CISSP Data Security Control in topic explain data states, data at reset, data in transit and data in use etc.
Data States
It is typically agreed upon that data and information can be in three basic states: data at rest, data in motion (transit), and data in use.
Understanding these three states and how information and data can be represented in each of the states can allow an organization to apply the security measures that are appropriate for its protection.
- Data at Rest: data stored on media in any type of It is at rest because it is not being transmitted or processed in any way.
- Data in Motion: data that is currently traveling, typically across a It is in motion because it is moving.
- Data in Use: data that is being processed by applications or It is in use because it is data that is currently in the process of being generated, updated, appended, or erased. It might also be in the process of being viewed by users accessing it through various endpoints or applications.
Data at Rest
The protection of stored data is often a key requirement for a company’s sensitive information. Databases, backup information, off-site storage, password files, and many other types of sensitive information need to be protected from disclosure or undetected alteration and availability. Much of this can be done through the use of cryptographic algorithms that limit access to the data to those that hold the proper encryption (and decryption) keys. Some modern cryptographic tools also permit the condensing, or compressing, of messages, saving both transmission and storage space, making them very efficient.
Data at Rest – Description of Risk
Malicious users may gain unauthorized physical or logical access to a device, transfer information from the device to an attacker’s system, and perform other actions that jeopardize the confidentiality of the information on a device.
Data at Rest – Recommendations
Removable media and mobile devices must be properly encrypted, following the guidelines below when used to store valuable data.
Mobile devices include laptops, tablets, wearable tech, and smartphones. Proper access controls and redundancy controls also need to be applied to protect data at rest.
Data in Transit
Data that moves, usually across networks, is said to be data in motion, or in transit. One of the primary needs of organizations today is to move data and information across various types of media, but the need is to prevent the contents of the message from being revealed even if the message itself was intercepted in transit.
Whether the message is sent manually, over a voice network, or via the internet, or any other network, including wireless networks, modern cryptography can provide secure and confidential methods to transmit data and allows the verification of the integrity of the message so that any changes to the message itself can be detected. Recent advances in quantum cryptography have shown that the “viewing” of a message can be detected while in transit.
Related Product : Personal Data Protection & General Data Protection Regulation Training & Certification
Link Encryption
Data are encrypted on a network using either link or end-to-end encryption. In general, link encryption is performed by service providers, such as a data communications provider on a Frame Relay network. Link encryption encrypts all of the data along a communications path (e.g., a satellite link, telephone circuit, or T-1 line).
Because link encryption also encrypts routing data, communications nodes need to decrypt the data to continue routing. The data packet is decrypted and re-encrypted at each point in the communications channel. It is theoretically possible that an attacker compromising a node in the network may see the message in the clear. Because link encryption also encrypts the routing information, it provides traffic confidentiality better than end-to-end encryption. Traffic confidentiality hides the addressing information from an observer, preventing an inference attack based on the existence of traffic between two parties.
End-to-End Encryption
End-to-end encryption is generally performed by the end user within an organization. The data are encrypted at the start of the communications channel or before and remain encrypted until decrypted at the remote end. Although data remain encrypted when passed through a network, routing information remains visible. An example of end-to-end encryption would be a virtual private network (VPN) connection.

Data in Transit – Description of Risk
The risks associated with data in motion are the same as those associated with data at rest. These include unauthorized disclosure, modification, and unavailability. Malicious actors may intercept or monitor plaintext data transmitting across network and gain unauthorized access that jeopardizes the confidentiality, integrity, and availability of the data.
Data in Transit – Recommendations
- Valuable data must be encrypted when transmitted across any network to protect against eavesdropping of network traffic by unauthorized users.
- In cases where source and target endpoint devices are within the same protected subnet, valuable data transmission must still be encrypted as recommended below due to the potential for high-negative impact of a valuable data breach. The types of transmission may include client-to-server and server-to-server communication, as well as any data transfer between core systems and third-party systems.
- Email is not considered secure and must not be used to transmit sensitive data unless additional email encryption tools are used. When attempting to secure data in transit, consider the following recommendations to design secure transmission of data:
– Where the sensitive device is reachable via web interface, web traffic must be transmitted over Secure Sockets Layer (SSL), using only strong security protocols, such as SSLv3, and Transport Layer Security 1 or v1.2 (TLS).
– Sensitive data transmitted over email must be secured using cryptographically strong email encryption tools such as PGP or S/MIME.
– Alternatively, prior to sending the email, user should encrypt sensitive data using compliant File Encryption tools and attach to email for transmission. - Non-web valuable data traffic should be encrypted via application-level encryption.
- Where an application database resides outside of the application server, all connections between the database and application should also be encrypted using FIPS-compliant cryptographic algorithms.
- Where application-level encryption is not available for non-web sensitive data traffic, implement network-level encryption such as IPSec or SSH tunneling.
- Encryption should be applied when transmitting valuable data between devices in protected subnets with strong firewall controls.
Data in Use
A particularly troublesome problem to protect is data in use. Data being processed is a perfect example of data in use. Typically, most architectures will need to process data in clear text, therefore, making it really difficult to protect data in use. While we may be able to protect data in motion and data at rest by using methods such as encryption, and access controls, data in use is very difficult to protect.
Data in Use – Recommendations
The industry has identified a potential solution to protecting data in use. This requires the implementation of secure enclaves where the processing would occur. Data would still be processed in clear text, but the concept of an enclave is that it would be isolated, or sectioned off, from the rest of the architecture so that it can protect anything in the enclave. This really means that we are isolating the enclave and its contents from the rest of the architecture and its components so that it cannot be affected by any vulnerabilities or malware that might exist in the architecture.
The definition of the word enclave does a really good job of explaining or at least visualizing how this might work. The definition of an enclave is a territory that is isolated or distinct from another territory. This implies we protect it from the other components of an architecture so that it cannot be viewed or accessed while processing data in use. But, as security professionals should always understand, nothing is perfectly secure, and there may be other vulnerabilities that would render this concept insecure as well, especially related to implementation issues.
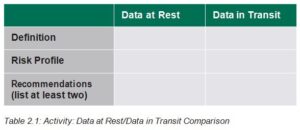
Activity: Data at Rest/Data in Transit Comparison
INSTRUCTIONS
Working with a partner, complete Table 2.1.
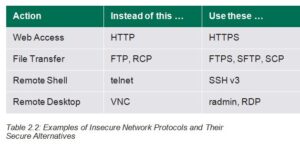
Examples of Insecure Network Protocols and Their Secure Alternatives
Picking Encryption Algorithms
When selecting algorithms to encrypt valuable data, keep these considerations in mind:
- Always choose the encryption algorithms that support longer key lengths as they generally provides stronger protection.
- Since passwords are often used to control the keys within the cryptosystem, long complex passphrases are stronger than shorter passphrases.
Wireless Connections
When connecting to wireless networks to access a system handling sensitive data, only connect to wireless networks employing cryptographically strong wireless encryption standards such as WPA2. Encryption mechanisms described in the section above must also be applied in addition to strong wireless network encryption to ensure end- to-end protection.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


