Steven connected his iPhone to a public computer that had been infected by Clark, an attacker. After establishing the connection with the public computer, Steven enabled iTunes WI-FI sync on the computer so that the device could continue communication with that computer even after being physically disconnected. Now, Clark gains access to Steven’s iPhone through the infected computer and is able to monitor and read all of Steven’s activity on the iPhone, even after the device is out of the communication zone.
Which of the following attacks is performed by Clark in above scenario?
Option 1 : iOS Jailbreaking
Option 2 : Exploiting SS7 vulnerability
Option 3 : iOS trustjacking
Option 4 : Man-in-the-disk attack
1. iOS Jailbreaking
Jailbreaking alludes to advantage heightening on an iPhone gadget to eliminate programming limitations forced by iPhone on iOS, iPhone, tvOS, watchOS, bridgeOS and audioOS working frameworks. Normally it is done through a progression of part fixes. A jailbroken gadget licenses root access inside the working framework and gives the chance to introduce programming not accessible through the iOS iPhone Store. Various gadgets and variants are abused with an assortment of devices. Apple sees jailbreaking as an infringement of the End-client permit arrangement, and emphatically alerts gadget proprietors from endeavoring to accomplish root access through abuse of weaknesses.
While now and again contrasted with establishing an Android gadget, Jailbreaking is the detour of a few kinds of iPhone preclusions for the end client. Since it incorporates altering the working framework (implemented by a “bolted bootloader”), introducing non-formally endorsed (not accessible on the iPhone App Store) applications by means of sideloading, and giving the client raised organization level advantages (establishing), the ideas are extraordinary.
2. Exploiting SS7 weakness
SS7 assaults are versatile digital assaults that abuse security weaknesses in the SS7 convention to bargain and catch voice and SMS interchanges on a cell organization. Like a Man In the Middle assault, SS7 assaults target cell phone interchanges as opposed to wifi transmissions.
How do SS7 assaults work?
SS7 assaults abuse the validation capacity of correspondence conventions running on the SS7 convention to snoop on voice and text interchanges. As indicated by media communications specialists, all a digital criminal would require to effectively dispatch a SS7 assault are a PC running Linux and the SS7 SDK – both allowed to download from the Internet.
When associated with a SS7 organization, the programmer can target supporters on the organization while tricking the organization into speculation the programmer gadget is really a MSC/VLR hub.
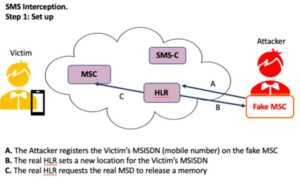
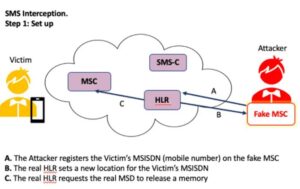
How can portable administrators deal with forestall SS7 assaults?
The imperfections and weaknesses inborn in the SS7 convention are out of the ward of endeavors, independent ventures just as customers. Being that, SS7 weaknesses can’t just be eliminated or fixed.
The GSMA suggests that versatile organization tasks center around customer training. With customers giving more consideration to the security of their cell phones and IoT gadgets they are bound to make a move to make sure about their gadgets. Particularly with regards to basic applications and administrations like Smart Homes and Offices.
- Client Password Security
Two factor SMS confirmation, imperfect all things considered, is still generally utilized. Security cognizant organizations and administrations are slowly moving ceaselessly from SMS and offer different strategies for validating clients which don’t depend on outdated phone conventions like SS7.
- Observing and Event Analysis
In the event that a SS7 network is effectively undermined, organizations need to be able to screen the movement during the assault. They should be educated on security occasions with regards to what’s going on corporate workers just as gadgets. This should be important for any undertaking portable security procedure. At last, organizations need to execute a protection that recognizes dangers and makes a move before any harm happens.
- Ordinary Updates
Network safety is certainly not a set it and fail to remember it bargain regardless of whether you utilize mechanization. Cybercriminals are continually concocting new endeavors and ways to deal with bargain frameworks to get their hands on classified information or seize gadgets for recover. Successful Patch Management is basic and supplements versatile guard. By utilizing constant investigation of endpoint security, business can guarantee referred to weaknesses are fixed at the earliest opportunity through programming and firmware refreshes.
