CISSP Asset Lifecycle in this topic explain classifications and categories which are applying in asset lifecycle.
Module Objectives
- Describe the asset lifecycle.
- Understand how data classification and categorization applies to the asset lifecycle.
The Asset Lifecycle
To protect assets properly, one must understand the asset lifecycle and apply protection mechanism throughout the phases of the asset lifecycle. The protection will always be based on the value of those assets at particular points in the lifecycle phases. This implies that the parties accountable and responsible for the protection of assets must understand and monitor the value of assets as they go through their lifecycle. Those in the best position to do this are the owners of those assets, or designates of the owners.
Understanding the data security lifecycle, enables the organization to map the different phases in the data lifecycle against the required controls that are relevant for each phase. The data lifecycle guidance provides a framework to map relevant use cases for data access, while assisting in the development and application of appropriate security controls within each lifecycle stage.
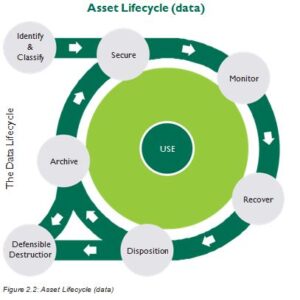
The Asset Lifecycle
To protect assets properly, one must understand the asset lifecycle and apply protection mechanism throughout the phases of the asset lifecycle. The protection will always be based on the value of those assets at particular points in that lifecycle. Figure 2.2 illustrates one example of the lifecycle phases. There are many other methodologies where there are more or less phases, or they might be named differently. Regardless, the point to be made here is that protection is required throughout the phases, and it is always based on the value of the assets at those particular moments in the lifecycle phases.
For example, according to the Securosis Blog, the lifecycle of data is depicted as having six phases: create, store, use, share, archive, and destroy. The Securosis Blog describes these phases as follows:
Create: Creation is the generation or acquisition of new content, or the iteration or updating of existing content. The creation phase is the preferred time to classify content according to its sensitivity and value to the organization. Careful classification is important since security controls will be based on that classification. Unless the classification is done correctly, poor security controls could be implemented if content is classified incorrectly. This is why the owners need to classify their assets; the owners are in the best position to understand the value of those assets to the organization, which is what the classification should be based on.
Store: Storing is the process of committing the data to some sort of storage media and in most cases happens at the same time as creation. When storing data, it should be protected in accordance with its classification level, and baseline controls, such as encryption, access controls, logging and monitoring, and redundancy, should be implemented to avoid risks.
Use: Data is accessed, viewed, processed, or used in some sort of way. Data in use is usually most vulnerable because it is probably in clear text at that point and may be transported into unsecure locations such as servers and workstations. To be processed, data must be unencrypted. Controls, such as data loss prevention (DLP), Digital Rights Management (DRM), and access controls, should be in place to protect the data in use and prevent unauthorized access.
Share: Information is shared with others, such as between users, to customers, and to partners, vendors, and other third parties. Not all data should be shared, and not all sharing should present a threat, but since data that is shared is no longer under the organization’s control, maintaining security can be most difficult. Data should only be shared based on its classification and only to those that are authorized for certain classifications. Technologies, such as DLP, can be used to detect unauthorized sharing, and DRM technologies can be used to maintain control over the information.
Archive: Data leaving active use may need to be stored long-term. Archiving data for a long period of time can be challenging, especially from a security perspective. Considerations of security through the archive period may affect data access procedures. The technology used may present challenges as well. Imagine if data is stored on some media and then needs to be retrieved a number of years later. Will the technology still exist to read the media? Data placed in archive must still be protected according to its classification level. Legal and regulatory requirements must also be addressed, and different tools and providers might be part of this phase and, therefore, may have shared responsibilities for the protection of archived information.
Destroy: The destruction phase can have different technical meanings according to usage, data content, and applications used. Data destruction can take many forms, from a simple delete or erase, to permanent data destruction using physical or digital means. As usual, consideration should be given according to value—the classification of the data.
Even though the phases described are those depicted in the Securoris Blog, the phases depicted in our diagram really focus on the security requirements as data moves through the different phases of its lifecycle. The phases depicted in our diagram are: identify and classify, secure, monitor, recover, disposition, archive, and defensible destruction. These phases imply the security requirements of each of these phases.
- Identify and classify: As information is created or collected, in other words created, it needs to be classified based on its This is done by the owner, who is always in the best position to understand the value.
- Secure: Once information is discovered or created and classified based on its value, it needs to be secured based on that Each of the classification levels specified in the organization’s classification system will dictate the protection requirements expressed as baselines. Baselines are minimum levels of security required for each of the classification levels used in the organization’s classification scheme.
- Monitor: Once information is secured based on its classification level, the security controls and the value of the asset needs to be monitored on a regular basis. Any change in the value, or the effectiveness of the security controls, will need attention to either increase or decrease the security controls. Security controls will always need to be cost-effective, based on the value being protected.
- Recover: Any impact to the value of the asset will require the ability to recover from those An impact could be a failure in the security control or an event that impacts the value of the asset, but regardless, it will require the ability to recover from that negative eventuality. This could be as simple as having the ability to backup and restore, or to activate redundant controls. The value of the asset and the risks to that value will always dictate the recovery capability required.
