CEH Training Noida | CEH-v10 Training Course
Original price was: ₹35,000.00.₹32,000.00Current price is: ₹32,000.00.
Infosavvy raises the bar again for certification and training of ethical hacking programs with the all new C|EH v10! This program will make you involve deeply into Hacker Mindset which will teach you how to think like a hacker, it puts you in a position where you have all the commands and knowledge in employing the ethical hacking process.
Certified Ethical Hacker | CEH Certification
- Introduction to Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration
- Vulnerability Analysis
- System Hacking
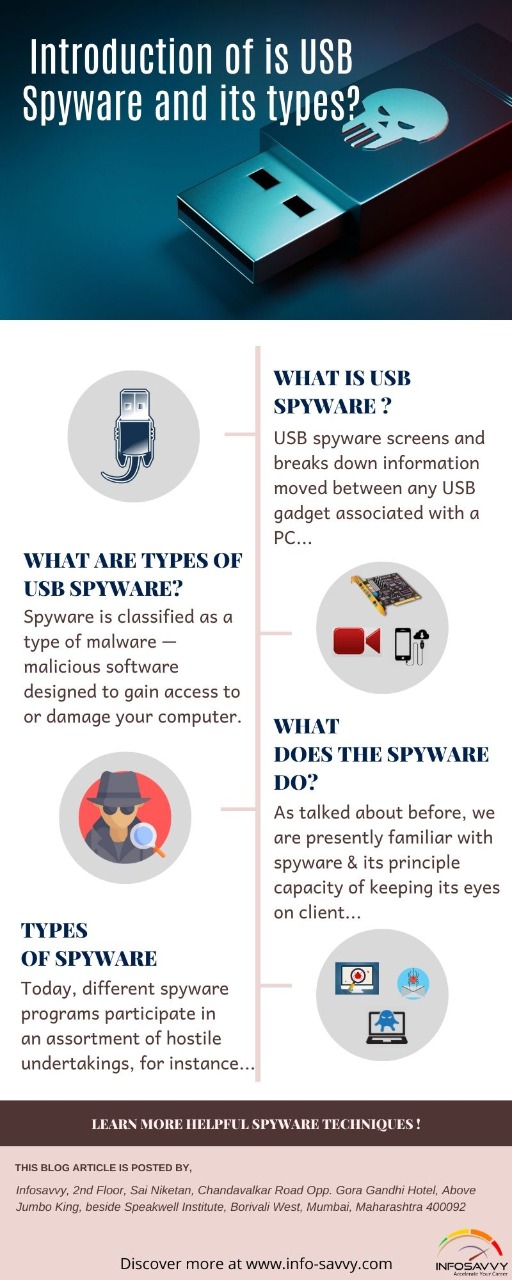
- Malware Threats
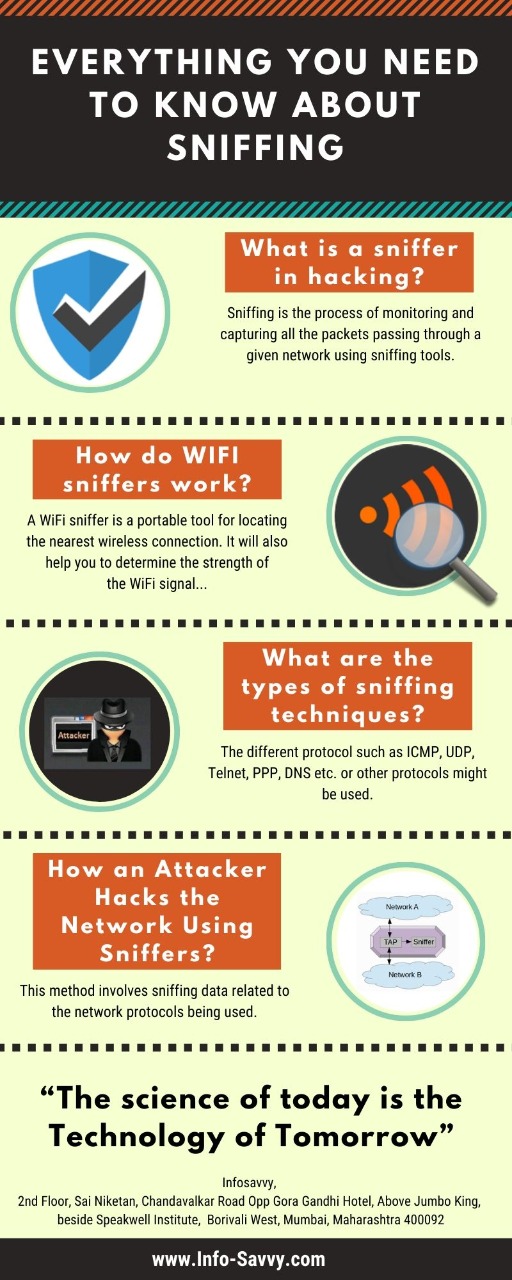
- Sniffing
- Social Engineering
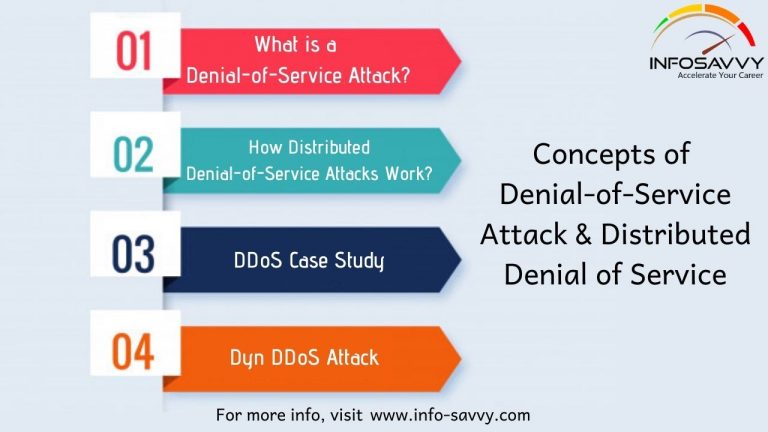
- Denial of Service
- Session Hijacking
- Hacking Web Servers
- Hacking Web Applications
- SQL Injection
- Hacking Wireless Networks
- Hacking Mobile Platforms
- Evading IDS, Firewalls, and Honeypots
- I0T Hacking
- Cloud Computing
- Cryptography
- Security Officers
- Auditors
- Network Administrators
- Firewall Administrators
- Security Professionals
- Anyone who is concerned about the integrity of the network infrastructure
- Network Administrator
- Systems Administrator
- Systems Engineer
- Systems Architect
- Network Security Specialist
Prerequisites
- Strong knowledge of TCP/IP
- Information systems and security background
- Minimum of 12 months of experience in networking technologies
CEH v10 Exam Info
- Number of Questions: 125
- Passing Score: 70%
- Test Duration: 4 Hours
- Test Format: Multiple Choice
- Test Delivery: Prometric Prime / VUE / ECCEXAM
Legal Agreement
Ethical Hacking and Countermeasures course mission is to educate, introduce and demonstrate hacking tools for penetration testing purposes only. Prior to attending this course, you will be asked to sign an agreement stating that you will not use the newly acquired skills for illegal or malicious