By eliminating the dependency on cabling to the endpoint, wireless technologies have expanded networking capabilities significantly. Deploying a wireless network is relatively easy and has become the preference in many corporate environments. Home networking is made simple by wireless technology. With the IoT devices reaching the market, the demand for wireless capabilities is increasing. The main limitation to wireless networks, or WiFi, is the range of the signal. As this is a security discussion, it is important to balance all the new capabilities with an understanding of the risks that wireless connections present. From there, you can strategize several security approaches to mitigate vulnerabilities. In general terms, the security of wireless transmissions relies on a combination of physical and technical controls, like the implementation of shielded device-use areas and encryption.
Wireless networks face the same vulnerabilities, threats, and risks as any cabled net- work, but they also have additional security considerations. One of the principal issues with wireless technology is the insecure nature of the technology in the default configuration. For instance, wireless devices are sometimes shipped with a default administrator credential of admin for the username and password for the password. This is acceptable if the recipient changes the credentials or establishes a multifactor authentication process before the device goes into the production environment. In home settings, end users may not even be aware of this issue. Wireless networks also face an increased risk of MitM types of eavesdropping and packet sniffing using devices that read captured data emanation across electromagnetic signals. Recently, with the proliferation of IoT devices, wireless DDoS attacks have become headline-making attacks of disruption. The configuration weaknesses of wireless connected devices permit attackers to insert malicious bots in things like DVRs, web cameras, intelligent personal assistant devices, and smartphones to create a botnet to send out almost limitless signals to bring down critical services and highly visible web targets.
To be properly prepared to deal with wireless networks, the security practitioner needs to understand the standards and protocols that govern wireless technology. They also need to understand the variety of technologies, techniques, and obstacles involved with securing wireless access points (WAPs) and wireless technology in general. This knowledge is essential in preparing them for adequately understanding how to address wireless attacks. The following sections will examine these topics in more detail.
NOTE When electrons move, they create emanations and a magnetic field. These data emanations can be picked up by devices that scan for them. Attackers use such devices to capture and re-create these emanations elsewhere to reproduce the electron stream on, for example, the attacker’s screen. The obvious result is that your data is exposed to the attacker.
Wireless Standards and Protocols
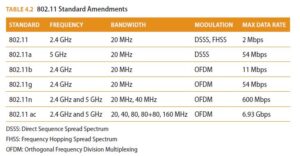
Wireless network communications are governed by the IEEE 802.11 standard. Evolutions of the standard are published through amendments that document updated versions of the original standard. These are highlighted in Table 4.2, and it should be noted that each version or amendment to the 802.11 standard has offered improved maximum data rates. 802.11x is often used to indicate all of the specific implementations as a collective whole, but that is not preferred over a general reference to 802.11.
Tip Do not confuse 802.11x with 802.1x, which is an authentication technology and not related to wireless.
Wired Equivalent Privacy (WEP) and WiFi Protected Access (WPA)
The IEEE 802.11 standard defines two methods that wireless clients can use to authenticate to WAPs before normal network communications can occur across the wireless link. These two methods are open system authentication (OSA) and shared key authentication (SKA).
- OSA provides no confidentiality or security because no real authentication is required. Communication happens if the radio signal is strong enough to reach a compatible receiver. All OSA transmissions are unecrypted.
- SKA enforces some form of authentication, and if the authentication isn’t provided, the communication is blocked. The 802.11 standard defines one optional technique for SKA known as Wired Equivalent Privacy (WEP), with subsequent amendments to the original 802.11 standard adding WiFi Protected Access (WPA), WPA2, and other technologies.
Wired Equivalent Privacy (WEP) was designed to protect against eavesdropping for wireless communications. The initial aim of WEP was to provide the same level of protection against MitM attacks that wired networks have. WEP implemented encryption of data in wireless transmissions using a Rivest Cipher 4 (RC4) symmetric stream cipher. Message integrity verification is possible because a hash value is used to verify that received packets weren’t modified or corrupted while in transit. It also can be configured to prevent unauthorized access. Incidentally, the knowledge or possession of the encryption key helps as a basic form of authentication. Without the key, access to the network itself is denied. WEP is used at the two lowest layers of the OSI model: the data link and physical layers. It therefore does not offer end-to-end security. Over time, WEP has been shown to have weaknesses. For instance, WEP uses static encryption keys, the same key used by every device on a wireless network. It is possible, therefore, that if an eavesdrop- per intercepted enough encrypted packets, the key could be deduced. In fact, WEP was cracked almost as soon as it was released. It takes less than a minute to hack through WEP protection.
