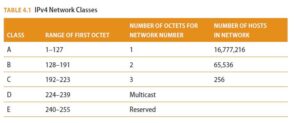
Internet Protocol Networking is the main protocol of the Internet. The protocol resides at the OSI model’s network layer and the TCP/IP model’s Internet layer. For all intents and purposes, IP makes the Internet a reality because the protocol makes it possible to relay datagrams across network boundaries. IP exists in two versions: IPv4, which is currently the main version used, and IPv6, to which Internet-connected devices are expected to evolve. IPv4 uses 32-bit IP addresses, often written as four decimal numbers called octets, in the range 0–255, such as 172.16.8.93. Refer to Table 4.1 to see the network classes that subdivide IP addressing.
In contrast, IPv6 uses 128 bits portioned into four hexadecimal digits, which are separated by colons for addressing and segmented into two parts: a 64-bit network prefix and a 64-bit interface identifier. An example IPv6 address looks like 2607:f0d0:1002:0051:0000:0000:0000:0004. The added complexity adds to the number of addresses available for an expanding number of interconnected devices. The scheme intends also to improve network addressing and routing.
Some of the principal benefits of IPv6 over IPv4 include the following:
- Scoped addresses: This adds a layer of security and access control for administrators who can group and then deny or allow access to network services, like file servers or printing.
- Autoconfiguration: This removes the need for both DHCP and Network Address Translation (NAT).
- Quality of Service (QoS) priority values: Based on the content priority, traffic management is conducted according to preset QoS priority values.
The adoption of IPv6 has been slow. Operating systems since about 2000 have had the ability to use IPv6 either natively or via an add-in. IPv6 was developed by the IETF to manage anticipated problem of IPv4 address exhaustion. Adoption hurdles include added cost of some IPv6-capable devices and the fact that IPv4 works well. Decision-makers are reluctant to either make a change for the sake of change itself or make process improvements that provide a minimal financial return on investment. Early adopters of IPv6 are found in private, internal networks in large corporations, research laboratories, and universities.
A basic understanding of the addressing and numbering that define the TCP/IP networking scheme is important. At a basic level, there are three components:
- MAC address: This is the permanent address of the hardware device.
- IP address: This is the temporary or logical address assigned, corresponding to a unique MAC address.
- Domain name: Also called computer name, this is an assigned temporary, human-language convention that corresponds to the IP address.
NOTE Permanent and temporary addresses in the context of MAC and IP addresses can be a bit misleading. MAC addresses are meant to be permanent, but they can be changed via some NICs and modern operating systems. A NIC change is truly a change on the hardware, but the operating system makes the change in memory. However, the operating system change is still effective, and the altered or assigned MAC address overrules the MAC issued by the NIC manufacturer. Additionally, with an increasing reliance on virtualization, the MAC address becomes much less permanent. With every new virtual machine (VM) created, the MAC address often is a new one as well. This can be of special concern when software packages enforce licensing according to the MAC address (which presumed to be a physical asset that wouldn’t change no matter how often the client reinstalled the server). IP addresses are changed often by manual intervention or via DHCP services. The IP address can be assigned to be static, but an administrator can change it relatively quickly.
TCP/IP
At this point in the chapter, the term TCP/IP must seem to be a generic concept to define everything—protocols, networking models, and even a synonym for the Internet itself. The concepts behind TCP/IP are central to understanding telecommunications and networking, but there are specific principles and processes that information security professionals must understand in depth. To start, TCP/IP is a set of rules (protocols) that provide a framework or governance for communications that enables interconnection of separate nodes across different network boundaries on the Internet. TCP/IP sets up the way processors package data into data packets, senders transfer the packets, and receivers accept the packets, as well as routing information to the destination.
The acronym TCP/IP often is used to refer to the entire protocol suite, which contains other protocols besides TCP and IP. The transport layer of both the OSI and TCP/ IP models is home to UDP in addition to TCP. Similarly, the OSI model’s network layer and the TCP/IP model’s Internet layer each house the IP, ARP, IGMP, and ICMP protocols. Expanding further is when someone mentions the TCP/IP stack, which likely is referring to protocols and layers above and below the earlier two.