attacks and you will not use such tools in an attempt to compromise any computer system, and to indemnify EC-Council with respect to the use or misuse of these tools, regardless of intent. Not anyone can be a student – the Accredited Training Centers (ATC) will make sure the applicants work for legitimate companies.
Certified Ethical Hacker | CEH
INFOSAVVY’s Certified Ethical Hacker | CEH training and certification boot camp will immerse the students into a hands-on environment where they will be shown how to conduct ethical hacking.
Certified Ethical Hacker | CEH is the worlds most advanced ethical hacking course with 18 of the most current security domains any ethical hacker will ever want to know when they are planning to beef up the information security posture of their organization. In 18 comprehensive modules, the course covers over 270 attack technologies, commonly used by hackers. The CEH v10 contains over 140 labs which mimic real time scenarios in the course to help you “live” through an attack as if it were real and provide you with access to over 2200 commonly used hacking tools to immerse you into the hacker world. As “a picture tells a thousand words”, the developers of the CEH v9 have all this and more for you in over 2200 graphically rich, specially designed slides to help you grasp complex security concepts in depth which will be presented to you in 5 day hands on class by our Certified Instructor. The goal of this course is to help you master an ethical hacking methodology that can be used in a penetration testing or ethical hacking situation. You walk out the door with ethical hacking skills that are highly in demand, as well as the globally recognized Certified Ethical Hacker certification! This course prepares you for EC-Council Certified Ethical Hacker exam 312-50. In short, you walk out the door with hacking skills that are highly in demand, as well as the internationally recognized Certified Ethical Hacker certification!
