iPhone leveling
Understanding the varied sorts of mobile acquisition tools and therefore the data they’re capable of recovering is paramount for a mobile forensic examiner. A mobile device forensic tool arrangement was developed by Sam Brothers, a computer and mobile forensic examiner and researcher. the target of his arrangement is to enable an examiner to put telephone and GPS forensic tools into a category, counting on the extraction methodology of that tool. This categorization facilitates the comparison between different tools and provides a framework for forensic examiners.
The classification tool is displayed in Figure 1.6. Starting at rock bottom and dealing upward, the methods and tools generally become more technical, invasive, time consuming, forensically sound, and expensive (Brothers, 2007). Level 1 (Manual Extraction) involves simply scrolling through the info on the device as any user does during a traditional manner. Level 2 (Logical Analysis) is employed by most investigators today, because it is merely mildly technical and requires little training. Level 3 (Hex Dump) is where many forensic examiners have moved over the last 2–3 years, and it’s been gaining quickly in popularity and support within the forensics community. Level 4 (Chip-Off) is that the “new frontier” for many examiners, as formal training classes teaching this sort of study have barely become available. Finally, Level 5 is never performed and isn’t well documented at this point , because it is extremely technical, very expensive, and highly time consuming.
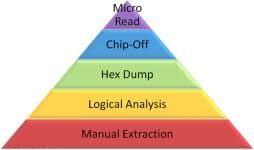
Figure iPhone Classification Tool
It should be noted that there are pros and cons to performing analysis at each layer. The forensics examiner should remember of those issues and will only proceed with the extent of extraction that he/she has been trained to work at. Evidence are often permanently destroyed if a given method or tool isn’t properly utilized. This risk increases the upper you progress up within the pyramid. Thus, proper training is critical to obtaining the very best success rate in data extraction and proper forensic analysis of those devices.
Each existing mobile forensic tool are often classified under one (or more) of the five levels. the subsequent text contains an in depth description of every level also because the methods that are used for data extraction at that given level.
Level 1 – Manual Extraction: A manual extraction involves viewing the info content on the phone directly as viewed on its screen through the utilization of the device’s keypad. the knowledge discovered is manually documented (generally employing a digital camera). At this level, it’s impossible to recover deleted information. Some tools are developed that aid an investigator to simply document a manual extraction. These tools capture what’s shown on the device, which is then captured digitally for future reference and storage.
Level 2 – Logical Extraction: Connectivity to the mobile device is usually established via a cable to either a bit of forensic hardware or a forensic workstation containing specialized software. The examiner can also prefer to use Bluetooth for connectivity rather than a cable. Once connected, the software tool initiates a command to request then extract allocated files on a given device. As explained by Brothers, the command is initiated by the pc and sent to the device, which is then interpreted by the processor within the device. Next, the requested data is retrieved from the device’s memory and sent back to the forensic workstation to be reviewed by the examiner. Most iPhone forensic tools currently available perform at this level of the arrangement . It should even be noted that several of those tools are capable of performing an analysis of iPhone backup files saved on a user’s computer.
Also Read: What is Email Forensic Investigation
Level 3 – Hex Dump: A hex dump, more commonly mentioned as a “physical extraction,” provides the investigator with more data than was available at the lower levels. To perform this sort of extraction, the device is connected to the forensic workstation generally via a cable. Occasionally, this connection to the pc is either through the device’s data port, JTAG (an internal test connection), or maybe via Wi-Fi. rather than initiating a command, unsigned code is copied to the device (most commonly into memory), instructing the phone to repeat user data to the pc . The resulting data is copied, transferred, and stored as a raw disk image. Since the resulting image is in binary format, technical expertise is required for analysis at this level. The currently available tools which will perform this sort of acquisition on an iPhone are discussed intimately in some books.
Level 4 – Chip-Off: Chip-off refers to the acquisition of knowledge directly from the device’s chip , which within the case of the iPhone is that the NAND non-volatile storage . The chip is physically faraway from the device and data stored thereon is extracted by a chip reader. Brothers points out that this sort of acquisition is analogous to imaging a tough drive from a computer or laptop using traditional hard disc imaging techniques. because the pyramid describes, this method is far more technically challenging than the manual, logical, or hex dumping acquisition techniques. the quantity of required investigator knowledge greatly increases at this level as does the acquisition time. a number of the aspects that make this system so advanced include the big variety of chip types used, the myriad of raw binary data formats, and therefore the risk of causing physical damage to the chip during the extraction process .
Level 5 – Micro Read: This process involves manually viewing and interpreting data seen on the chip . By analyzing the physical gates on the chip, the examiner can then translate the gate status to 0’s and 1’s to then determine the resulting ASCII characters. the method is time consuming and dear , and requires extensive knowledge of all aspects of Flash memory and the file system. There are currently no commercial tools available to perform a micro read on an Apple device.