To improve wireless security, a group known as WiFi Alliance developed a new encryption standard called WiFi Protected Access. As a replacement for WEP, WPA could be retrofitted to WEP firmware on wireless NICs designed for WEP already in the computing environment. That feature proved to be more problematic than it was worth. The changes to the WAPs were extensive, and hardware replacement was a better option.
WPA was intended as an interim solution until the IEEE published the promised 802.11i standard. That process lingered for years, so WPA was implemented independent of the 802.11 amendment. The WPA protocol implements the Lightweight Extensible Authentication Protocol (LEAP) and Temporal Key Integrity Protocol (TKIP), which support a per-packet key that dynamically generates a new 128-bit key for each packet.
WPA negotiates a unique key set with each host. It improves upon the WEP 64-bit or 128-bit encryption key that had to be manually entered on WAPs and devices and did not change. WPA uses LEAP and TKIP to perform Message Integrity Check, which is designed to prevent an attacker from altering and resending data packets. This replaces the cyclic redundancy check (CRC) that was used by the WEP standard. CRC’s main flaw was that it did not provide a sufficiently strong data integrity guarantee for the pack- ets it handled. Researchers have identified a flaw in WPA similar to the weaknesses in WEP. WPA often employs a static yet secret passphrase for authentication. A brute-force attack theoretically can result in a guessed passphrase. The likelihood of a sufficient pass-phrase (no fewer than 14 characters) succumbing to this attack is very low, but not impossible. Collaterally, the message integrity check hash function can then be exploited to retrieve the keystream from short strings of packets to use for injection attacks or spoofing. Basically, attacks specific to WPA—coWPAtty and a GPU-based cracking tool, to name two—have rendered WPA’s security unreliable. Both the LEAP and TKIP encryption options for WPA are now considered crackable using a variety of available and easy to use cracking techniques.
IEEE 802.11i or WPA2
The next evolution was WPA2, which replaced WPA. Originally, it was meant to replace WEP, but as mentioned before, the 802.11i standard lingered, and WPA was implemented independently. This amendment deals with the security issues of the original 802.11 standard. WPA2 is backward compatible to WPA. It provides U.S. government–grade security by implementing the National Institute of Standards and Technology (NIST) FIPS 140-2 compliant AES encryption algorithm and 802.1x-based authentications, and Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP). There are two versions of WPA2: WPA2-Personal and WPA2-Enterprise. WPA2-Personal protects unauthorized network access by utilizing a setup password. WPA2-Enterprise verifies network users through a server using Network Access Control (NAC).
The selection of the name WPA2 is because WPA was already published and in widespread use. However, WPA2 is not the second version of WPA. They are distinct and different. IEEE 802.11i, or WPA2, implemented concepts similar to IPSec to improve encryption and security within the wireless networks. As of 2018, no actual successful compromises have happened to a properly configured, encrypted WPA2 wireless net- work. That may be more at risk today, though. On October 16, 2017, security researchers disclosed several high-severity vulnerabilities in the WPA2 protocol. There was a proof- of-concept, called KRACK for Key Reinstallation Attacks, to demonstrate that attackers could eavesdrop on WiFi traffic. Devices running the Android, Linux, Apple, Windows, and OpenBSD operating systems, as well as MediaTek Linksys, and other types of devices, are all vulnerable. The good news is that patches have been made available, and no real-world attack was reported.
NOTE WPA3 is on the way. Announced by WiFi Alliance in January 2018, WPA3 was launched in June 2018. The new standard uses 192-bit encryption and individualized encryption for each user. WPA3 also promises weak password mitigation and simplified setup processes for devices with no human interface.
