Jason, an attacker, targeted an organization to perform an attack on its Internet-facing web server with the intention of gaining access to backend servers, which are protected by a firewall. In this process, he used a URL https://xyz.com/feed.php?url=externalsite.com/feed/to to obtain a remote feed and altered the URL input to the local host to view all the local resources on the target server. What is the type of attack Jason performed in the above scenario?
Option 1 : Web cache poisoning attack
Option 2 : Sever-side request forgery (SSRF) attack
Option 3 : Web server misconfiguration
Option 4 : Website defacement
1. Web cache poisoning attack
Web cache poisoning is an advanced technique whereby an attacker exploits the behavior of a web server and cache so a harmful http response is served to different users.
Fundamentally, web cache poisoning involves 2 phases. First, the attacker should work out the way to elicit a response from the back-end server that how to contains some reasonably dangerous payload. Once successful, they have to make sure that their response is cached and intended served to the intended victims.
A poisoned web cache will potentially be a devastating means of distributing varied different attacks, exploiting vulnerabilities like XSS, JavaScript injection, open redirection, and so on.
How will a web cache work?
To understand how web cache poisoning vulnerabilities arise, it’s important to have a basic understanding of however web caches work.
If a server had to send a new response to each single HTTP request severally, this may likely overload the server, leading to latency issues and a poor user expertise, particularly during busy periods. Caching is primarily a method of reducing such and the.
The cache sits between the server and therefore the user, wherever it saves (caches) the responses to specific requests, typically for a fixed amount of time. If another user then sends without any request, the cache simply serves a replica of the cached response on to the user, without any interaction from the back-end. This greatly eases the load on the server by reducing the number of duplicate requests it’s to handle.
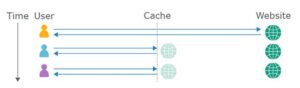
Cache keys
When the cache receives an http request, it first has to verify whether there’s a cached response that it will serve directly, or whether or not it’s to forward the request for handling by the back-end server. Caches identify equivalent requests by comparing a predefined set of the request’s components, known collectively because the “cache key”. Typically, this might contain the request line and Host header. elements of the request that are not included within the cache key are said to be “unkeyed”.
If the cache key of an incoming request matches the key of a previous request, then the cache considers them to be equivalent. As a result, it’ll serve a copy of the cached response that was generated for the original request. this applies to all subsequent requests with the matching cache key, till the cached response expires.
Crucially, the other elements of the request area unit ignored altogether by the cache. We’ll explore the impact of this behavior in more detail later.
What is the impact of a web cache poisoning attack?
The impact of net cache poisoning is heavily dependent on 2 key factors:
- What exactly the attacker will successfully get cached
As the poisoned cache is more a way of distribution than a standalone attack, the impact of net cache poisoning is inextricably linked to however harmful the injected payload is. like most types of attack, net cache poisoning may also be used in combination with alternative attacks to step up the potential impact even additional.
- The quantity of traffic on the affected page
The poisoned response can only be served to users who visit the affected page whereas the cache is poisoned. As a result, the impact will range from non-existent to large reckoning on whether the page is well-liked or not. If AN wrongdoer managed to poison a cached response on the home page of a major web site, for example, the attack might affect thousands of users with none subsequent interaction from the a major.
Note that the length of a cache entry doesn’t necessarily affect the impact of net cache poisoning. an attack will sometimes be scripted in such a way that it re-poisons the cache indefinitely.
2. Sever-side request forgery (SSRF) attack
Server-side request forgery (also called SSRF) is a net security vulnerability that allows an assaulter to induce the server-side application to make http requests to associate arbitrary domain of the attacker’s choosing.
In typical SSRF examples, the attacker might cause the server to make a connection back to itself, or to other web-based services among the organization’s infrastructure, or to external third-party systems.
Another type of trust relationship that often arises with server-side request forgery is where the application server is able to interact with different back-end systems that aren’t directly reachable by users. These systems typically have non-routable private informatics addresses. Since the back-end systems normally ordinarily protected by the topology, they typically have a weaker security posture. In several cases, internal back-end systems contain sensitive functionality that may be accessed while not authentication by anyone who is able to act with the systems.
In the preceding example, suppose there’s an body interface at the back-end url https://192.168.0.68/admin. Here, an attacker will exploit the SSRF vulnerability to access the executive interface by submitting the following request:
POST /product/stock HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 118
stockApi=http://192.168.0.68/admin
3. Web server misconfiguration
Server misconfiguration attacks exploit configuration weaknesses found in web and application servers. many servers go with unnecessary default and sample files, including applications, configuration files, scripts, and webpages. they may also have reserve services enabled, like content management and remote administration functionality. Debugging functions could also be enabled or body functions could also be accessible to anonymous users. Servers might embrace well-known default accounts and passwords. Failure to totally lock down or harden the server will leave improperly set file and directory permissions.
All of those server misconfiguration options are often prevent attackers to bypass authentication ways and gain access to sensitive info, maybe with elevated privileges. SSL vulnerabilities like misconfigured certificates and encryption settings, the employment of default certificates, and improper authentication implementation with external systems all have the potential to compromise the confidentiality of information.
How to forestall Server Misconfiguration?
Once you understand your entire environment, the best thanks to manage risk is to lock down the most critical infrastructure, allowing solely desired behaviour. Any communication that isn’t necessary for an application should be blocked. this may include:
- Disable administration interfaces.
- Disable debugging.
- Disable use of default accounts/passwords.
- Configure server to stop unauthorized access, directory listing, etc.
- Consider running scans and doing audits periodically to assist notice future misconfigurations or missing patches.
4. Website defacement
Web defacement is an attack in which malicious parties penetrate a website and replace content on the site with their own messages. The messages will convey a political or religious message, profanity or other inappropriate content that might embarrass website owners, or a notice that the web site has been hacked by a particular hacker profanity.
Most websites and web applications store information in environment or configuration files, that affects the content displayed on the web site, or specifies wherever templates and page content is found. unexpected changes to those files will mean a security compromise and might signal a defacement attack.
Common causes of defacement attacks include:
- Unauthorized access
- SQL injection
- Cross-site scripting (XSS)
- DNS hijacking
- Malware infection
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web-Server Concept
- Web-Server Attacks
- Web-Server Attack Tools
- Web-Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