If strictly talking about IP and TCP as individual protocols and not the entire TCP/ IP protocol suite, then TCP/IP consists of TCP layered on top of IP to determine the logistics of data in motion and establish virtual circuits. TCP and IP are a longstanding pair of protocols, developed in 1978 by Bob Kahn and Vint Cerf. A description of TCP/ IP methodology is that a data stream is split into IP packets that are then reassembled into the data stream at the destination. If the destination does not acknowledge receipt of a packet, TCP/IP supports retransmitting lost packets, a feature performed by TCP. In short, TCP/IP includes the destination and route with the packet while also ensuring the reliability by checking for errors and supporting requests for retransmission.
DNS and domain address resolution are important components that facilitate the ability to scale networking efficiently and effectively. Certainly, the principal reason to enforce addressing is to ensure that networked computers can locate specific machines and tell one computer from another. Another benefit, particularly of domain address resolution, is to enable a naming scheme readable in human language instead of the more machine-like schemes of IP addresses. Humans are more apt to remember www.microsoft.com than 32.100.122.175. The resolution of numerical addresses to human-readable format was more a convenience than a necessity to scale computer adoption and use.
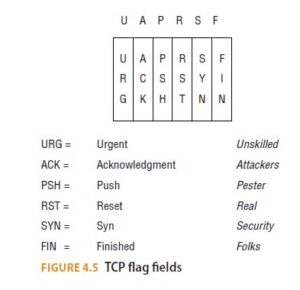
In the TCP header there is some important information contained in areas called flag fields. These fields are important because they can contain one or more control bits in the form of an 8-bit flag field. The bits determine the function of that TCP packet and request a specific manner of response from the recipient. Multiple flags can be used in some conditions. In the TCP three-way handshake, for example, both the SYN and ACK flags are set. The bit positions correspond to a control setting per single flag. Each position can be set on with a value of 1 or off with a value of 0. Each of the eight flags is a byte presented in either hex or binary format. A hex presentation of 00010010 is 0x12.
Of that 8-bit flag field, let’s specify the last six flags: URG, ACK, PSH, RST, SYN, and FIN. A mnemonic phrase can be helpful, like “Unskilled Attackers Pester Real Security Folks,” with the first letter being associated with each of the six TCP flags. In the case mentioned earlier, represented by hex as 0x12, which depicts the initial response of a three-way handshake, the flags set are 000A00S0. In this layout, the fourth and seventh flags are enabled (value is 1). The flag layout can be depicted as one letter per flag, or UAPRSF, as shown in Figure 4.5.
Network Attacks
Networking protocols were designed long before the necessity of security was fully recognized. Consequently, even today networked hosts remain vulnerable and networked systems fail to implement mitigating controls. Systems that are hardened against attacks that exploit misconfiguration and unnecessary services can still be vulnerable from attacks exploiting network services. Several updates and revisions to networking protocols have been adopted, but weaknesses remain due to security being designed as an afterthought, although progress continues to be made. A recent example is the Google Chrome browser finally adopting support for DNS over TLS (a secured version of the DNS protocol).
The “Open System Interconnection and Transmission Control Protocol/Internet Protocol Models” section earlier in this chapter explored the OSI model and how its layers continue in the abstract from physical to application. It examined where established protocols fall within those layers. The section also touched on what attack vectors exist at each OSI layer to expose some of the vulnerability therein.
By knowing how networked hosts communicate with each other, security professionals can better understand how network attacks can occur and be successful. Armed with that information, the following sections delve into a variety of network attacks.
Distributed Denial-of-Service (DDoS) Attacks
When an attacker does not have the skills or tools for a sophisticated attack, they may use a brute-force attack, which can be just as effective. Simply flooding the targeted system with UDP packets from infected machines has proven successful, especially as the Internet of Things (IoT) devices have been used, unwittingly, to help launch the distributed denial-of-service (DDoS) attacks. A typical DDoS attack consists of a large number of individual machines that are subverted to bombard a target with overwhelming traffic over a short period of time. The individual contribution of any one compromised machine, be it a PC, IoT device, networking hardware, or server, would amount to no damage. But the collective sum creates a crushing amount of traffic to the end target.