IEEE 802.1X
Both WPA and WPA2 support the enterprise authentication known as 802.1X/EAP, a standard NAC that is port-based to ensure client access control to network resources. Effectively, 802.1X is a checking system that allows the wireless network to leverage the existing network infrastructure’s authentication services. Through the use of 802.1X, other techniques and solutions such as RADIUS, TACACS, certificates, smart cards, token devices, and biometrics can be integrated into wireless networks providing techniques for multifactor authentication.
EAP (Extensible Authentication Protocol)
Extensible Authentication Protocol (EAP) is an authentication framework versus a specific mechanism of authentication. EAP facilitates compatibility with new authentication technologies for existing wireless or point-to-point connection technologies. More than 40 different EAP methods of authentication are widely supported. These include the wireless methods of LEAP, EAP-TLS, EAP-SIM, EAP-AKA, and EAP-TTLS. Two significant EAP methods that bear a closer look are PEAP and LEAP.
Tip EAP is not an assurance of security. For example, EAP-MD5 and a prerelease EAP known as LEAP are known to be vulnerable.
PEAP (Protected Extensible Authentication Protocol)
Using a TLS tunnel, Protected Extensible Authentication Protocol (PEAP) encapsulates EAP methods to provide authentication and, potentially, encryption. Since EAP was originally designed for use over physically isolated channels and hence assumed secured path- ways, EAP is usually not encrypted. So, PEAP can provide encryption for EAP methods.
LEAP (Lightweight Extensible Authentication Protocol)
Lightweight Extensible Authentication Protocol (LEAP) is a Cisco proprietary alternative to TKIP for WPA, but it should not be used. An attack tool known as Asleap was released in 2004 that could exploit the ultimately weak protection provided by LEAP. Use of EAP- TLS is preferred. If LEAP is used, a complex password is an imperative. LEAP served the purpose of addressing deficiencies in TKIP before the advent of 802.11i/ WPA2.
TKIP (Temporal Key Integrity Protocol)
TKIP was designed as the replacement for WEP without requiring replacement of legacy wireless hardware. TKIP was implemented into the 802.11 wireless networking standards within the guidelines of WPA. TKIP improvements include a key-mixing function that combines the initialization vector (IV) (i.e., a random number) with the secret root key before using that key with RC4 to perform encryption; a sequence counter is used to prevent packet replay attacks; and a strong message integrity check (MIC) is used.
CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol)
CCMP was created to replace WEP and TKIP/WPA. CCMP uses Advanced Encryption Standard (AES) with a 128-bit key. CCMP is the preferred standard security protocol of 802.11 wireless networking indicated by 802.11i. To date, no attacks have yet been successful against the AES/CCMP encryption. CCMP is the standard encryption mechanism used in WPA2.
NOTE The impact that security requirements can have on business and technology is not trivial. For instance, data encryption and filtering, like WPA2 and IPSec VPN, has to be tested and refined to optimal configurations to minimize any performance degradation.
Securing Wireless Access Points
WAPs are the devices within a physical environment that receive signals. Based on access control and required frequency values, these access points permit devices to connect.
Even with access controls and frequency settings, a security issue can result from a WAP that has a broadcast beacon that is set too powerfully and sends its beacon far beyond the necessary range. Whether broadcasting the beacon far away is seen as an advantage, say to roaming users, is a decision left to the company. This allows an unwanted wireless device to connect even if the end user is prohibited from accessing the physical area where the WAP is installed. In short, securing the WAP requires attention to proper placement of the device, shielding it, and limiting noise transmission while satisfying customer need to connect.
This section on how to secure WAPs assumes only that the need for wireless access is there, but no action has been taken to create it. Creating wireless access does not start with placing hardware arbitrarily. The first action to take is to conduct a site survey. A site survey is useful for assessing what, if any, wireless access exists currently. It also helps in planning for the future. Once the survey is complete, decisions on where to place wire- less access hardware can be made. This section also covers deciding on the correct type of antennas to broadcast from the chosen hardware.
Configuring your access points comes next. Configuration options follow the hard- ware sections. We first examine how the broadcast channels matter. Then there is discussion on what modes the hardware may be set to, such as whether to centralize the communication or form a type of transmission mesh. Additional consideration is given to how the network is broadcast and labeled, using service set identifiers (SSIDs). Finally, additional methods of securing access are covered, from the low-level filtering of MAC addresses to the higher-level use of captive portals.
