A firewalls is used to prevent unauthorized data flow from one area of the network to another. The boundary could be between trusted segments and the Internet or between other parts of a private network. In any case, a firewall creates a boundary and is employed to prevent or allow traffic from moving across that boundary.
The capabilities of a firewall can be accomplished with software, hardware, or both. Data coming into and out of the private network or internal segments must pass through the firewall. The firewall examines and inspects each packet and blocks those that do not match specified security criteria. These activities and some other network events are captured on firewall logs. Reviewing and auditing of logs are extremely valuable security tools that security professionals use for incident detection and response, forensic analysis, and improvement of the performance of the security assets.
The term firewall is used because the networking versions have a function similar to that of a firewall in a physical structure. A firewall in a building is a barrier meant to prevent or delay the spread of an actual fire. However, unlike a building firewall that suppresses all fire, a firewall in a systems environment is designed to permit approved traffic to transit between two environments.
For the network perimeter, firewalls are considered the first line of protection as part of an overall layered architecture. Elsewhere, firewalls, as noted earlier, are used to establish a boundary for any area and to separate and control traffic flow across that boundary. They are foundational to networking and one of the most prevalent security technologies used to protect information systems and networks. In terms of security due diligence, firewalls are essential. However, firewalls alone are not enough. For instance, they do not provide capabilities for authentication. Other types of devices and techniques are needed to complement firewalls. Without other devices and technologies in the security portfolio, firewalls become a single point of failure.
NOTE The expression “behind the firewall” describes traffic that flows within a subnet. Firewalls govern traffic from one subnet to another and do not protect from malicious data within the subnet.
Firewalls require configuration and human management, which is why security professionals must understand how to best use them. They do not automatically provide benefit. Besides any technical vulnerabilities that may be found, configuration and over- sight in firewall management help mitigate the risk of human error and misconfiguration. Security professionals have to configure filtering rules that define permitted traffic. These rules, be they to determine filtering or deny packets, make up the decision process of the firewall. For example, one firewall rule may say, “Drop all inbound packets routed with an internal source address.” Also important is how a firewall acts when it fails. If a firewall ceases to operate well, for example, it becomes overwhelmed, then the firewall optimally should fail “closed.” This means the firewall should not allow any packets through. To make sure the rules remain in place, the firewall must be protected against unauthorized change, and configurations must be kept current over time. Like any other device or endpoint, firewalls have vulnerabilities to be closed or patched, and security professionals also oversee the patching and upgrade procedures.
One of the most important roles of a security professional is to use the activity logs generated by firewalls. The logs should be analyzed for several types of events. Here are a few examples:
- The reboot or restart of a firewall
- Failure to start or a device crashing
- Changes to the firewall configuration file
- A configuration or system error while the firewall is running
- Unusual probes for access on ports
- Unsuccessful logins on devices
Tip Although the term can be used in other contexts about access control, the list of rules that govern a firewall is usually referred to as the access control list (ACL). An ACL contains specifications for authorized ports, protocols, list of permissions, IP addresses, URLs, and other variables to establish acceptable traffic.
Along with where a firewall is positioned, how they process and interrogate data differentiates types of firewalls. The principle of defense in depth applies here too. None of the different types of firewalls is sufficient alone. A combination is preferred.
Along with the variety of traditional firewalls that exist, there is the more recent next- generation firewall. There are also special firewalls such as multihomed and bastion firewalls. The following sections explore each of these, as well as firewall deployment architectures.
Types of Firewalls
There are four basic types of firewalls: static packet filtering firewalls, application level firewalls, stateful inspection firewalls, and circuit level firewalls. The key differentiator between all four firewalls is the OSI model layer at which each operates.
The first, a static packet filtering firewall, is the earliest and the simplest of firewall designs. Also called a screening router, the packet filtering firewall is the fastest design. Operating at the OSI model’s network layer, it inspects each packet. If a packet breaks the rules put in place, the packet is dropped and/or logged. Able to work most quickly, a packet filtering firewall will mitigate the risk of a particular packet type. This type of firewall offers no authentication mechanism and can be vulnerable to spoofing.
An application level firewall examines packets and network traffic with much more scrutiny than do packet filtering firewalls. Operating at the higher OSI model application layer, an application level firewall seeks to identify what kind of application traffic wants to cross the boundary. Often used as a separator between end users and the external network, the application level firewall functions as a proxy. Deep inspection takes time, making this firewall the slowest of all types.
The stateful inspection firewall is set apart from the key feature that differentiates it from a simple packet filtering firewall: a stateful firewall monitors the state of network connections. This firewall operates at the network and transport layers of the OSI model.
The connection state is based on how TCP operates and how TCP establishes a session through the “three-way handshake” discussed earlier. That state is kept track of, plus other connection attributes, such as destination and source details, are saved temporarily in memory. Over time, these details are used for smartly applying filters.
The circuit level firewall is functionally simple and very efficient, operating most like a stateful inspection firewall. The primary difference is this firewall works only at the session layer of the OSI model. For a circuit level firewall, the only task is to ensure the TCP handshaking is complete. No actual packet is inspected, nor would any individual packet be dropped. Traffic coming through a circuit level firewall will appear as if it originated from the gateway, since the circuit level firewall’s big benefit is to verify the session, while masking any details about the protected network.
