Cloud-based systems are those based on a pool of network-accessible servers and related resources that can be rapidly and programmatically provisioned and managed.
NIST SP 800-145 and ISO/IEC 17788 define a number of characteristics that distinguish cloud computing:
- Broad network access: Resources (physical and virtual) are accessible and man- aged over the network.
- Measured service: Users pay only for the services they use.
- On-demand self-service: Users can provision and manage services using auto- mated tools without requiring human interaction.
- Rapid elasticity and scalability: Services can be rapidly and automatically scaled up or down to meet demand.
- Resource pooling and multitenancy: Physical or virtual resources are aggregated to serve multiple users while keeping their data isolated and inaccessible to other tenants.
There are several service models as shown in Table 3.2.

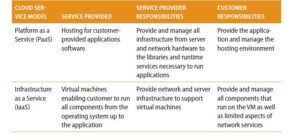
With each service model there is obviously a different division between the components supplied by the Cloud-Based System service provider and those provided by the customer. This gives rise to the cloud-shared responsibility model as illustrated in Figure 3.15. Security of cloud deployment is shared between the customer and the provider. The Cloud-Based System service provider is responsible for the security of the cloud, and the customer is responsible for the security in the cloud. This also means that one has to consider the security capabilities and commitments of the provider when assessing the risk of a cloud deployment.
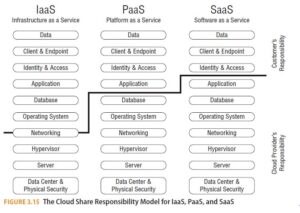
In particular, the cloud service provider is exclusively responsible for:
- Physical security
- Environmental security
- Hardware (i.e. the servers and storage devices)
- Networking (i.e. cables, switches, routers, firewalls, and Internet connectivity)
The cloud service provider and the customer share responsibility for:
- Vulnerability and patch management: Using Figure 15 as a guide to deter- mine which organization is responsible for which activities, the Cloud-Based System server provider is responsible for patching the software below the responsibility dividing line, the customer above (i.e in the case of SaaS, the customer is only responsible for the computers and browsers used to access the cloud).
- Configuration management: The cloud service provider is responsible for the infrastructure, the customer for everything above. Network configuration and security is a special case, as the customer of an IaaS provider typically has configuration control over significant aspects of the network routing and firewalls through APIs and web-based management consoles. As these network controls are a key component of the security of an IaaS clouds deployment, the customer must take great care in ensuring their proper
- Training: Both the Cloud-Based System provider and customer are responsible for the specific training required for their own personal.
In the IaaS situation, in which the customer has responsibility for many aspects of network security, providing perimeter and interior security requires a different approach from traditional data center security. In the clouds, the customer rarely has the ability to install actual networking or security devices (such as firewalls, routers, switches, and the like), but instead is given API access to a limited number of firewall and router functions that they can use to control access to their virtual machines. Also, depending on the clouds service provider, access to network traffic, as one might expect in a data center using a network tap or a SPAN (mirror) port, may or may not be available, or might be only available on a sampled basis such as NetFlow or sFlow.
Finally, cloud service can be deployed in a number of ways:
- Public cloud: Available to any customer
- Private cloud: Used exclusively by a single customer (may be in-house or run by a third party, on-premise or off)
- Community cloud: Used exclusively by a small group of customers (may be man- aged by one or more of the customers, or a third party, on-premise or off)
- Hybrid cloud: A combination of two or more of the above deployment models
The deployment model will have a significant effect on the nature of the risk assessment for the clouds deployment. That said, do not assume that private or on-premise clouds deployments are intrinsically more secure than public clouds. The major clouds providers have invested heavily in security, as attested to by their many security audits and certifications, and they can typically provide better security for their clients than those companies can for themselves.


