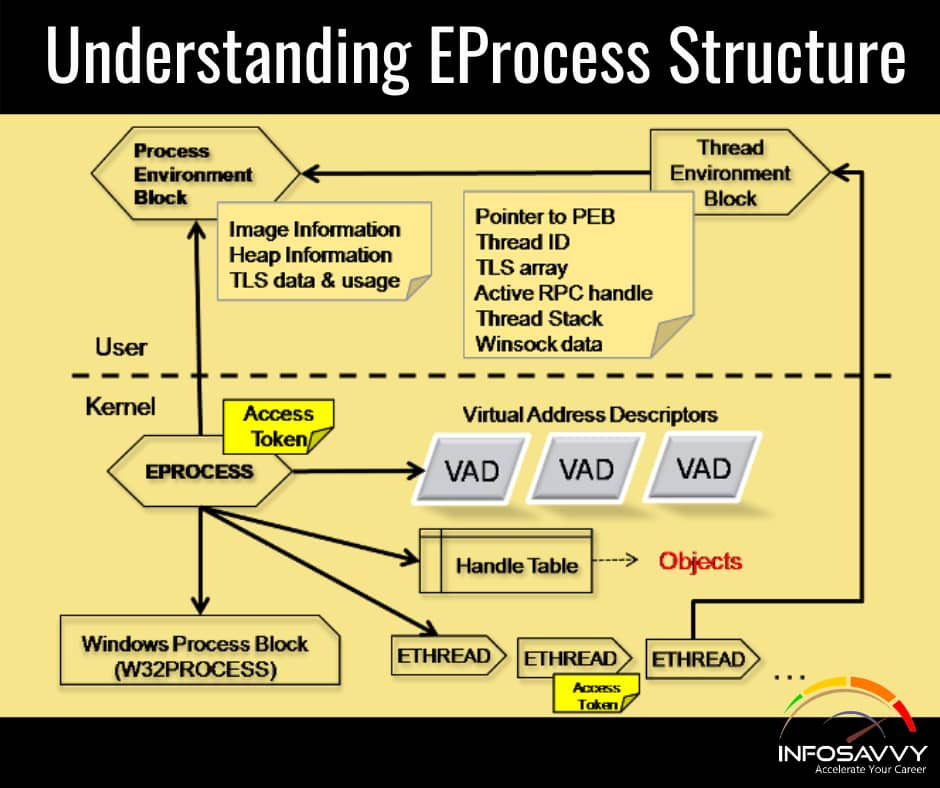
Understanding EProcess Structure in Each process on the Windows operating system is associated with an executive process or Eprocess block. It is the basic data structure that stores various attributes of the process and the pointer to the other attributes and data structures related to the process. The investigator can read this data structure. The data structure is essentially a sequence of bytes, with each sequence having a particular meaning. The size and even the values of the structures change not only between operating system versions but also between service packs of the same version of the operating system.
It is relatively easy to view the contents of the EProcess structure. First, download and install the Microsoft debugging tools and the correct symbols for operating system and service pack. Then download LiveKD.exe, copy it into the same directory as the debugging took. Once this is done, open a command prompt, change to the directory where the debugging tool is installed, and type the following command: debug>livekd -w
This command will open WinDbg, the GU1 interface to the debugger tools. To see the entire contents of an EProcess block, type dt -a -b —v _EPROCESS into the command window, and press Enter. The —a flag shows each array element on a new line, with its index. The —b switch displays blocks recursively. The -v flag creates a more verbose output, telling the overall size of each structure.
The process environment block, or PEB is an important element of all processes which is pointed to by the EProcess structure. This structure contains a great deal of information, but the elements that are important to forensic investigators are:
- A pointer to the loader data (referred to as PPEB_LDR_DATA) structure that includes pointers or references to modifies (DLLs) used by the process.
- A pointer to the image base address where an investigator expects to find the beginning of the executable image file
- A pointer to the process parameter structure, which itself maintains the DLL path, the path to the executable image, and the command line used to launch the process Parsing this information from a dump file can be useful to the investigator.
Related Product : Computer Hacking Forensic Investigator | CHFI
Process Creation Mechanism
There are a number of steps that are followed when a process Ls created, These steps can be broken down into six stages:
- The image (.exe) file to be executed is opened. During this stage, the appropriate subsystem (Posix, MS-DOS, Win 16, etc.) is identified, the Image File Execution Options registry key is checked to see if there is a debugger value, and if there is, the process starts over.
- The EProcess object is created. The kernel process block (KProcess), the process environment block, and the initial address space are also set up.
- The initial thread is created.
- The Windows subsystem is notified of the creation of the new process and thread, along with the ID of the process’ creator and a flag to identify whether the process belongs to a Windows process.
- Execution of the initial thread starts. At this point, the process environment has been set up and resources have been allocated for the process’s thread(s) to use.
- The initialization of the address space is completed in the context of the new process and thread.
The process has at least one thread and may begin consuming additional memory resources as the process executes itself.
