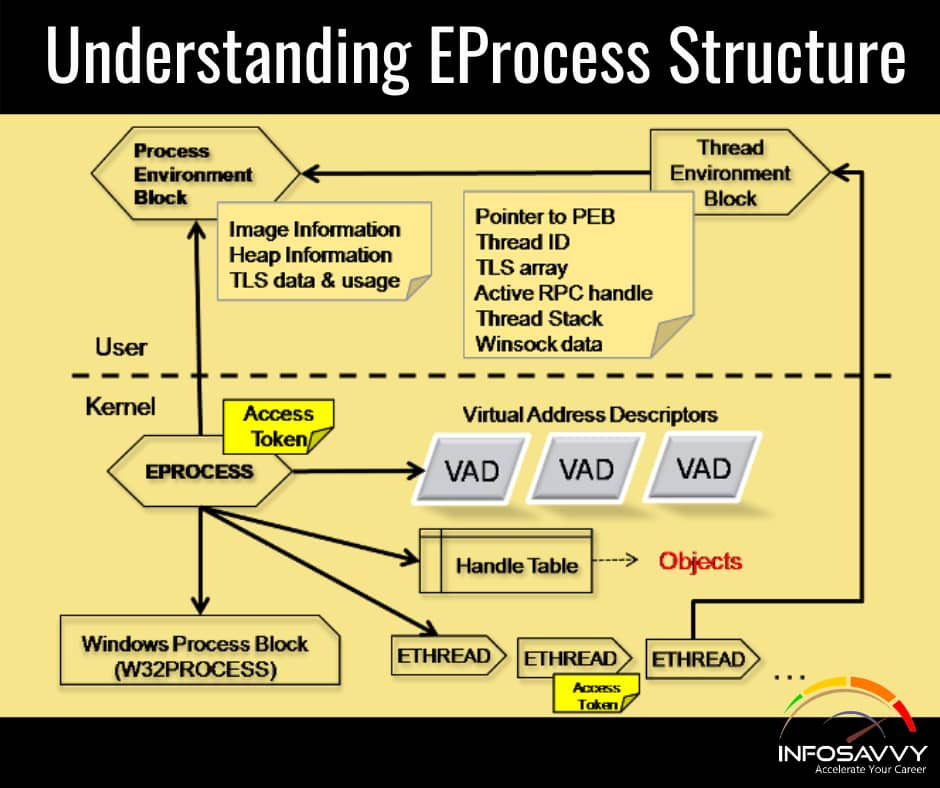
Understand the Importance of Network Forensics
Understand the Importance of Network Forensics in this this article Network Forensics is the implementation of sniffing, recording, acquisition, and analysis of network traffic and event logs to investigate a network security incident. Capturing network traffic over a network is simple in theory, but relatively complex in practice due to many inherent reasons such as the large amount of data flow and complex nature of Internet protocols. Recording network traffic involves a lot of resources. …