Tip To subvert the volumes of machines needed for a DDoS, a botnet is created and used. The botnet is a number of Internet-connected and commandeered computers that communicate in a command and control manner.
Although the term botnet has grown in popular media because of the use of the tactic in enlisting IoT devices such as baby monitors, TVs, webcams, and other network-aware wireless devices, botnets were weaponized almost 20 years ago. Medical devices were hacked when the FDA published guidance that any Unix-based machines were to have a standard, known configuration. These certified, special-purpose computing devices became targets because they inherited the weaknesses of the standard configurations. Once hackers discovered vulnerabilities to exploit, the weaknesses were applicable across an entire platform, and a medical device botnet was created. The number and varieties of devices used to create botnets has expanded. In 2016, large numbers of digital recording video (DVR) devices and other Internet-enabled systems were used to create the Mirai botnet. This botnet was used in a series of DDoS attacks against Dyn.com, one of the largest providers of DNS services. This attack disrupted major computing platforms operated by PayPal, Twitter, Reddit, GitHub, Amazon, Netflix, Spotify, and RuneScape. In sum, botnets are enslaving vast numbers of IoT devices and creating highly successful DDoS attacks.
SYN Flooding
In an attempt to overload a system, this type of attack bombards the recipient with an overwhelming number of SYN packets, and the sender or senders do not acknowledge any of the replies. SYN flooding is a form of denial-of-service (DoS) attack, exploiting properties of TCP at the transport layer (layer 4). TCP initiates a connection by sending a SYN packet, which when received and accepted is replied to with a SYN-ACK packet. The SYN flooding DoS attack is executed by sending massive amounts of those SYN packets. The SYN packets accumulate at the recipient system, and the software crashes because it cannot handle the overflow. The attacker attempts to consume enough server resources to make the system unresponsive to legitimate traffic. Some refer to this attack as the half-open attack because of the partial three-way TCP/IP handshake that underlies the attack. Eventually, given enough connection attempts, the capacity of the network card and stack to maintain open connections is exhausted. The attack was imagined decades before it was actually performed. Until the source code and descriptions of the SYN flooding attacks were published in 1996 in the magazines 2600 and Phrack, attackers had not executed the attack successfully. That changed when the publicly available information was used in an attack against Panix, a New York ISP, for several days.
Even though these types of attacks have such a long history and the mitigations have been in existence for almost as long, SYN flooding is still a common attack. There are some ways to mitigate a SYN flood vulnerability. A few of the most prevalent approaches are the following:
- Increasing backlog queue: This is an allowance or increase of half-open connections a system will It requires additional memory resources to increase the maximum backlog. Depending on the availability of memory resources, mitigating the SYN flooding threat can degrade system performance. A risk-benefit analysis is required against unwanted denial of service impact and slower performance.
- Recycling the oldest half-open TCP connection: This is a first-in, first-out queueing strategy where once the backlog queue limit is reached, the oldest half- open request is overwritten. The benefit is fully establishing legitimate connections faster than the backlog can be filled with malicious SYN packets. However, if the backlog queue is too small or the attack too voluminous, this mitigation can be insufficient.
- SYN cookies: The server responds to each connection request, SYN, with a SYN-ACK packet. The SYN request is dropped from the The port is open to new, hopefully legitimate, new connections. If the initial connection is legitimate, the original sender will send its ACK packet. The initial recipient, which created the SYN cookie, will reconstruct the SYN backlog queue entry. Of course, there will be some limitations as some information about the TCP connection can be lost. This is more advantageous than the full DoS outage.
Smurfing
Smurfing is a historical type of attack dating back to the 1990s that is categorized as a DDoS attack. The name comes from a popular cartoon of the time and represents the concept of an overwhelming number of very small attackers that successfully overtake a larger opponent.