Parsing Memory Contents
The tools that parse memory contents usually employ the methodology of locating and enumerating the active process list using specific values/offsets (derived from system files) to identify the beginning of the list. Then the tools use the same methodology for walking through the double linked list, until all the active processes have been identified. The location of the offset for the beginning of the active process list was derived from one of the important system files, ntoskrnl.exe. Lsproc.pl Lsproc (short for list processes) locates processes but not threads. It takes single argument, the path, and name, to a RAM dump file:
Example: c: \perl \memory>lsproc pl d: \dumps \ drfws1-mem.dmp
The output of Isproc.pl appears at the console (i.e., STDOUT) in six columns. Lspd.pl
Ispd.pl is a command-line Perl script that relies on the output of Isproc.pl to obtain its information, Specifically, Ispd.pl takes two arguments: the path and name of the dump file and the offset from the lsproc.pl output of the process that the investigators are interested in.
The command line to use Ispd.pl is: c:\perl\memory>lspd.pl d:\dumps\dfrwsl-mem.dmp 0x0414dd60
Lspd.pl also retrieves a list of the names of various modules (DLLs) used by the process and whatever available handles (file handles and so on) it can find in memory.
Also Read : What is Memory Dump?
Parsing Process Memory
In the past, investigators have used tools such as strings.exe or grep searches to parse through the contents of a RAM dump and look for interesting strings (passwords), IP or email addresses, URLs, etc. However, when investigators are parsing through a file which is about half a megabyte in size, there is not a great deal of context to the information.
Lspm.pI takes the same arguments as Ispd.pl (the name and path of the dump file, and the physical offset within the file of the process structure) and extracts the available pages from the dump file, and writes them to a file within the current working directory. To run lspm.pl against the dd.exe process, use the following command line:
c:\perl\memory>lspm.pl d:\dumps\dfrwsl-mem.dmp 0x0414dd60
The output looks like this:
Name: dd.exe -> 0x01d9e000
There are 372 pages (1523712 bytes) to process.
Dumping process memory to dd.dmp…
Done.
Extracting the Process Image
When a process is launched, the executable file is read into memory. One of the pieces of information that can be obtained from the process details (via Ispd.pl) is the offset within the dump file to the Image Base Address. Lspd.pl can do a quick check to see whether an executable image can be found in that location. To further develop this information, the PE file header can be parsed to see whether it is possible to extract the entire contents of the executable image from the dump file.
Extracting the Process Image (Cont’d)
Lspi.pl can’t reassemble the file if any of the memory pages have been marked as invalid and are no longer located in memory. A file extracted from the memory dump will not be exactly the same as the original executable file. This is due to the fact that some of the file’s sections are writeable, and those sections changes during the process execution step.
As the process executes, various elements of the executable code (addresses, variables, and so on) change based on the environment and the stage of execution. However, there are a couple of ways to determine the nature of a file and get some information about its purpose. One of those ways is to see whether the file has any file version information compiled into it, as is done with most files created by legitimate software companies. As noticed from the section headers of the image file, there is a section named .rsrc, which is the name often used for a resource section of a PE file. This section can contain a variety of resources, such as dialogs and version strings, and is organized like a file system. The file hashing option can also be used to get this information.
Collecting Process Memory
During an investigation, the investigator is usually interested in only particular processes rather than a list of all processes, and would like more than just the contents of process memory available in RAM dump file. For example, the investigator might have quickly identified processes of interest that required no additional extensive investigation.
There are ways to collect all the memory used by a process not just what is in physical memory but what is in virtual memory or the page file as well. The pmdurnp.exe tool allows dumping the contents of process memory without stopping the process. This allows the process to continue and the contents of memory to change while being written to a file, thereby creating a “smear” of process memory. Also, prndurnp.exe does not create an output file that can be analyzed with the debugging tools.
Another method for dumping the contents of process memory is called Process Dumper. It dumps the entire process space along with additional metadata and the process environment to the console (STDOUT), so that the output can be redirected to a file or a socket.
Userdump.exe allows dumping of any process, without attaching a debugger and without terminating the process once the dump has been completed. Also, the dump file generated by userdump.exe can be read by the MS debugging tools. However, working of the userdump.exe command requires system installation of its specific driver. Once done with the dumping process, use debugging tools to analyze the dump files. Other helpful tools include:
1. Volatility
The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offers visibility into the runtime state of the system. The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research.
2. BinText
It can extract text from a file and find plain ASCII text, Unicode (double byte ANSI) text, and Resource strings, providing useful information for each item in the optional “advanced” view mode. Its comprehensive filtering helps prevent listing of unwanted. The gathered list can be searched and saved to a separate file as either a plain text file or in informative tabular format.
3. Handle
Handle is a utility that displays information about open handles for any process in the system. You can use it to see the programs that have open files or to see the object types and names of all the handles of a program.
4. ListDLLs.exe
It is a utility that reports the DLLs loaded into processes. It lists all DLLs loaded into all processes, or into a specific process. It can also list the processes that have a particular DLL loaded. ListDLLs can also display full version information for DLLs, including their digital signature, and it can be used to scan processes for unsigned DLLs.
Questions related to this topic
- How do I open a memory dump file?
- How do you analyze memory dump files?
- Is it safe to delete a memory DMP file?
- Where are windows dump files stored?
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com