INFOSAVVY’s Certified Ethical Hacker | CEH training and certification boot camp will immerse the students into a hands-on environment where they will be shown how to conduct ethical hacking. They will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! They will scan, test, hack and secure their own systems. This course was designed to provide you with the tools and techniques used by crackers and information security professionals alike to break into an organization. As we put it, “To beat a cracker, you need to think like a cracker”. You will be thought the Five Phases of CEH and thought how you can approach your target and succeed at breaking in every time! The five phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks. This course will immerse you into the cracker Mindset so that you will be able to defend against future attacks. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. All of this will be done without harming any real network. Students will also learn about Intrusion Detection, Policy Creation, Social Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student leaves this intensive 5 day class they will have hands on understanding and experience in Ethical Hacking. This course prepares you for EC-Council Certified Ethical Hacker v9 exam 312-50.
Other IT Security and Governance Courses
You must be logged in to post a review.
You may also like…
-
IT Security & Governance
EC-Council Certified Chief Information Security Officer | CCISO
₹70,000.00 Add to cartCCISO Certification is an up skill to be succeeded at the highest levels of information security. It’s first of its kind training certification program aimed at producing top-level information security executives. It not only concentrates on technical knowledge but also on the application security management principles from an executive management point of view.
The program consists of three committees: Training, Body of Knowledge and the C|CISO Exam. Every element of this program was developed with the aspiring CISO keeping in minds and looks to spread the knowledge of seasoned professionals to the next generation in the arena that are most critical in the growth sector and maintenance of a successful information security program.
[ninja_form id=7] -
IT Security & Governance
EC-Council Certified Incident Handler | ECIH v2
Original price was: ₹23,000.00.₹21,000.00Current price is: ₹21,000.00. Add to cartECIH is a program which enables individuals and organizations with the ability to handle and respond to various types of cyber security incidents in a systematic way (I, H and R). Restoring regular operations of the organizations at the earliest and mitigating the negative impact on the business operations.
The I, H and R process includes stages like incident handling and response preparation, incident validation and prioritization, incident escalation and notification, forensic evidence gathering and analysis, incident containment, systems recovery, and incident eradication.
[ninja_form id=7] -
IT Security & Governance
EC-Council Security Analyst v10 | ECSA
Original price was: ₹45,000.00.₹40,000.00Current price is: ₹40,000.00. Add to cartECSA training from Infosavvy provides an absolute learning progress continuing where the CEH program left off. This new ECSAv10 program has updated syllabus and an industry recognized comprehensive penetration testing methodology.
Inclusive of all the above mentioned topics certifies the learner to elevate their abilities by applying these skills learned through intensive practical labs and challenges.
Various methods are covered by ECSA in this course which has different requirements across all the verticals. ECSA is an amalgamation of both manual and automated penetration testing.
[ninja_form id=7]
-
IT Security & Governance
Certified Threat Intelligence Analyst | CTIA
Original price was: ₹25,000.00.₹20,000.00Current price is: ₹20,000.00. Add to cartCertified Threat Intelligence Analyst | CTIA by ISACA is a training and credentialing program from Infosavvy which is designed and developed in collaboration with cyber security and threat intelligence experts across the globe. It helps organizations in identifying and mitigating business risks by converting unknown threats mainly internal and external into known threats. It is a comprehensive specialist level program that teaches a structured approach for building effective threat intelligence.
Mainly our Target Audience are Ethical Hackers, Security Practitioners, Engineers, Analysts, Specialist, Architects, Managers, Threat Intelligence Analysts, Associates, Researchers, Consultants, Threat Hunters and SOC Professionals.
[ninja_form id=7]















Reviews
There are no reviews yet.