Overview of Network Security Objectives this blog is based on Understanding Network and Information Security with it’s objective Confidentiality, Integrity and Availability etc.
Understanding Network and information Security Basics
Security is very important, and therefore the lack of it risks financial, legal, political, and PR implications. This section covers a number of the concepts, terms, and methodologies employed in preparing for and dealing with secure networks.
Network Security Objectives
When considering networks, you’ll view them from different perspectives. for instance , senior management might view the network as a business tool to facilitate the goals of the corporate . Network technicians (at least some) might consider their networks to be the middle of the universe. End users might consider the network to be just a tool for them to urge their job done, or possibly as a source for recreation. Not all users appreciate their role keep data safe, and unfortunately the users of the network represent a big vulnerability, therein they need usernames and passwords (or other credentials, like one-time password token generators) that allow them access to the network. If a user is compromised or an unauthorized individual gains access to data, applications, or devices that they ought to not have access, the safety of the network should fail as a result, even after you apply all the concepts that you simply learn during this book. So, a crucial point to recollect is that the users’ behaviours pose a security risk which training users may be a key a part of a comprehensive security policy.
Confidentiality, Integrity, and Availability
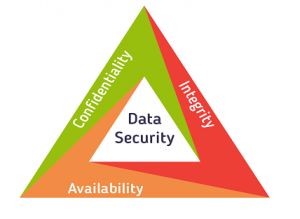
Network security objectives usually involve three basic concepts:
- Confidentiality: There are two sorts of data: data in motion because it moves across the network; and data at rest, when data is sitting on storage media (server, local workstation, within the cloud, then forth). Confidentiality means only the authorized individuals/systems can view sensitive or classified information. This also implies that unauthorized individuals mustn’t have any sort of access to the info . Regarding data in motion, the first thanks to protect that data is to encrypt it before sending it over the network. an alternative choice you’ll use with encryption is to use separate networks for the transmission of confidential data. Several chapters during this book specialise in these two concepts.
- Integrity: Integrity for data means changes made to data are done only by authorized individuals/systems. Corruption of knowledge may be a failure to take care of data integrity.
- Availability: this is applicable to systems and to data. If the network or its data isn’t available to authorized users—perhaps due to a denial-of-service (DoS) attack or even due to a general network failure—the impact could also be significant to companies and users who believe that network as a business tool. The failure of a system, to incorporate data, applications, devices, and networks, generally equates to loss of revenue. Perhaps thinking of those security concepts because the CIA “triad” might assist you remember them: confidentiality, integrity, and availability.
Cost-Benefit Analysis of Security
Network security engineers must understand not only what they protect, but also from whom. Risk management is that the key phrase that you simply will hear over and over, and although not very glamorous, it’s supported specific principles and ideas associated with both asset protection and security management.
What is an asset?
It’s anything that’s valuable to a corporation . These might be tangible items (people, computers, then on) or intangible items (intellectual property, database information, contact lists, accounting info). Knowing the assets that you simply try to guard and their value, location, and exposure can assist you more effectively determine the time and money to spend securing those assets.
A vulnerability is an exploitable weakness during a system or its design. Vulnerabilities are often found in protocols, operating systems, applications, and system designs. Vulnerabilities abound, with more discovered a day .
A threat is any potential danger to an asset. If a vulnerability exists but has not yet been exploited or, more importantly, it’s not yet publicly known, the threat is latent and not yet realized. If someone is actively launching an attack against your system and successfully accesses something or compromises your security against an asset, the threat is realized. The entity that takes advantage of the vulnerability is understood because the malicious actor and therefore the path employed by this actor to perform the attack is understood because the threat agent or threat vector.
“A threat is any potential danger to an asset”
A countermeasure may be a safeguard that somehow mitigates a possible risk. It does so by either reducing or eliminating the vulnerability, or a minimum of reduces the likelihood of the threat agent to truly exploit the danger . for instance , you would possibly have an unpatched machine on your network, making it highly vulnerable. If that machine is unplugged from the network and ceases to possess any interaction with exchanging data with the other device, you’ve got successfully mitigated all of these vulnerabilities. you’ve got likely rendered that machine not an asset, though; but it’s safer.
Note that thresholds apply to how we classify things. We don’t spend quite the asset is worth to guard it because doing so makes no sense. for instance , purchasing a second hand car for $200 then spending $2000 on a secure garage facility in order that nobody can harm the car or $1500 on an alarm for that car seems to be a reasonably silly proposition. If you identify the info with the best value/worth, you always automatically identify where the best effort to secure that information are going to be confine mind, however, that beyond a company’s particular view about the worth of any data, regulatory entities may additionally be involved (government regulations or laws, business partner agreements, contractual agreements, then forth).
Also Read : Network Security Controls
Just accepting the complete risk (the all-or-nothing approach) isn’t really acceptable. After all, you’ll implement security measures to mitigate the danger . additionally , those self same security devices, like firewalls and intrusion prevention systems (IPS), can protect multiple devices simultaneously, thus providing a price benefit. So, you’ll reduce risk by pocket money on appropriate security measures, and typically do an honest job of protecting an asset. you’ll never completely eliminate risk, so you want to find the balance.
Content describes variety of security terms and therefore the appliances to which they relate.
Asset
An asset is an item that’s to be protected and may include property, people, and information/data that have value to the corporate . This includes intangible items like proprietary information or trade secrets and therefore the reputation of the corporate . the info could include company records, client information, proprietary software, and so on.
Vulnerability
A vulnerability is an exploitable weakness of some type. That exploitation might result from a malicious attack, or it’d be accidentally triggered due to a failure or weakness within the policy, implementation, or software running on the network.
Threat
This is what you’re protecting against. A threat is anything that attempts to realize unauthorized access to, compromise, destroy, or damage an asset. Threats are often realized via an attack or exploit that takes advantage of an existing vulnerability. Threats today are available many sorts and spread sooner than ever before. Threats also can morph and be modified over time, then you want to be ever diligent to stay up with them.
Risk
Risk is that the potential for unauthorized access to, compromise, destruction, or damage to an asset. If a threat exists, but proper countermeasures and protections are in situ (it is your goal to supply this protection), the potential for the threat to achieve success is reduced (thus reducing the general risk).
Countermeasure
Risk is that the potential for unauthorized access to, compromise, destruction, or damage to an asset. If a threat exists, but proper countermeasures and protections are in situ (it is your goal to supply this protection), the potential for the threat to achieve success is reduced (thus reducing the general risk).
Questions related to this topic
- What are the 3 threats to information security?
- What is information security risk?
- What are some examples of unauthorized access?
- What is confidentiality in computer security?
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