Conducting a Site Survey
Site surveys are useful techniques for both identifying rogue access points and defining the placement, configuration, and documentation of access points.
Rogue WAPs are WAPs that are installed on an otherwise secure network with- out explicit authorization. Sometimes, a rogue access point is implemented by an employee for a perceived access or performance need. More concerning are cases where a malicious attacker installs a rogue access point to try to fool end users to try to connect. Such attacks harvest credentials or help launch DDoS attacks. It is import- ant for security personnel to conduct searches and scans to be on the lookout for these unwanted devices.
A physical walk-through, or site survey, is a way to discover rogue access points in the physical environment. During the site survey, security personnel investigate the presence, strength, and reach of WAPs deployed in an environment, while looking for unsanctioned signals. As the walk-through is conducted, a normal endpoint client with a wireless NIC can be used to simply detect signals. Another approach is to use one of a variety of wireless intrusion detection devices to scan the environment.
Site surveys also provide operational benefits, as the review helps define optimal placement and configuration and generate documentation for access points. Optimal placement and configuration consist of ensuring sufficient signal strength is available at all locations where access is desired. At the same time, where access is not wanted, like in public areas or outside of the facility, the signal availability should be minimized or eliminated. A site survey is useful for evaluating existing wireless network deployments, planning expansion of current deployments, and planning for future deployments.
Determining Wireless Access Placement
Using information determined by site surveys, the WAP locations are finalized. It is not recommended to commit to specific locations until the placements are informed by the walk-through. Conduct the proper testing of configurations and signal strength with multiple WAPs in place. There will most likely be movements and adjustments in this phase. Once an optimal configuration and location pattern is reached, make the locations permanent.
Here are some general considerations for wireless access placement:
- Use a central location.
- Avoid solid physical obstruction.
- Avoid reflective or other flat metal surface.
- Avoid the use of electrical equipment (interference).
- Position external omnidirectional antennas pointing vertically.
- Point a directional antenna toward the area of desired use.
An essential consideration for wireless technology is the impact of the environment on the broadcast signal. Wireless signals are impacted by various types of interference, physical and electromagnetic. Distance and obstructions are physical concerns. Electricity and other radio signals can conflict with or impede the effectiveness of the wireless signals. Network administrators will manipulate directional antennas and tune signal strength to accommodate the physical and electromagnetic obstacles to reach the desired areas of access.
A primary security concern for antennas is understanding how the lob pattern extends from the antenna. This is particularly true with directional antennas where the lob reaches far beyond the typical unidirectional antenna in one focused direction while being attenuated in the other directions. Even without special equipment, one can walk concentric circles around an access point and use a mobile device to measure radiation strength.
Antenna Types
The antenna is an integral component in wireless communication systems. The antenna transforms electrical signals into radio waves, and vice versa. Signal transmission requirements and reception quality dictate the choice of antenna from the various kinds avail- able. Standard antennas can be upgraded to signal-boosting, stronger antennas. Some of the most common types of antenna used are as follows:
- The standard straight, pole-dipole, or vertical antenna sends signals in all directions away from the antenna. This radiation pattern is omnidirectional and is the prevalent type of antenna on base stations and endpoint
- Many other types of antennas are directional. Instead of broadcasting in every direction, the signal is focused to one direction. Some examples of directional antennas include the following:
- Yagi: A Yagi antenna is crafted from a straight bar with crossbars to catch specific radio frequencies in the direction of the main bar.
- Cantennas: These are constructed from tubes with one sealed They focus along the direction of the open end of the tube.
- Panel antennas: These are flat devices that focus from only one side of the panel.
- Parabolic antennas: These are used to focus signals from very long distances or weak sources.
There are a few key antenna considerations with regard to securing the wireless network. Most importantly, recognize that directional antennas significantly extend the network’s reach in one focused direction. This is the case for both receiving and transmitting. Therefore, care must be taken in pointing directional antennas so the network’s visibility and vulnerabilities are not cast out too far. For choosing antennas and their placement, bear in mind how the broadcast extends well past walls and through floors, particularly when the organization is in a multitenant building.
