Threat Modeling Methodologies
There are three general approaches to threat modeling. Different risk methodologies, compliance frameworks, or systems prefer one or another, but the security professional should be able to apply all three approaches to a particular environment.
- Attacker-centric: This threat modeling approach starts by identifying the various actors who could potentially cause harm to a system. This approach can be helpful when narrowly approaching a problem by limiting the number of scenarios under analysis. Tactical military intelligence is typically driven by an attacker centric threat model, as are many business continuity/disaster recovery planning processes. As a result, many people have had experience with this form of threat modeling elsewhere in their professional lives. This approach is often helpful when the analysis is being conducted by nontechnical professionals, as capturing the means, methods, and motivations of the attackers to build a profile (or persona) of an attacker encourages active engagement.
- Asset-centric: As opposed to an attacker-centric approach, an asset-centric threat model identifies the assets of value first. The value of the asset should be characterized by the value of the asset to the organization and the value of the asset to the attacker. The means by which the asset is managed, manipulated, used, and stored are then evaluated to identify how an attacker might compromise the asset. Many compliance regimes focus on protection of an asset (e.g., protected health information under HIPAA, personally identifiable information under the GDPR, or the Primary Account Number under PCI-DSS), so this approach is helpful when establishing or verifying compliance. Tools that supports asset-centric analysis include classification and categorization of information, identifying information that is sensitive to disclosure, and the importance of the information to the organization’s business processes. As is done with the attacker-centric model, organizations typically maintain an inventory or library process to identify those assets of value.
- System (Software)-centric: For many information systems environments, the system- or software-centric model is most useful. In this approach, the system is represented as a set of interconnected processes, often using DFDs as mentioned. These diagrams are then evaluated by the analysts to determine whether control is necessary, exists, and achieves the control effect. Clarifying trust boundaries is essential to define, as the level and type of control changes as information transits the boundary.
There are many different threat modeling methodologies. Some of the most widely used are STRIDE, NIST 800-154, PASTA, and OCTAVE, each of which are explored next.
Related Product : Certified Threat Intelligence Analyst | CTIA
STRIDE
Microsoft developed the STRIDE methodology in the late 1990s as a way to standardize the identification of threats across their product line. Given the popularity of the Microsoft tools, the approach found wide acceptance within the development community. STRIDE is a classic software-centric threat model. The acronym STRIDE is a mnemonic for spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege. When evaluating an interaction between processes, these six threats to a system’s CIA state are reviewed. Finally, this model has been influential in the development of other models, notably the OWASP threat modeling process. This model is more fully discussed in Chapter 8.
NIST 800-154 Data-Centric Threat Modeling
In 2016, NIST placed for public comment a threat modeling approach centered on protecting high-value data. This approach is known as NIST 800-154, “Data-Centric Threat Modeling.” It explicitly rejects that best-practice approaches are sufficient to protect sensitive information, as best practice is too general and would overlook controls specifically tailored to meet the protection of the sensitive asset. In this model, the analysis of the risk proceeds through four major steps.
- Identify and characterize the system and data of interest. The data and information should be defined narrowly to a particular logical set of data on a single host or small group of hosts. Then the information is characterized, taking into account the authorized locations for the data within the system, how the information moves within the system between authorized locations, the security objectives for the data using the CIA construct, recognizing that not all of the objectives are of equal importance for a particular data set, and then defining the people and processes that are authorized to access the data within the context of the security objectives.
- Identify and select the attack vectors to be included in the model. Identify potential attack vectors and then prioritize those that meet the likelihood and consequence criteria established for the data or system.
- Characterize the security controls for mitigating the attack vectors. Identify the security control alterations that would address the risk and are reasonably feasible to accomplish. Next, for each selected control alteration, estimate the effectiveness of the control on the attack vector. Finally, estimate the negative consequences of the control, taking into account issues such as cost, functionality, usability, and performance.
- Analyze the threat model. Taking into account the characteristics documented in the previous steps, evaluate the controls to identify which controls give an acceptable level of risk reduction while minimizing the negative impacts of the control. Most data-centric models emphasize one of the aspects of the CIA Triad over the others. In the case of national security information, confidentiality would receive more weight. In the case of information regarding hurricane forecasting, confidentiality might be low on the list of interests, but integrity and availability of the information might be of greater importance.
The Process for Attack Simulation and Threat Analysis
The Process for Attack Simulation and Threat Analysis (PASTA), as the full name implies, is an attacker-centric modeling approach, but the outputs of the model are focused on protecting the organization’s assets. Its seven-step process aligns business objectives, technical requirements, and compliance expectations to identify threats and attack patterns. These are then prioritized through a scoring system. The results can then be analyzed to determine which security controls can be applied to reduce the risk to an acceptable level. Advocates for this approach argue that the integration of business concerns in the process takes the threat modeling activity from a technical exercise to a process more suited to assessing business risk.
Operationally Critical Threat, Asset, and Vulnerability Evaluation
Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) is an approach for managing information security risks developed at the Software Engineering Institute (SEI). While the overall OCTAVE approach encompasses more than threat modeling, asset-based threat modeling is at the core of the process. In its current form, OCTAVE Allegro breaks down into a set of four phases with eight steps. (See Figure 1.8.)
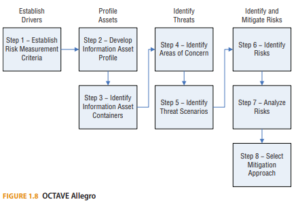
These are the four phases of OCTAVE Allegro:
- Establish drivers, where the organization develops risk measurement criteria that are consistent with organizational drivers.
- Profile assets, where the assets that are the focus of the risk assessment are identified and profiled and the assets’ containers are identified.
- Identify threats, where threats to the assets—in the context of their containers—are identified and documented through a structured process.
- Identify and mitigate risks, where risks are identified and analyzed based on threat information and mitigation strategies are developed to address those risks.
As compared with previous versions of OCTAVE, Allegro simplifies the collection of data, improves focus on risk mitigation strategies, and provides a simple quantitative model (as opposed to the qualitative approaches previously emphasized). Proponents argue that this makes the model easier to understand and use, simplifying training and increasing the likelihood that the approach will be consistently adopted as a risk method inside organizations.
Other Models
Other threat modeling methodologies include the following:
- TRIKE is an open source threat modeling approach and tool.
- Construct a platform for Risk Analysis of Security Critical Systems (CORAS), also open source, relies heavily on UML as the front end for visualizing the threats.
- Visual, Agile, and Simple Threat Modeling (VAST) is a proprietary approach that leverages Agile concepts.
- Implementing a structured threat modeling program allows an organization to consistently identify and characterize the threats it faces and then apply appropriate control to the risks.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


