attacks have been developed by researchers.
Depending on how poorly or wisely the algorithm was implemented in the chip, side-channel attacks such as a timing attack can reveal valuable information about what’s kept secret on the chip. A timing attack is performed like this: the attacker will measure and analyze the exact time period involved for the chip to process any instruction to it. By detecting minute differences in the time needed to complete the instruction, the attacker can infer secret data. Similarly, power analysis attacks can also allow an attacker to make inferences about the data contained in the chip.