Wireless Channels
Wireless signals are subdivided within a frequency range in increments called channels. These channels are like the lanes on a road or highway. There are 11 channels in the United States, there are 13 in Europe, and there are 17 in Japan. In the United States, the Federal Communications Commission (FCC) regulates the frequencies and has allocated 11. In the other countries and jurisdictions, the frequencies are regulated by national or the member states’ union and explains why there are differences in the number of frequencies.
Normally, a wireless connection is a communication signal between an endpoint client and a WAP. This occurs over a single channel. It is possible to have interference with devices on separate channels when two or more access points are located too closely together or the radio strength of WAPs is too high.
Security professionals should note that channel selection has little to no impact on mitigating wireless risks such as spoofing, jamming, or the visibility of the network. Instead, channels get chosen to minimize the interference between access points or other WiFi networks outside their control.
Tip Configure access points that are located near each other with a maximum channel separation. For instance, for four access points located within close proximity, channel settings could be 1, 11, 1, and 11 if the arrangement was linear, like along a hallway across the length of a building. However, if the building is square and an access point is in each corner, the channel settings may need to be 1, 4, 8, and 11.
Infrastructure Mode and Ad Hoc Mode
When deploying wireless networks, WAPs can be deployed in one of two modes: ad hoc or infrastructure. It is better to deploy the wireless access points configured to use infra- structure mode rather than ad hoc mode to enforce restrictions leveraged through WAPs. Ad hoc mode allows wireless devices to communicate without centralized control. Infra- structure mode prevents the devices or the NICs from interacting directly.
There are four distinct variants of infrastructure mode:
- Standalone: A WAP connects multiple wireless clients to each other but not to any wired resources.
- Wired extension: The WAP acts as a connection point, or hub, to link the wire- less clients to the wired network.
- Enterprise extended: Multiple WAPs, all with the same extended service set identifier (ESSID), are used to connect a large physical area to the same wired network. This allows for physical device movement without losing connection to the ESSID.
- Bridge: A wireless connection is used to link two wired networks, often used between floors or buildings when running cables or wires is infeasible or inconvenient.
Service Set Identifiers (SSIDs)
Anyone who has connected to a wireless network knows to ask for the network name, the technical term for an SSID. The SSID is that string of characters that identifies the wireless network. The SSID represents the logical wireless network, not the unique access point, as there can be multiple access points to provide coverage for multiple SSIDs.
There are two types of SSID, namely, ESSID and basic service set identifier (BSSID). An ESSID is the name of a wireless network in infrastructure mode when a wireless base station or WAP is used. A BSSID is the name of a wireless network when in ad hoc or peer-to-peer mode. In a scenario where multiple different base stations or WAPs are used in infrastructure mode, the BSSID is the MAC address of the base station hosting the ESSID to differentiate multiple base stations in the overall extended wireless network.
In securing the SSID wireless network, regardless of the types, note that the SSID is comparable to the name of a workgroup. When an endpoint client discovers an SSID, the wireless NIC is configured to communicate with the associated closest or strongest WAP. The SSID has secure access features so that discovery does not necessarily equate to access. There are additional steps before the client can communicate, such as enabling encryption and ensuring that discovered SSIDs are legitimate. With enabling encryption, the client is required to enter a password to permit access. Ensuring the legitimacy of the SSIDs that clients might see requires the organization to periodically monitor for rogue access points.
Tip It is important to reconfigure the SSIDs of new devices before deployment, as many default settings are supplied by the vendor and, therefore, widely and well known.
A step that can be taken to better secure WAPs is to disable the SSID broadcast of the beacon frame. A beacon frame is a special broadcast transmission that the SSID sends regularly from the WAP. Discovery by end user clients occurs as any wireless NIC finds this radio signal. In fact, with a detect and connect NIC feature, the connection can be automatic. Network administrators can disable, or silence, the broadcast. This is recommended as a security best practice. This makes connection a little more difficult, as the end user must know the SSID address to search. Keeping the beacon off and the SSID hidden is not foolproof. Attackers have tools to discover SSID via wireless sniffer technology to capture SSID information used in transmissions between wireless clients and the WAPs, as the SSID is still needed to direct packets.
