The Brewer-Nash model was developed to implement an ethical wall security policy. In the commercial world there are regulatory requirements designed to prevent conflicts of interest arising from insider knowledge. These rules require that organizations establish barriers to prevent those with confidential information from being placed in a position where that knowledge could improperly influence their actions.
Note In the original Brewer-Nash paper the term “Chinese Wall” was used. This term is deprecated in favor of “ethical wall” or “cone of silence.”
For example, a financial analyst working for a bank cannot provide advice for a client company when he has insider knowledge related to another client who is a competitor. Similarly, in countries in which a law firm is permitted to represent adversarial clients, the regulations require an ethical wall to exist between the two legal teams within the same company.
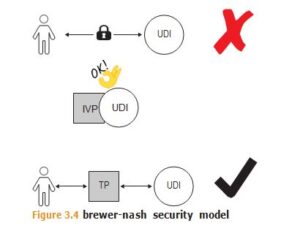
Recall that in the BLP security model, access to data is determined based on attributes of the subject and the object. In contrast to BLP, the Brewer-Nash security model is based on segregation of duties, hence, the visual of erecting an ethical wall. Access to the data must be limited by what data the person is already permitted to access.
Related Product : Computer Hacking Forensic Investigator | CHFI
The Brewer-Nash model defines a hierarchical model for information:
- Individual pieces of information related to a single company or client are called objects in keeping with BLP’s usage.
- All objects related to the same company (or client) are part of what is called a company data set.
- All company data sets in the same industry (i.e. that are competitors) are part of what is called a conflict of interest class.
The objective of an ethical wall security policy is that people are only permitted to access information (objects) that does not conflict with information they already have access to.
For example, let’s say a new financial analyst who has not accessed any information held by his newer employer and therefore, under Brewer-Nash (BN), is free to access any company data set. The analyst already accessed ACME Finance information, and he is free to access information that exists in a different conflict of interest class, say, BETA Chemicals. But if he tries to access an object associated with Ajax Finance, which is in the same conflict of interest class as ACME, the BN security model would bar that access. See Figure 3.4.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


