One of the first, and the best known, of the lattice security model was published by David Bell and Leonard LaPadula, which specifies the following three rules:
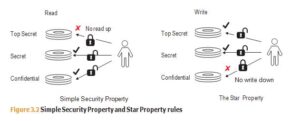
- Simple Security Property: Sometimes referred to as no read up, this rule prevents a subject from reading an object at a higher security level.
- Star Property: Sometimes referred to as no write down, this rule prevents a subject from writing to an object at a lower security level.
- Discretionary-Security Property: A subject can perform an operation on an object if permitted by the access matrix.
The Simple Security Property rule protects against unauthorized subjects accessing sensitive information that they are not permitted to read. The Star Property rule prevents an authorized subject from breaching security by writing sensitive information to an object at a lower security level.
Related Product : Computer Hacking Forensic Investigator | CHFI
For a real-world scenario, imagine an intelligence officer in the military who has “Secret” access, a mid-level classification between “Confidential” and “Top Secret.” According to the Simple Security Property rule, the officer can only read Secret and Confidential material. According to the Star Property rule, the officer can only write to Top Secret and Secret. The first rule doesn’t make unauthorized material accessible to the officer, while the second rule prevents the officer from accidentally revealing unauthorized material to staff with a lower clearance. Figure 3.2 provides a graphical view of these two rules.
The Discretionary-Security Property rule is useful when, for example, there are different departments. Let’s say our same officer can read Secret and Confidential in one department, but can only read Confidential in other departments. Likewise, other intelligence officers in various departments might have higher clearance levels for their respective areas, but not for all. In this case, the model allows for an access matrix, and the Discretionary-Security Property comes into effect.
An access matrix has a row for each subject and a column for each object, and the element in a cell where a subject row and object column intersect defines what operation (i.e. access), if any, is to be permitted. Table 3.1 provides an example of an access matrix.

The Discretionary-Security Property operates in conjunction with the other two mandatory access controls. The subject can only access the object if all three proper- ties hold.
There are two other issues that are not well addressed by the BLP model:
- The model focuses on confidentiality, as one would expect from a model developed to meet the requirements of military and government organizations. It does not consider risks to the integrity of information. Protecting the integrity of objects means preventing the unauthorized, possibly malicious, modification of an object. In the commercial world, preventing tampering with financial records, which could facilitate fraud, is more important than maintaining the confidentiality of those records.
- The model does not deal with covert channels. The possibility of performing permitted operations in a manner that reveals confidential information through side channels (e.g. by performing operations in a manner that can be detected by other, less secure, processes—such as consuming bursts of CPU, or forcing abnormal levels of VM paging).
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