Disabling SSID is a good first step. Hiding the existence of the network is a best practice, but it is not in itself sufficiently strong security. As with all defense in depth and layered security best-practice approaches, not broadcasting the SSID, coupled with using WPA2, will provide a reliable authentication and encryption solution with fewer failed attempts.
Using Captive Portals
Captive portals are authentication safeguards for many wireless networks implemented for public use, such as at hotels, restaurants, bars, airports, libraries, and so on. They are a common practice on wired networks, too. The process is to force a newly connected device to a starting page to establish authorized access. The portal may require input of credentials, payment, or an access code. It is also a good location to publish or provide a link to privacy policies and acceptable use terms and conditions. If end user consent for tracking and information collection is required, the captive portal allows for that as well. Once the end user satisfies the conditions required by the starting page, only then can they communicate across the network.
MAC Filters
A MAC filter is a whitelist or a register of authorized wireless client interface MAC addresses that is used by a WAP. Devices not on the list are blocked. The downsides are that the list is difficult to manage and does not scale to large environments with many changes.
There are two approaches to utilizing MAC filters. In one approach, someone, such as a network security analyst or a security professional tasked with securing wireless access, would determine through asset management what devices are permitted to connect. The other approach would be using a software solution such as intrusion detection. Some access point vendors offer such features, including the ability to detect MAC address spoofing to mitigate the risk of someone forging a known whitelisted MAC.
Wireless Attacks
In spite of increasing attention and capability for securing wireless networks, they are attractive targets for attackers. The types of attacks continue to grow, and many attacks are effective on wired networks as well as wireless ones. Attacks such as packet sniffing, MitM, and password theft are common to both wireless and wired networks and are discussed earlier in the chapter. A few types of attacks focus on wireless networks alone, like signal jamming attacks and a special collection of wireless attacks called war driving.
Signal jamming is the malicious activity of overwhelming a WAP to the extent that legitimate traffic can no longer be processed. Even though this is illegal in most places, there are inexpensive jamming products, like a TV jammer, available for sale online.
War driving is a bit of a play on words. The term has roots in a form of attack in the 1980s called war dialing, where computers would be used to make large numbers of phone calls searching for modems to exploit. War driving, in contrast, is when someone, usually in a moving vehicle, actively searches for WiFi wireless networks using wireless network scanning tools. These scanning tools and software are readily available and, far too often, free. When a wireless network appears to be present, the attacker uses the tools to interrogate the wireless interface or a wireless detector to locate wireless network signals. Once an attacker knows a wireless network is present, they can use sniffers to gather wireless packets for investigation. The next step in the attack is to discover hidden SSIDs, active IP addresses, valid MAC addresses, and even the authentication mechanism the clients use. MitM attacks may progress or the attackers may conduct advanced attacks with specialized tools, like AirCrack, AirSnort, and WireShark to attempt to break into the connection and gather additional important information. When using no security protocols or older ones, like WEP and WPA, attackers have very little difficulty being successful.
NOTE With the advancement of drones and the ability for private citizens to use them, a newer attack vector known as war droning is now a threat. Scanning and cracking activities are accomplished with a drone instead of by a person in a vehicle within proximity of the WAP.
War drivers often share the information they gather. Not all war driving attacks are meant to disrupt or be particularly malicious. It is likely the attackers are trying to simply get Internet access for free. Using the information they obtain from their own tools, they combine data with GPS information about location. Then they publish the information to websites like WiGLE, openBmap, or Geomena. Other people access the maps of various networks to find locations where they can hijack the wireless and access the Internet or conduct additional attacks.
There are no laws that prohibit war driving, although nothing specifically allows it either. Some consider it ethically wrong, but at a high level it is somewhat analogous to neighborhood mapping in the physical world with house numbers and phone numbers publicly listed. In fact, the reporting of war driving information on the Web could be considered an expanded version of what WAPs are meant to do: broadcast. However, as security professionals know, not all WAPs are broadcasting publicly, as they are hidden.
NOTE A real-life example helps underscore the duality of war driving as a potential attack vector, but also sometimes is a reasonable information-sharing act. Google systematically gathered WiFi information through video and mapping functions for its Street View service. The issue was Google’s lack of prior notice to the data collection, which created privacy concerns.


