Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to perform port scanning on a target host in the network. While performing the given task, Sam sends FIN/ACK probes and determines that an RST packet is sent in response by the target host, indicating that the port is closed. What is the port scanning technique used by Sam to discovers open ports?
Option 1 : IDLE/IPID header scan
Option 2 : ACK flag probe scan
Option 3 : Xmas scan
Option 4: TCP Maimon scan
1. IDLE/IPID header scan
Idle scan may be a TCP based port scan where the attacker sends spoofed packets to a passive (also called as “silent”) victim host. With the term “passive” we mean here that the incoming or outgoing traffic of the victim host is extremely low. (The reason of this may be understood throughout the article.)
Before we enter the deeper details of the Idle Scan, two concepts need to be understood clearly:
1) IP ID
2) Response of a number to some TCP flags.
Idle Scan (Victim Port Open)
1.) The attacker sends a SYN/ACK segment to the Zombie computer.
2.) Zombie computer responses with RST segment and its IP ID is incremented by “one”.
With this step the attacker learns the IP ID value of the Zombie computer which is 6,162 during this case.
3.) After the attacker has learnt the IP ID value of the Zombie computer the attacker sends a SYN segment to the victim computer with the spoofed IP address of the Zombie computer. (Spoofed IP address is 192.168.20.20 during this case.)
4.) Because the port on the victim computer is open then victim computer will response to the Zombie computer with a SYN/ACK Notice that the response isn’t sent to the attacker rather to the Zombie Computer because the attacker has spoofed the IP address of the Zombie computer.
Also be conscious of that in this point period we assume that there wasn’t any traffic coming into our Zombie computer.
5.) The Zombie computer gets a SYN/ACK segment from the victim computer and therefore the refore the Zombie computer responds with RST segment thereto and the Zombie computer increases its IP ID by “one” (IP ID = 6,163)
6.) The attacker sends a SYN/ACK segment to the Zombie computer.
The Zombie computer responds with a RST segment to the SYN/ACK segment and increases its IP ID by “one”. IP ID value are going to be 6,164.
The first IP ID value of the Zombie computer sent to the attacker was 6,162. At the top of this process, the attacker gets an IP ID value of 6,164. Because the IP ID is increased by “two” we will conclude that the port of the victim computer is OPEN. As you’ll see we will learn the status of the ports of the victim computer via a Zombie computer with sending just a SYN segment to the victim computer. (Kinda magic, huh?)
Let me remind you the thing again: If during this point our Zombie computer sent or received any traffic from the other host then the IP ID would be increased by quite “two”. therefore the Idle Scan wouldn’t work for that case. That’s why it’s vital that our chosen Zombie computer has got to be “idle” within the network.
2. ACK flag probe scan
ACK flag probe scanning works by sending TCP probe packets with ACK flag set so as to work out whether the port is open or closed. this is often done by analyzing the TTL and WINDOW field of the received RST packet’s header. The port is open if the TTL value is a smaller amount than 64.
Similarly, the port is additionally considered to be open if the WINDOW value isn’t 0 (zero). Otherwise, the port is taken into account to be closed.
ACK flag probe is additionally wont to determine the filtering rules of the target network. If there’s no response, then meaning that a stateful firewall is present. If the response is RST, then the port isn’t filtered.
3. Xmas scan
In this scan, the ACK, SYN, URG, RST, and FIN flags are ready directly on an equivalent packet. the difficulty with this is often that since all the flags are set, the target system may have difficulties in interpreting the packets it’s received. the subsequent diagram shows this process:


4. TCP Maimon scan
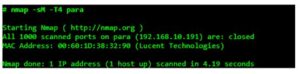
The Maimon scan is known as after its discoverer, Uriel Maimon. He described the technique in Phrack Magazine issue #49 (November 1996). Nmap, including this system , was released two issues later. this system is strictly an equivalent as NULL, FIN, and Xmas scan, except that the probe is FIN/ACK. consistent with RFC 793 (TCP), a RST packet should be generated in response to such a search whether the port is open or closed. However, Uriel noticed that a lot of BSD-derived systems simply drop the packet if the port is open. Nmap takes advantage of this to work out open ports, as shown in

The Nmap flag for a Maimon scan is -sM. While this feature was quite useful in 1996, modern systems rarely exhibit this bug. They send a RST back for all ports, making every port appear closed.
Example failed Maimon scan
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



