VPC Network Address Translation When you associate an ENI with a public IP address, the ENI maintains its private IP address. Associating a public IP with an ENI doesn’t reconfigure the ENI with a new address. Instead, the Internet gateway maps the public IP address to the ENI’s private IP address using a process called network address translation (NAT). When an instance with a public IP connects to a host on the Internet, the host sees the traffic as originating from the instance’s public IP. For example, assume an instance with a private IP address of 172.31.7.10 is associated with the EIP 35.168.241.48. When the instance attempts to send a packet to the Internet host 198.51.100.11, it will send the following packet to the Internet gateway:
Source IP Address Destination IP Address
172.31.7.10 35.168.241.48
The Internet gateway will translate this packet to change the source IP address to the instance’s public IP address. The translated packet, which the Internet gateway forwards to the host, looks like this:
Source IP Address Destination IP Address
35.168.241.48 198.51.100.11
Likewise, when a host on the Internet sends a packet to the instance’s EIP, the Internet gateway will perform network address translation on the incoming packet. The packet that reaches the Internet gateway from the Internet host will look like this:
Source IP Address Destination IP Address
198.51.100.11 35.168.241.48
The Internet gateway will translate this packet, replacing the destination IP address with the instance’s private IP address, as follows:
Source IP Address Destination IP Address
198.51.100.11 172.31.7.10
Network address translation occurs automatically at the Internet gateway when an instance has a public IP address. You can’t change this behaviour. Network address translation as described here is also sometimes called one-to-one NAT because one private IP address gets mapped to one public IP address.
Network Address Translation Devices
Although network address translation occurs at the Internet gateway, there are two other resources that can also perform NAT.
– NAT gateway
– NAT instance AWS calls these NAT devices.
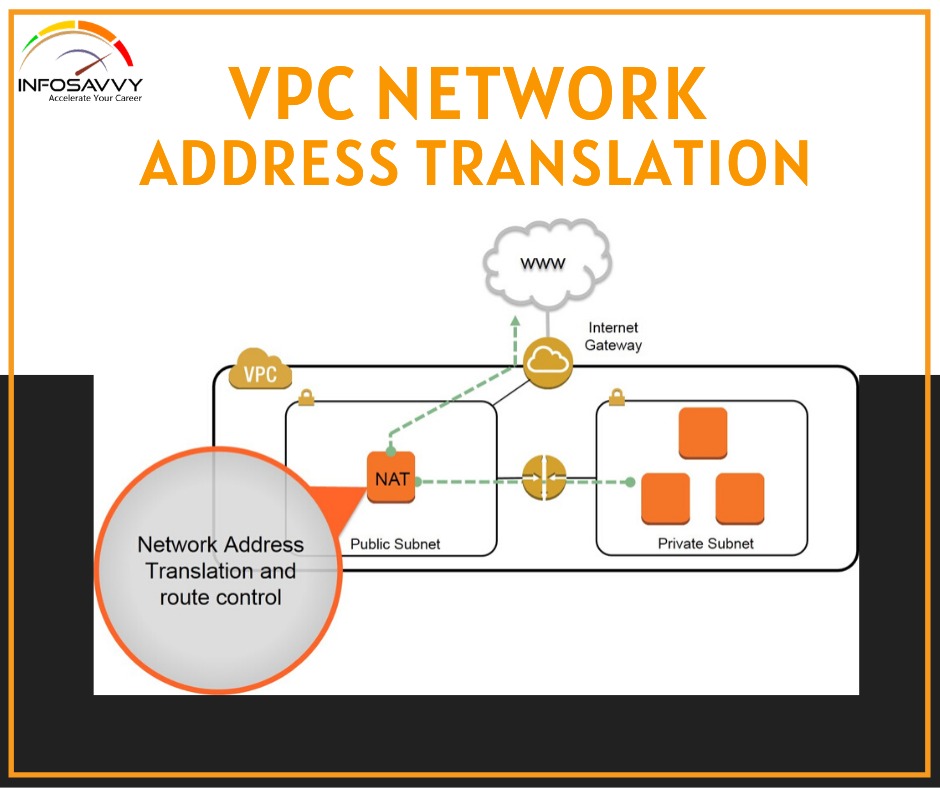
The purpose of a NAT device is to allow an instance to access the Internet while preventing hosts on the Internet from reaching the instance directly. This is useful when an instance needs to go out to the Internet to fetch updates or to upload data but does not need to service requests from clients. When you use a VPC Network Address Translation device, the instance needing Internet access does not have a public IP address allocated to it. Incidentally, this makes it impossible for hosts on the Internet to reach it directly. Instead, only the NAT device is configured with a public IP. Additionally, the VPC Network Address Translation device has an interface in a public subnet.
Refer to Table 4.7 for an example.
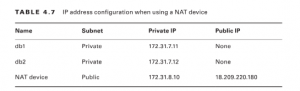
When db1 sends a packet to a host on the Internet with the address 198.51.100.11, the packet must first go to the NAT device. The NAT device translates the packet as follows:

The NAT device then takes the translated packet and forwards it to the Internet gateway. The Internet gateway performs NAT translation on this packet as follows:

