Introduction to Popular TCP/IP Applications in this article throughout your preparation for the CCNA Routing and Switching exams, you’ll come across a variety of TCP/IP applications. you ought to a minimum of remember of some of the applications which will be wont to help manage and control a network.
The World Wide Web (WWW) application exists through web browsers accessing the content available on web servers. Although it’s often thought of as an end-user application, you’ll actually use WWW to manage a router or switch. You enable an internet server function within the router or switch and use a browser to access the router or switch. The domain name System (DNS) allows users to use names to ask computers, with DNS getting used to seek out the corresponding IP addresses. DNS also uses a client/server model, with DNS servers being controlled by networking personnel and DNS client functions being part of most any device that uses TCP/IP today. The client simply asks the DNS server to provide the IP address that corresponds to a given name. Simple Network Management Protocol (SNMP) is an application layer protocol used specifically for network device management. for instance , Cisco supplies a large sort of network management products, many of them within the Cisco Prime network management software package family. they will be wont to query, compile, store, and display information about a network’s operation. to question the network devices, Cisco Prime software mainly uses SNMP protocols. Traditionally, to maneuver files to and from a router or switch, Cisco used Trivial File Transfer Protocol (TFTP) . TFTP defines a protocol for basic file transfer—hence the word trivial. Alternatively, routers and switches can use File Transfer Protocol (FTP), which may be a far more functional protocol, to transfer files. Both work well for moving files into and out of Cisco devices. FTP allows more features, making it an honest choice for the overall end-user population. TFTP client and server applications are very simple, making them good tools as embedded parts of networking devices.
Also Read : Introduction to TCP/IP Networking
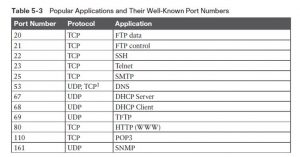
Some of these applications use TCP, and a few use UDP. for instance , Simple Mail Transfer Protocol (SMTP) and Post Office Protocol version 3 (POP3), both used for transferring mail, require guaranteed delivery, in order that they use TCP. no matter which transport layer protocol is employed , applications use a well known port number in order that clients know which port to aim to attach to. Table 5-3 lists several popular applications and their well-known port numbers.

Connection Establishment and Termination
TCP connection establishment occurs before any of the opposite TCP features can begin their work. Connection establishment refers to the method of initializing Sequence and Acknowledgment fields and agreeing on the port numbers used. Figure 5-5 shows an example of connection establishment flow.

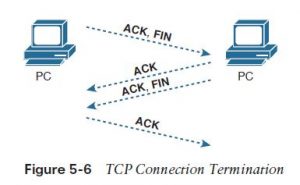
This three-way connection establishment flow (also called a three-way handshake) must complete before data transfer can begin. The connection exists between the 2 sockets, although the TCP header has no single socket field. Of the three parts of a socket, the IP addresses are implied based on the source and destination IP addresses within the IP header. TCP is implied because a TCP header is in use, as specified by the protocol field value within the IP header. Therefore, the only parts of the socket that require to be encoded within the TCP header are the port numbers. TCP signals connection establishment using 2 bits inside the flag fields of the TCP header. Called the SYN and ACK flags, these bits have a very interesting meaning. SYN means “synchronize the sequence numbers,” which is one necessary component in initialization for TCP. Figure 5-6 shows TCP connection termination. This four-way termination sequence is simple and uses a further flag, called the FIN bit. (FIN is short for “finished,” as you would possibly guess.) One interesting note: Before the device on the proper sends the third TCP segment within the sequence, it notifies the appliance that the connection is coming down. It then waits on an acknowledgment from the application before sending the third segment within the figure. Just just in case the application takes a while to reply, the PC on the proper sends the second flow within the figure, acknowledging that the opposite PC wants to require down the connection. Otherwise, the PC on the left might resend the primary segment repeatedly.
TCP establishes and terminates connections between the endpoints, whereas UDP doesn’t . Many protocols operate under these same concepts, therefore the terms connection-oriented and connectionless are wont to ask the overall idea of every . More formally, these terms are often defined as follows :
- Connection-oriented protocol: A protocol that needs an exchange of messages before data transfer begins, or that features a required pre-established correlation between two endpoints.
- Connectionless protocol: A protocol that doesn’t require an exchange of messages which doesn’t require a pre-established correlation between two endpoints.
Questions related to this topic
- Does DNS use TCP or UDP?
- Which protocol is used by DNS?
- What is TCP 53 used for?
- What is TCP over IP?
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



Great article very useful information and easy to understand thanks a lot.