How would you be able to respond?
The best way to be completely protected from SS7 assaults is to just stop your cell phone. You and I both realize that is impossible. So what you can do is “know the adversary”. Staying alert that pernicious exercises like SS7 assaults are predominant and normal is essentially a need in 2020.
All things considered, with the billions of cell phone clients around the world, the danger of you being focused for reconnaissance by digital crooks is likely little. However, in the event that you end up being a president, sovereign or even specialist holding delicate patient data on their versatile, your odds are a lot higher than those of a regular person. In case you’re actually utilizing 2FA for banking administrations, you might just be at risk for having your record bargained.
Considering exactly that it is so natural to execute a SS7 assault and how much harm a fruitful one can do to both the person in question and their specialist organization, one can dare to dream that development in telecom will ensure us, the end clients.
3. iOS trustjacking
An iPhone client’s most noticeably terrible bad dream is to have somebody oversee his/her gadget, including the capacity to record and control all action without waiting be in a similar room. In this blog entry, we present another weakness called “Trustjacking”, which permits an aggressor to do precisely that.
This weakness misuses an iOS highlight called iTunes Wi-Fi sync, which permits a client to deal with their iOS gadget without genuinely interfacing it to their PC. A solitary tap by the iOS gadget proprietor when the two are associated with a similar organization permits an assailant to oversee the gadget. Furthermore, we will stroll through past related weaknesses and show the progressions that iPhone has made to alleviate them, and why these are adequately not to forestall comparative assaults.
After interfacing an iOS gadget to another PC, the clients are being found out if they trust the associated PC or not. Deciding to believe the PC permits it to speak with the iOS gadget by means of the standard iTunes APIs.
This permits the PC to get to the photographs on the gadget, perform reinforcement, introduce applications and considerably more, without requiring another affirmation from the client and with no recognizable sign. Besides, this permits enacting the “iTunes Wi-Fi sync” highlight, which makes it conceivable to proceed with this sort of correspondence with the gadget even after it has been detached from the PC, as long as the PC and the iOS gadget are associated with a similar organization. It is intriguing to take note of that empowering “iTunes Wi-Fi sync” doesn’t need the casualty’s endorsement and can be directed simply from the PC side.
Getting a live stream of the gadget’s screen should be possible effectively by consistently requesting screen captures and showing or recording them distantly.
It is imperative to take note of that other than the underlying single purpose of disappointment, approving the vindictive PC, there is no other component that forestalls this proceeded with access. Likewise, there isn’t anything that informs the clients that by approving the PC they permit admittance to their gadget even in the wake of detaching the USB link.
4. Man-in-the-plate assault
Man-in-the-plate (MITD) is an assault vector that permits a gatecrasher to block and possibly change information as it moves between Android outside capacity and an introduced versatile application. MITD is a variety of the more ordinarily known man-in-the-center assault. The assault abuses inadequately composed code that neglects to follow Google’s proposals for how applications should utilize outer capacity.
In any gadget that utilizes the Android OS, there are two sorts of capacity: inner and outside. Inward capacity for Android applications is sandboxed with the application, however outer capacity is proposed to permit record dividing among applications. Android engineers are urged to program applications so all information is securely put away inside the Android gadget’s interior stockpiling, however when a program is made that stores all or part of its information in the outer piece of the Android’s stockpiling framework, the information turns into an assault surface on the grounds that the information is helpless against control by outside gatherings.
Normally, outer capacity is situated on a SD card or inside a capacity segment on the Android gadget and is utilized to divide records among applications. During a MITD assault, when a real program endeavors to run a normal update, the aggressor can supplant the update records with an altogether new program or control the application by altering the update’s code. When vindictive applications are introduced or changes are made with code infusion, an outsider can sidestep the framework’s security and access delicate data, similar to contact records and photographs, or equipment, similar to receivers and cameras. This sort of assault can likewise make the program show a mistake and immediately shut down, it can mess with different applications, or it can run malevolent code that harms the gadget or totally takes it over through an advantage heightening assault.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



