Learn All About Linux File Systems
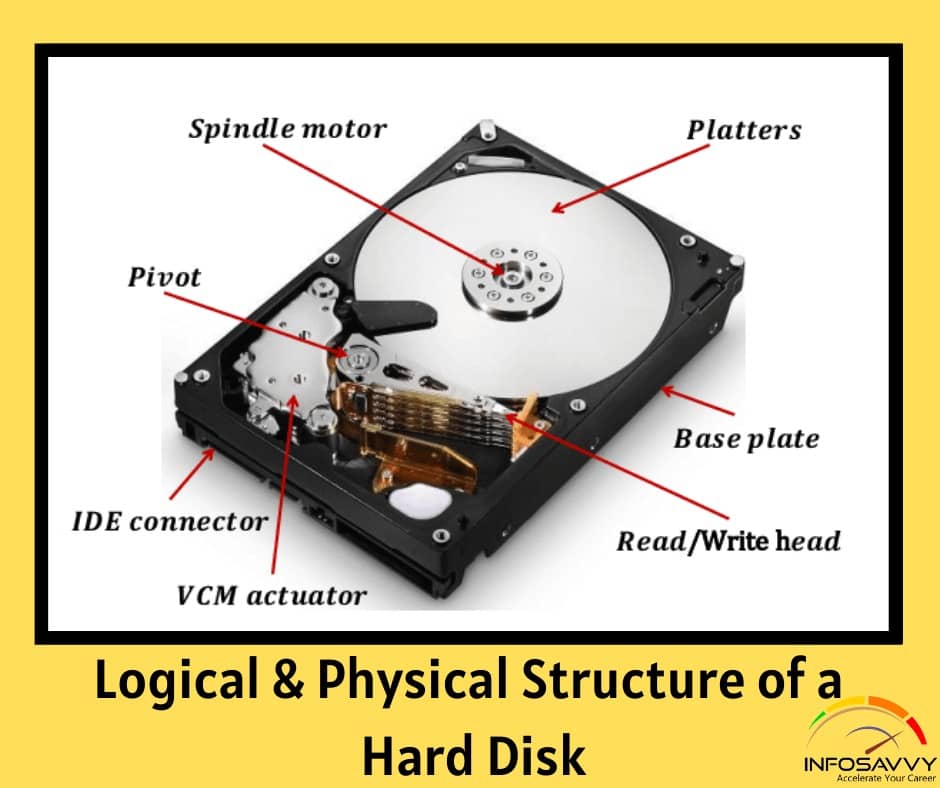
In this blog explain Linux File System Architecture, File system Hierarchy atandard (FHS), Extended File System (EXT), Second Extended File System (EXT2), Second Extended File System (EXT2) (Cont’d), Second Extended File System (EXT2) (Cont’d) etc… Linux OS uses different file systems to store the data. As the investigators may encounter the attack source or victim systems to be running on Linux, they should have comprehensive knowledge regarding the storage methods it employs. The following section …