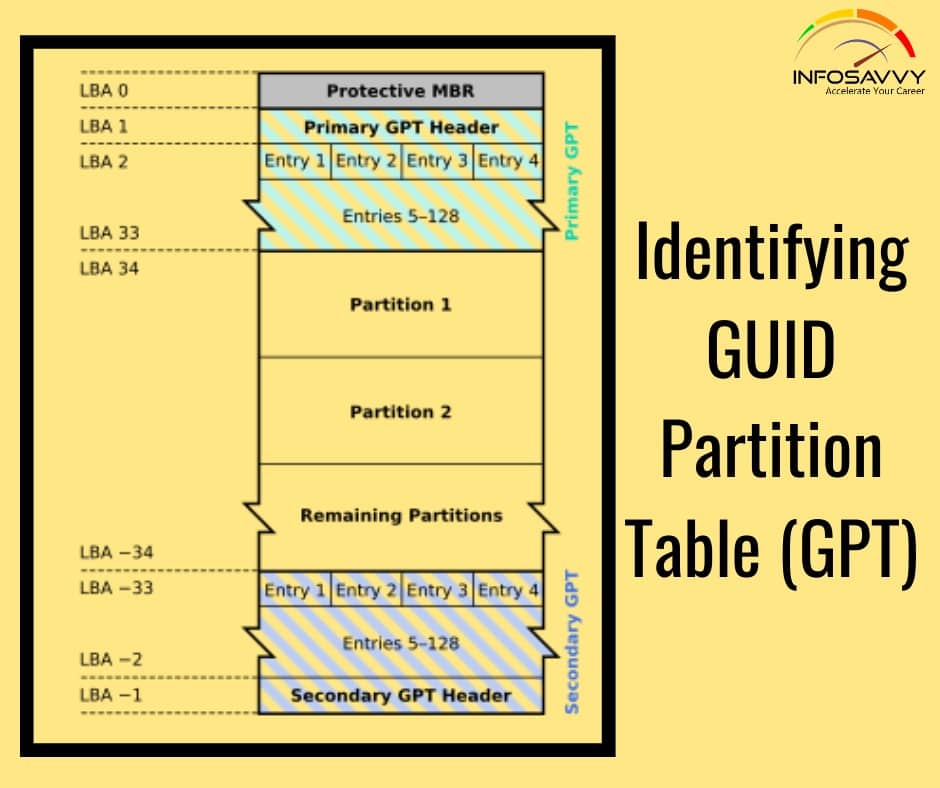
Detecting Steganography
Detecting Steganography in this article how to detect Steganography explained with it types as well as Steganography detecting files explained with the help of tools using in stegenography and data hiding in file system structures technique. Software Clues on the Computer During investigation, the investigators should first look at files, documents, software applications, and other suspicious files for clues hidden through steganography. Steganography investigators should also know about common steganographic techniques, software, tools, terminologies, and …