- Disposition: Once the useful life of the asset has been reached, the asset will need to be disposed Disposition can usually take two forms, either archiving (retention) or destruction. The decision of which method of disposition to be used can be dictated by several factors such as laws, regulations, policy, and value, etc.
- Archive: Archiving typically means long-term storage. Requirements may be dictated by several factors, all of which need to be carefully identified and understood to properly meet the retention requirements. Again, the owners are in the best position to understand these requirements and must be consulted to achieve the requirements of retention and archiving. Technology also must be addressed as there are requirements to have the information available far in the future, as well as possibly having to access the information at any time during its archiving period.
- Defensible destruction: Knowing when and how to destroy assets can be very problematic, and many companies will avoid this problem by keeping everything for a very long time. This is not a good option as this is neither efficient nor wise because protection of the information and the assets will still be required. Defensible destruction means eliminating and destroying assets, including information, in a quality controlled, regulatory-compliant, and legally defensible way. Every organization should have policies that address not only records retention and archiving, but also verifiable ways of destroying assets at the end of their lifecycle.
Related Product : EC-Council Security Analyst v10 | ECSA
Classification and Categorization
Most dictionaries will define the words classification and categorization as follows. Classification is the act of forming into a class or classes. This can be rephrased as a distribution into groups, as classes, according to common attributes. Whereas categorization is the process of sorting or arranging things into classes. This can be simplified as saying classification is the system, and categorization is the act of sorting into the classification system.
Classification
The purpose of a classification system is to ensure protection of the assets based on value in such a way that only those with an appropriate level of clearance can have access to the assets. Many organizations will use the terms “confidential,” “proprietary,” or “sensitive” to mark assets. These markings may limit access to specific individuals, such as board members, or possibly certain sections of an organization, such as the human resources (HR) area or other key areas of the organization.
Categorization
Categorization is the process of determining the impact of the loss of confidentiality, integrity, or availability of the information to an organization. For example, public information on a web page may be low impact to an organization as it requires only minimal uptime, it does not matter if the information is changed, and it is globally viewable by the public. However, a startup company may have a design for a new clean power plant, which if it was lost or altered may cause the company to go bankrupt, as a competitor may be able to manufacture and implement the design faster. This type of information would be categorized as “high” impact.
Classification and categorization is used to help standardize the protection baselines for information systems and the level of suitability and trust an employee may need to access information. By consolidating data of similar categorization and classification, organizations can realize economy of scale in implementing appropriate security controls. Security controls are then tailored for specific threats and vulnerabilities.
Data Classification and Policy
Data classification is all about analyzing the data that the organization has, in whatever form, determining its importance and value and then assigning it to a category or classification level. That category, or classification level, will determine the security requirements for protection of that valuable asset. For example, any data that is classified at the highest level, whether contained in a printed report or stored electronically, needs to be classified so that it can be handled and secured properly based on its classification. The requirements for classification should be outlined in a classification policy.
will determine the security requirements for protection of that valuable asset. For example, any data that is classified at the highest level, whether contained in a printed report or stored electronically, needs to be classified so that it can be handled and secured properly based on its classification. The requirements for classification should be outlined in a classification policy.
Data Classification Policy
When classifying data, determine the following aspects of the policy:
- Who will have access to the data: Define the roles of people who can access the Examples include accounting clerks who are allowed to see all accounts payable and receivable but cannot add new accounts and all employees who are allowed to see the names of other employees (along with managers’ names and departments, and the names of vendors and contractors working for the company). However, only HR employees and managers can see the related pay grades, home addresses, and phone numbers of the entire staff. And only HR managers can see and update employee information classified as private, including Social Security numbers (SSNs) and insurance information.
- How the data is secured: Determine whether the data is generally available or, by default, off In other words, when defining the roles that are allowed to have access, you also need to define the type of access—view only or update capabilities—along with the general access policy for the data. As an example, many companies set access controls to deny database access to everyone except those who are specifically granted permission to view or update the data.
- How long the data is to be retained: Many industries require that data be retained for a certain length of For example, many finance industries in countries may require specific retention periods. Data owners need to know the regulatory requirements for their data, and if requirements do not exist, they should base the retention period on the needs of the business.
- What method(s) should be used to dispose of the data: For some data classifications, the method of disposal will not But some data is so sensitive that data owners will want to dispose of printed reports through cross-cut shredding or another secure method. In addition, they may require employees to use a utility to verify that data has been removed fully from their PCs after they erase files containing sensitive data to address any possible data remanence issues or concerns.
- Whether the data needs to be encrypted: Data owners will have to decide whether their data needs to be encrypted. They typically set this requirement when they must comply with a law or regulation such as the Payment Card Industry Data Security Standard (PCI DSS).
- The appropriate use of the data: This aspect of the policy defines whether data is for use within the company, is restricted for use by only selected roles, or can be made public to anyone outside the organization. In addition, some data have associated legal usage definitions. The organization’s policy should spell out any such restrictions or refer to the legal definitions as required. Proper data classification also helps the organization comply with pertinent laws and regulations. For example, classifying credit card data as private can help ensure compliance with the One of the requirements of this standard is to encrypt credit card information. Data owners who correctly defined the encryption aspect of their organization’s data classification policy will require that the data be encrypted according to the specifications defined in this standard.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


