Ethical hacker Jane Doe is attempting to crack the password of the head of the IT department of ABC company. She is utilizing a rainbow table and notices upon entering a password that extra characters are added to the password after submitting. What countermeasure is the company using to protect against rainbow tables?
Option 1: Password key hashing
Option 2: Account lockout
Option 3: Password salting
Option 4 : Password hashing
1. Password key hashing
When a password has been “hashed” it means that it’s been became a scrambled illustration of itself. A user’s password is taken and – using a key the site to the positioning – the hash worth comes from the mix of each the password and also the key, using a set algorithm.
To verify a user’s password is correct it’s hashed and also the worth compared therewith keep on record each time they login.
You cannot directly flip a hashed worth into the password, however you can compute what the password is that if you continually generate hashes from passwords till you find one that matches, a so-called brute-force attack, or similar methods.
2. Account opposition
Security feature used with operating systems and services with a login that locks any account that has failed a login try quite a group parameter. for example, a system might be started to lock an account for one hour if the user fails the login 5 times in 10 minutes. Account opposition keeps the account secure by preventing anyone or something from guessing the username and password. once your account is locked, you must wait the set amount of time before being able to log into your account once more. within the image below of the Windows XP office, is Associate in Nursing example of where this policy can be started in Windows.
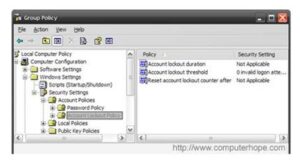
In the above example image, are 3 default policies. The Account lockout duration permits you to specify how many minutes the account remains secured once triggered. The Account lockout threshold permits you to specify how many invalid logins will occur before locking the account. Finally, the Reset account opposition counter when specifies the length in minutes the counter can reset if there have been no failed tries. a decent setting for many users is sixty, 10, and 30.
3. Password salting
Passwords are usually delineated as “hashed and salted”. salting is simply the addition of a unique, random string of characters renowned solely to the site to every parole before it’s hashed, typically this “salt” is placed in front of each password.
The salt value needs to be hold on by the site, which means typically sites use the same salt for each parole. This makes it less effective than if individual salts are used.
The use of unique salts means that common passwords shared by multiple users – like “123456” or “password” – aren’t revealed revealed when one such hashed password is known – because despite the passwords being the same the immediately and hashed values are not.
Large salts also protect against certain methods of attack on hashes, including rainbow tables or logs of hashed passwords previously broken.
Both hashing and salting may be repeated more than once to increase the issue in breaking the security.
4. Password hashing
For security reasons, you’ll need to store passwords in hashed kind. This guards against the possibility that someone who gains unauthorized access to the information will retrieve the passwords of each user within the system. Hashing performs a one-way transformation on a password, turning the parole into another String, called the hashed password. “One-way” means that it’s much not possible to travel the other means – to show the hashed password into the first password. There are many mathematically advanced hashing algorithms that fulfill these desires. By default, the Personalization module uses the MD5 algorithm to perform a one-way hash of the password value and to store it in hashed kind.
The hashed password value is not encrypted before it’s hold on within the information. once a member tries to log in, the Personalization module takes the supplied password, performs the same one-way hash and compares it to the database value. If the passwords match, then login is successful.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



