By performing a penetration test, you gained access under a user account. During the test, you established a connection with your own machine via the SMB service and occasionally entered your login and password in plaintext.
Which file do you have to clean to clear the password?
Option 1 : .bashrc
Option 2 : .bash_history
Option 3 : .profile
Option 4 : .XSession-log
1. .bashrc
The .bashrc file may be a script file that’s executed when a user logs in. The file itself contains a series of configurations for the terminal session. This includes fixing or enabling: coloring, completion, shell history, command aliases, and more.
It is a hidden file and straightforward ls command won’t show the file.
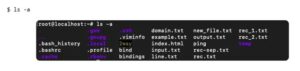
You can see the .bashrc command within the first column. The contents of .bashrc are often changed to define functions, command aliases, and customize the bash.
.bashrc file features a lot of comments that creates it easy to know .
To view the bashrc file:
$ cat .bashrc
Defining functions in bashrc
. bashrc are often wont to define functions that reduce redundant efforts. These functions are often a set of basic commands. These functions can even use arguments from the terminal.
Let’s define a function that tells the date during a more descriptive manner.
First you’ll got to enter the .bashrc enter editing mode.
$ vi .bashrc
2. .bash_history
File created by Bash, a Unix-based shell program commonly used on Mac OS X and Linux operating systems; stores a history of user commands entered at the command prompt; used for viewing old commands that are executed.
BASH_HISTORY files are hidden files with no filename prefix. They always use the filename .bash_history.
NOTE: Bash is that the shell program employed by Apple Terminal.
Our goal is to assist you understand what a file with a *.bash_history suffix is and the way to open it.
The Bash History file type, file format description, and Mac and Linux programs listed on this page are individually researched and verified by the FileInfo team. we attempt for 100% accuracy and only publish information about file formats that we’ve tested and validated.
3. .profile
.profile is for things that aren’t specifically associated with Bash, like environment variables PATH and friends, and will be available anytime. for instance , .profile should even be loaded when starting a graphical desktop session.
4. .XSession-log
If you would like to seek out more information a few problem during a session or want to repair it, consult the system log, which stores log data for your user session and applications.
The ~/.xsession-errors X session log file has been deprecated and is not any longer used.
On systemd-based systems, you’ll find the session log data within the systemd journal, which stores the info during a binary format. to look at the logs, use the journalctl command.
To view your user session logs:
1. Determine your user ID (uid) by running the subsequent command:
2. $ id –user
1000
3. View the journal logs for the user ID determined above:
$ journalctl _UID=1000
For more information on the systemd journal, see the journalctl(1) man page.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