Multiple instances can use the same NAT device, thus sharing the same public IP address for outbound connections. The function that NAT devices perform is also called port address translation (PAT).
Configuring Route Tables to Use NAT Devices
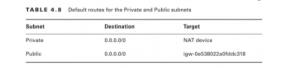
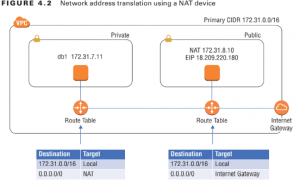
Instances that use the NAT device must send Internet-bound traffic to it, while the NAT device must send Internet-bound traffic to an Internet gateway. Hence, the NAT device and the instances that use it must use different default routes. Furthermore, they must also use different route tables and hence must reside in separate subnets. Refer to Table 4.7 again. Notice that the instances reside in the Private subnet, and the NAT device is in the Public subnet. The default routes for these subnets would follow the pattern in Table 4.8.
Refer to the diagram in Figure 4.2 to see the relationship between both of the route tables. Recall that a route target must be a VPC resource such as instance, Internet gateway, or ENI. The specific target you choose depends on the type of NAT device you use: a NAT gateway or a NAT instance.
NAT Gateway
A NAT gateway is a NAT device managed by AWS. Like an Internet gateway, it’s a one size-fits-all resource. It doesn’t come in a variety of flavours, and there’s nothing to manage or access. It automatically scales to accommodate your bandwidth requirements. You set it and forget it. When you create a NAT gateway, you must assign it an EIP. A NAT gateway can reside in only one subnet, which must be a public subnet for it to access the Internet. AWS selects a private IP address from the subnet and assigns it to the NAT gateway. For redundancy, you may create additional NAT gateways in different availability zones. After creating a NAT gateway, you must create a default route to direct Internet-bound traffic from your instances to the NAT gateway. The target you specify will be the NAT gateway ID, which follows the format nat-0750b9c8de7e75e9f. If you use multiple NAT gateways, you can create multiple default routes, each pointing to a different NAT gateway as the target. Because a NAT gateway doesn’t use an ENI, you can’t apply a security group to it. You can, however, apply a NACL to the subnet that it resides in.
NAT Instance
A NAT instance is a normal EC2 instance that uses a preconfigured Linux-based AMI. You have to perform the same steps to launch it as you would any other instance. It functions like a NAT gateway in many respects, but there are some key differences. Unlike a NAT gateway, a NAT instance doesn’t automatically scale to accommodate increased bandwidth requirements. Therefore, it’s important that you select an appropriately robust instance type. If you choose an instance type that’s too small, you must manually upgrade to a larger instance type. Also, a NAT instance has an ENI, so you must apply a security group to it. You also must remember to assign it a public IP address. Lastly, you must disable the source/destination check on the NAT instance’s ENI. This allows the NAT instance to receive traffic addressed to an IP other than its own, and it also allows the instance to send traffic using a source IP that it doesn’t own. One advantage of a NAT instance is that you can use it as a bastion host, sometimes called a jump host, to connect to instances that don’t have a public IP. You can’t do this with a NAT gateway. You must create a default route to direct Internet-bound traffic to the NAT instance. The target of the default route will be the NAT instance’s ID, which follows the format i-0a1674fe5671dcb00. If you want to guard against instance or availability zone failures, it’s not as simple as just spinning up another NAT instance. You cannot create multiple default routes pointing to different NAT instances. If you need this level of resiliency, you’re better off using NAT gateways instead.
Also Read:- AWS Elastic Block Storage Volumes and It’s Features
Related Products:- AWS Certified Solutions Architect | Associate
VPC Peering
You can configure VPC peering to allow instances in one VPC to communicate with VPCs in another over the private AWS network. You may want to do this if you have instances in different regions that need to communicate. You may also want to connect your instances to another AWS customer’s instances.
To enable VPC peering, you must set up a VPC peering connection between two VPCs. A VPC peering connection is a point-to-point connection between two and only two VPCs. You can have at most one peering connection between a pair of VPCs. Also, peered VPCs must not have overlapping CIDR blocks. With one exception, a VPC peering connection allows only instance-to-instance communication. This means an instance in one VPC can use the peering connection only to connect to another instance in the peered VPC. You can’t use it to share Internet gateways or NAT devices. You can, however, use it to share a Network Load Balancer (NLB). If you have more than two VPCs you need to connect, you must create a peering connection between each pair. You cannot daisy-chain VPC peering connections together and route through them. This configuration is called transitive routing. To use a peering connection, you must create new routes in both VPCs to allow traffic to travel in both directions. For each route, the destination prefix should exist within the destination VPC. The target of each route must be the peering connection’s identifier, which begins with pcx-. Refer to Table 4.9 for examples of two routes you would create to enable peering between a pair of VPCs.
Table 4.9 Routes for VPC peering Source VPC CIDR Destination VPC CIDR

Notice that the routes are mirrors of each other. Again, this is to allow traffic in both directions. The destination CIDR doesn’t need to exactly match that of the destination VPC. If you want to enable peering only between specific subnets, you can specify the subnet CIDR instead. Inter-region VPC peering is not available for some AWS regions. Peering connections between regions have a maximum transmission unit (MTU) of 1500 bytes and do not support IPv6.
Questions related to this topic
- How do I find my NAT gateway IP address?
- Do you need a NAT gateway for each subnet?
- How do I access my ec2 instances from the Internet?
- Does a NAT gateway require an Internet gateway?
- What is VPC Network Address Translation?
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com