The Internet Control Message Protocol (ICMP) uses ping packets to troubleshoot network connections by determining the reachability of a target host and a single system as the legitimate source. Smurfing exploits the functionality of the ICMP and broadcast subnets configured to magnify ICMP pings that will respond. These misconfigured networks are called smurf amplifiers. Using the IP broadcast, attackers send packets spoofing an intended victim source IP. The echo ICMP packet is used because ping checks to see if systems are alive on the network. The result of the broadcast message, especially if exploiting the presence of smurf amplification, is that all the computers on the network will respond to the targeted system. See Figure 4.6 for an illustration of the effect on the targeted system. In a large, distributed network, the volume of responses can overwhelm the target system.

Today, techniques exist to mitigate the effects of DDoS attacks. However, the attack method still works well in multiple, effective forms. The famed Mirai attack that crippled several enterprise networks was a form of a DDoS attack, modeled after a smurf attack.
Dozens of companies were affected, including Dyn DNS, GitHub, CNN, Reddit, Visa, HBO, and the BBC.
NOTE Internet Relay Chat (IRC) servers were highly susceptible to these attacks. Script kiddies or younger hackers in general preferred smurf attacks through IRC servers to take down chat rooms.
Today, the smurf attack is uncommon. Preventing an attack involves routine actions that administrators commonly use. External ping requests or broadcasts are typically ignored. The host or router is configured to be nonresponsive, and the requests are not forwarded. The remediation of smurf attacks also had a social component as benevolent actors posted lists of smurf amplifiers. Administrators of systems would notice their IP addresses on the smurf amplifier list and take action to configure the systems correctly. Those administrators that did not would get feedback from business or community users in the network about performance degradation. That pressure persuaded them to take the appropriate actions.
Some of the other commands that are central to creating these types of attacks, like ping and echo, are now commonly blocked. These include sourceroute and traceroute. However, these commands can also be helpful for troubleshooting. There are several specific attacks that are common enough to outline:
- Ping of death: Sending a ping packet that violates the Maximum Transmission Unit (MTU) size of 65,536 bytes, causing a crash
- Ping flooding: Overwhelming a system with a multitude of pings
- Teardrop: A network layer (Layer 3) attack, sending malformed packets to confuse the operating system, which cannot reassemble the packet
- Buffer overflow: An attack that overwhelms a specific type of memory on a system—the buffers. Robust input validation in applications prevents this
- Fraggle: A type of smurf attack that uses UDP echo packets instead of ICMP packets
DDoS and the Internet of Things (IoT)
As an emerging technology, IoT devices deserve a little more attention in this chapter. From a security perspective, these devices offer a soft target for potential attackers. They are delivered with default settings that are easily guessed or, in fact, publicly well known. Administrative credentials and management access are wide open to Internet-facing inter- faces. Attackers can exploit the devices with relatively simple remote access code. What compounds the vulnerabilities is that users do not interact with the devices the same way as they do with office automation or other endpoint computing assets. The default settings are rarely changed, even if the end user has the ability to make changes. Vendors are typically slow to provide upgrades and patches, if they supply post-sale manufacturing support at all. For these reasons, the devices are easy prey, and users often have no idea the devices are being hacked until it is too late.
The volume of IoT devices generates a lot of concern from security professionals. It is estimated that there are already tens of millions of vulnerable IoT devices. That number is growing. The interconnections are usually always on, left unprotected to ingress and egress unlike a typical LAN or WAN, but they enjoy high-speed connections. These variables explain why a botnet of huge groups of commandeered IoT devices presents a serious problem. Common attack sequences consist of compromising the device to send spam or broadcast messages. If spam filters block that attack, a tailored malware insert may be tried, like fast flux, which is a DNS technique to hide spamming attacks. If that does not accomplish the disruption, a brute-force type of DDoS might be launched.
Increasingly, well-resourced websites have sufficient bandwidth and can expand capacity above baseline or normal usage levels to withstand most attacks. However, just the threat of launching an attack can be enough to convince website owners to pay a ransom to extortionists to avoid testing the limits of the targeted site’s ability to remain responsive.
DDoS and Spam
A working definition of spam is the electronic equivalent of junk mail in the physical world. In most cases, spam is a nuisance but not an attempted cybersecurity attack. How- ever, spam can exist in the context of a DDoS attack. When an attacker sends a command to launch a spam campaign, the end result is an overwhelming volume of traffic. The spam traffic likely originates from a set of malicious botnets, with the outcome being spam. The receiving systems process the messages as legitimate, which is a mistake. The spam bots have spoofed the email addresses, which is a tactic unlike packet-level DDoS.
