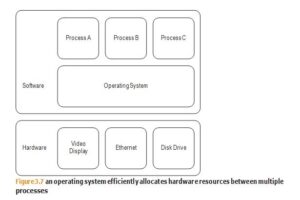
In CISSP Virtualization process is the operating systems provide programs with a set of services to enable them to operate more efficiently (and to be more easily designed and run) than if the program had to run on the computer directly. For example, instead of an application reading and writing disk storage blocks directly, the operating system provides a level of abstraction that manages the details of files and directories. Furthermore, most operating systems also enable multiple programs to run concurrently, with each application able to operate oblivious to the presence of other apps on the same system.
In some sense, an operating system provides a type of virtual computer, a computer that does not exist in reality (i.e. hardware) but which is much easier for applications to use than the physical hardware, and which makes more efficient use of the hardware by sharing it among different programs (see Figure 3.7).
CISSP Virtualization takes this concept a step further. Instead of just one operating system enabling multiple application programs running on the same hardware, a hypervisor makes use of a set of specific processor instructions and features to emulate an entire computer. This enables multiple operating systems to run on the same computer, each unaware of and unable (in a properly designed hypervisor) to affect the other operating systems.
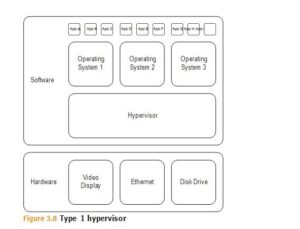
There are two types of hypervisors, commonly referred to as Type 1 and Type 2 hyper- visors. The primary difference between them is whether an underlying operating system is used to bridge the hardware with the virtual machines. A Type 1 hypervisor is the sole installation, acting as a bridge between hardware components and virtual machines, as illustrated in Figure 3.8. For this reason, Type 1 hypervisors are also called “bare metal” hypervisors. They are commonly found when flexibility and efficiency are most required. This is especially the case when the virtualized servers are running the same or similar services, making the most efficient use of the underlying hardware. In production environments, you are more likely to find virtualized machines sitting on Type 1 hypervisors. With a bit more overhead comes the Type 2 hypervisor, relying on a “host” operating system installed on the hardware. The virtualized machines running within the host OS are then called “guest” machines.
CISSP Virtualization is the foundation upon which Infrastructure-as-a-Service (IaaS) cloud providers such as AWS or Google provide virtual machines to different clients who may well end up running on the same physical computer, unknown to each other.
Related Product : Certified Information System Security Professional | CISSP
The advantages of virtualization include:
- More efficient use of the underlying hardware (just as operating systems permitted a single computer to be shared by multiple programs and users)
- Dynamic scaling of infrastructure in response to demand
- Additional separation and isolation between programs and applications running on different operating systems (as opposed to running on the same OS) — supporting the security principles of defense in depth and layers of security outlined earlier
Potential Weaknesses
As with memory protection, virtualization depends on the correct operation of both the hardware and the hypervisor. Hardware defects such as Meltdown break the underlying assumption that the hardware will prevent an unauthorized program (and possibly a completely unrelated client) from accessing memory assigned to another pro- gram (and client).
Similarly, software defects in hypervisors can improperly permit software running on one virtual machine to access data on a different virtual machine on the same computer. When such defects are discovered, they are usually responsibly disclosed to the largest cloud service providers so that they can be patched before the vulnerability becomes widely known.
There is always the possibility that these unpatched defects in the hardware or hypervisor might be known to a threat actor who is then able to compromise the protections that are supposed to prevent unrelated clients on virtual machines from interacting. To mitigate this risk, some IaaS cloud providers offer dedicated hosts which guarantee that only virtual machines assigned to your account will be permitted to run on the dedicated host.
Follow Us
https://www.facebook.com/INF0SAVVY
https://www.linkedin.com/company/14639279/admin/


