Risk Assessment Methodologies
There are dozens of risk assessment methodologies. Many are specific to industry sectors, such as government or software development. Still others differentiate themselves through their emphasis on either a quantitative or qualitative method. For the CISSP, a foundational understanding of risk assessment methods is necessary.
At its core, risk assessment is a formal determination of the likelihood and impact of an event relative to an asset. Typically conducted as a method of identifying and prioritizing the controls necessary to bring the risk to an acceptable level, the assessment process varies greatly depending on the framework, asset being protected, and desired outputs of the risk assessment process.
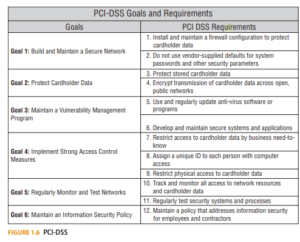
One of the most widely used risk assessment methodologies is the process characterized in NIST 800-30, “Guide for Conducting Risk Assessments.” (See Figure 1.7.)
The first step in the four-step process is to properly frame the risk. To initiate the process, a number of inputs from the risk management strategy are necessary. This includes an understanding of the organization’s risk tolerance, the scope of the assessment, any assumptions or constraints that would affect the assessment, the organization’s preferred methods of risk response, the processes for managing communications with stakeholders, and other information to conduct the risk assessment process in the context of the organization’s practices.
Related Product : ISO 31000 Risk Management | Certified Risk Manager
The second step in the process is to conduct the assessment. Four major activities will be performed to fully evaluate risk. Enumeration of the threats to the system must be undertaken, taking into account the threat’s means and motivations. The threats could be actors or events, but their relevance to the system and the organization is an essential input to the subsequent prioritization of control activities.
Identification of vulnerabilities is also performed. Vulnerabilities are weaknesses that a threat could potentially exploit. Identification and enumeration of potential vulnerabilities allows the organization to assess their severity. This leads to the identification of necessary predisposing conditions, which may affect the actual presentation of the vulnerability to the threat actor.
The NIST process explicitly recognizes the relationship between the threats and the vulnerabilities. A single threat event might exploit multiple vulnerabilities. A single vulnerability might be exploited by multiple threats. Regardless, the size and complexity of the environment require that the risk assessment processes be conducted across multiple levels—tiers—to address uncertainty at the organizational, mission/business process, and information systems levels.
Once the threats and weaknesses are known, the likelihood and impact of the threat actually exploiting the vulnerability are evaluated. Existing and planned countermeasures may affect the likelihood or impact and thus affect the eventual determination of the level of risk. Ultimately, in this step, the level of risk is determined through the evaluation of the likelihood and consequence of a particular threat exploiting a specific vulnerability. These activities, while they are often presented in a linear fashion to simplify explanation of the concepts, are often iterative and recursive. An identified vulnerability may reveal new potential threats. Part of the challenge in conducting assessments is placing constraints around the planning process to minimize “paralysis by analysis.” The third step in the process is to effectively communicate to stakeholders throughout the risk assessment process. Communication between organizational stakeholders must take into account the organization’s communication and reporting requirements to ensure that decision-makers have sufficient information on which to act. Further communication to a variety of other stakeholders inside and outside the organization should also
occur, consistent with organizational policies and guidance.
The fourth step in the process is to maintain the assessment. This includes monitoring the level of risk based on changes to the risk factors (threat sources and events, vulnerabilities and predisposing conditions, capabilities and intent of adversaries targeting the organizational operations, assets, or individuals) and communicating the changes in the risk appropriately in the organization. The activities in this step overlap processes identified in other parts of the NIST Risk Management Framework. This overlap is intended to explicitly recognize the integrated and holistic nature of the NIST 800 series processes.
Although there are many excellent risk management and risk assessment processes to choose from, it is more important to consistently apply risk practices across the organization. Consistent application and execution ensures that everyone knows what their role is relative to the risk activities and supports the evaluation and prioritization of risk. The security professional should be exposed to multiple methodologies to shape the risk management processes of their organization to meet the unique requirements of their business.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