Normally, an individual spam message is just an unsolicited email message with unwanted advertising, perhaps even seeking to deliver a malicious payload. However, as part of a DDoS attack, spam can be used as an acceptable type of traffic to deliver an onslaught of data. The volume of data to be received could shut down a system or mail gateway.
Man-in-the-Middle Attacks
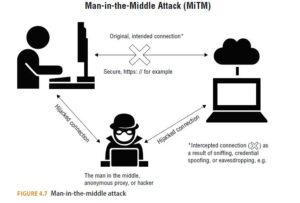
In a communication where sender and receiver believe they are connected, a MitM attack can be hard to detect and presents a significant threat to unprotected communications.
The attacker intercepts the signal and secretly relays and possibly alters the communication before stopping the transmission or allowing the message to reach the intended recipient. Eavesdropping is a specific type of MitM attack. In that scenario, the attacker relays the message to complete the circuit. The entire conversation is overheard, and in some instances controlled, by the attacker, while the sender and receiver think the message is private. Figure 4.7 depicts the general concepts of a MitM attack.
Another type of MitM attack is impersonation. This happens when the attacker circumvents the authentication process and compromises the credentials of one account. The endpoint communicating with the attacker is not aware that the communication is intercepted.
There are two main ways to prevent or detect MitM attacks: authentication and tam- per detection. Authentication provides some degree of certainty that a given message has come from a legitimate source. Tamper detection merely shows evidence that a message may have been altered.
- Authentication: To prevent MitM attacks, cryptographic protocols are used to authenticate the endpoints or transmission media. One such technique is to employ a TLS server paired with X.509 certificates. The X.509 certificates are used by the mutually trusted certificate authority (CA) to authenticate one or more entities. The message and an exchange of public keys are employed to make the channel secure.
- Tamper detection: Another way to detect MitM attacks is through examination of any latency in the transaction above baseline expectations. Response times are checked and normal factors like long calculations of hash functions are accounted for. If a delay is not explained, there may be unwanted, malicious third-party interference in the communication.
Packet Sniffing
Administrators often use packet sniffing tools for legitimate purposes, like troubleshooting. But attackers conduct passive MitM packet sniffing to gain information for adversarial purposes. Any unencrypted protocols are subject to passive attacks where an attacker has been able to place a packet sniffing tool to monitor traffic. The monitoring might be used to determine traffic types and patterns or to map network information. In any case, packet sniffing greatly benefits the attacker in preparing for other types of attacks. Say for example that an attacker using packet sniffing discovers that a company still uses an out- dated version of SSL or discovers the IP address of the Active Directory controller. The attacker is now set up to exploit that outdated protocol or server. Packet sniffing can also include actually grabbing packets in transit and attempting to extract useful information from the contents. Contained in some packets are usernames, passwords, IP addresses, credit card numbers, and other valuable payload.
Hijacking Attacks
Hijacking attacks describe many different types of MitM attack. A hijacking attack is any attack that involves the exploitation of a session, which is an established dialogue between devices. Normally a session is managed by a control mechanism such as a cookie or token. An attacker might try to intercept or eavesdrop the session token or cookie. In the case where an attacker has sniffed the cookie or token, the attacker may connect with the server using the legitimate token in parallel with the victim. Or the attacker may intercept the session token to use as well as to send a specially formed packet to the victim to terminate their initial session.
Many websites require authentication and use cookies to remember session tracking information. When the session is terminated as the user logs out, the cookie and credentials are typically cleared. Hijacking a session and stealing the token or cookie while the session is active can provide an attacker with valuable, sensitive information, such as unique details on what site was visited. Even worse, hijacking the session cookie may allow the attacker an opportunity to continue a session, posing as the victim.
Tip Promiscuous mode is a setting that packet sniffers enable to stop a device from discarding or filtering data unintended for it. The packet sniffer can gain access to the additional traffic and data packets that otherwise would have been filtered.