Those four types of firewalls represent the span from the earliest to the most well- established firewall technology. But there is the next generation firewall, often referred to as the next-gen firewall (NGFW). The next generation firewall combines the traditional features of those earlier four with the advanced features of other network-based security devices such as an IDS or IPS. In the context of the OSI model, a next generation fire- wall operates at multiple levels.
Multihomed Firewalls
This is a general term for firewall or proxy capabilities. Multihomed describes having more than the default two interfaces or NICs providing the boundary. The host uses a set of software-defined rules to determine what traffic can pass between networks it is connected to, minimizing the risk of data being inadvertently exchanged between the two networks.
Bastion Host/Screened Host
A bastion host is so named for its resemblance to the medieval structure used as a first-layer protection guard house at the entry of a castle. In computing, it is a special-purpose type of firewall or host computer positioned logically behind the services of a core network routing device or in a DMZ. That router separates the internal, private network from an untrusted network, which can be the Internet. The terms bastion hosts and screened hosts are used interchangeably. They are also sometimes referred to as jump hosts. They act as a proxy, as the only device reachable from external sources. The bastion host adds a layer of protection by concealing the identities of the internal nodes. A bastion host will have a very limited number of applications, usually only one, to limit the possible impact of host compromise. Most commonly, the application is a proxy server to facilitate services and encapsulate data through the bastion host.
Types of bastion host applications include the following:
- DNS server: Like a phone book for the network, translates from its stored directory of domain names to the resolved IP address
- Email server: A virtual post office, stores inbound email for local distribution and sends out emails externally over SMTP, for example
- FTP server: Allows for the transfer of files over the Internet using an established sender and recipient connection, usually password-protected
- Proxy server: A general application that acts as an intermediary between an end- point device and another server
- VPN termination point: An endpoint for a VPN, to extend a private network across a public network
- Web server: Processes requests via HTTP, for instance, to transmit data across the World Wide Web
Firewall Deployment Architectures
A screened subnet is a combination of bastion hosts. The basic architecture distinctly separates public and private segments. On the private intranet, the local computers and system are located behind a protective device or application, screening them from public access. On the other segment, public services like web servers and proxy servers are accessible. The subnets are helpful for increased security and can improve performance in data throughput.
In today’s complex computing environment, a single firewall in line between the untrusted and the private networks is almost always insufficient. There are some basic implementations for a firewall connected to a router to direct traffic to the Internet. How- ever, it is best practice to eliminate the reliance on a single firewall.
To improve protection and performance among and between subnets and externally to untrusted networks, organizations use multiple firewalls in combination. Figure 4.9 illustrates an example of the hybrid deployment of firewalls at different networking tiers of the private LAN.
The use of a two-tier design introduces the DMZ or an extranet for business-to-business (B2B) purposes. Another purpose is to differentiate between semitrusted partners, such as between a company and its governmental partners. There are two distinct versions of the two-tier model, a multihomed version and a serial version.
The first deployment architecture uses one firewall that has three or more interfaces.
In a firewall with multiple interfaces, one of the interfaces leads to the DMZ.
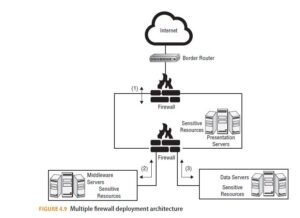
The second version consists of two firewall devices in a direct transactional line with each other. In the inline version, the DMZ is between the two serial firewalls. When using the DMZ, information server systems, e.g., web servers, are accessible to authorized external users. Otherwise, the firewall directs authorized traffic to the trusted network based on filtering rules or access control lists.
The most secure and most complex design is a three-tier deployment architecture. In this design, multiple subnets are established between the private network and the Internet through the use of individual firewall devices. As data traverses through each subnet, it meets progressively more stringent filtering rules at each firewall. This increases the chance that only authorized traffic reaches the trusted sources and the most critical assets. Access to the DMZ occurs at the outermost subnet. The first firewall may be a reverse proxy. The systems or data servers that support complex web applications and other transactions operate within the second or middle subnet. The private network is protected directly by the third.
There is a significant operational impact when employing the more complex architectures. The cost of deploying and managing the multiple tiers is a consideration to balance against the value of the assets. With the complexity and significant management requirements, the risk of firewall misconfiguration is something that requires ongoing attention. In this way, the devices that protect the environment become the vulnerability through human error.
Today, these firewall models are not the steadfast solution that they once were. Cloud services have been disruptive to the typical firewall architecture. While firewall models and architectures have been around for years, cloud services are fast becoming common, and corporate dependency on the cloud dictates how protected network traffic moves through the public Internet. One solution is using what Amazon Web Services (AWS) calls security groups. AWS security groups (SGs) are a type of firewall instance per virtual private cloud (VPC) or the virtual networking space people using AWS use to define their VMs.
Another approach is offering a firewall as a service (FWaaS), much like cloud service providers offer software as a service (SaaS). With FWaaS, filtering or screening packets are done virtually and off-site. FWaaS obviously requires more than your average trust in the cloud service provider, but its benefits include dedicated management in terms of updates, configuration, and enforcing your agreed-upon rules and policies.
Software-defined networking also presents disruption to traditional firewall architectures. SDN makes managing a network more flexible. This is largely seen as a feature and an advantage for networking engineers. However, SDN also makes maintaining firewall requirements more fluid, which can be a disadvantage. Again, SDN and cloud services have significantly affected how firewall services can be implemented.


