Samuel a security administrator, is accessing the configuration of a web server. He noticed that the server permits SSLv2 connections, and the same private key certificate is used on a different server that allows SSLv2 connections. This vulnerability makes the web server vulnerable to attack as the SSLv2 server can leak key information. Which of the following attack can be performed by exploiting the above vulnerability?
Option 1 : Padding oracle attack
Option 2 : DUHK attack
Option 3 : DROWN attack
Option 4 : Side-channel attack
1. Padding oracle attack
In cryptography, a padding oracle attack is an attack that uses the padding validation of a cryptographic message to decrypt the ciphertext. In cryptography, variable-length plaintext messages typically have to be padded (expanded) to be compatible with the underlying cryptographic primitive. The attack depends on having a “padding oracle” who freely responds to queries regarding whether or not a message is properly padded or not. padding oracle attacks area unit principally related to complete blood count mode secret writing used at intervals block ciphers. padding modes for uneven algorithms like OAEP may additionally be vulnerable to padding oracle attacks.
In symmetric cryptography, the cushioning oracle attack are often applied to the cbc mode of operation, wherever the “oracle” (usually a server) leaks information regarding whether or not the cushioning of AN encrypted message is correct or not. Such information will permit attackers to decode (and generally encrypt) messages through the oracle victimization the oracle’s key, while not knowing the secret writing key.
Padding oracle attack on complete blood count secret writing
The standard implementation of cbc secret writing in block ciphers is to decode all ciphertext blocks, validate the padding, take away the PKCS7 padding, and return the message’s plaintext. If the server returns AN “invalid padding” error instead of a generic “decryption failed” error, the attacker will use the server as a padding oracle to decrypt (and generally encrypt) messages.
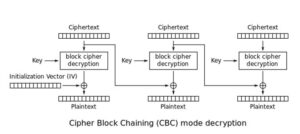
The mathematical formula for CBC decryption is
As delineated higher than, CBC decryption XORs every plaintext block with the previous ciphertext block. As a result, one-byte modification in block can build a corresponding amendment to a single computer memory unit in.
Suppose the attacker has 2 ciphertext blocks and they need to decode the second block to induce plaintext . The attacker changes the last byte of (creating ) and sends to the server. The server then returns whether or not or not the padding of the last decrypted block ( ) is correct (equal to 0x01). If the padding is correct, the wrongdoer currently knows that the last computer memory unit of is . Therefore, . If the padding is incorrect, the attacker will amendment the last byte of to future attainable worth. At most, the wrongdoer can need to build 256 makes an attempt (one guess for each possible byte) to search out the last byte of . If the decrypted block contains padding info or bytes used for padding then an extra try can have to be compelled to be created to resolve this ambiguity.
After determining the last byte of , the attacker will use an equivalent technique to get the second-to-last computer memory unit of . The attacker sets the last byte of to by setting the last byte of to . The attacker then uses an equivalent approach described higher than, now modifying the second-to-last computer memory unit till the padding is correct (0x02, 0x02).
If a block consists of 128 bits (AES, for example), that is sixteen bytes, the attacker can get plaintext in no over over 4080 makes an attempt. this is often significantly faster than the makes an attempt needed to bruteforce a 128-bit key.
Encrypting messages with padding oracle attack (CBC-R)
CBC-R turns a decryption oracle into associate degree encoding oracle, and is primarily incontestible against padding oracles.
Using padding oracle attack CBC-R will craft an initialization vector and ciphertext block for any plaintext:
- decrypt any ciphertext Pi = PODecrypt( Ci ) XOR Ci?1,
- select previous cipherblock Cx?1 freely,
- produce valid ciphertext/plaintext pair Cx-1 = px XOR PODecrypt( Ci ).
To generate a ciphertext that’s N blocks long, attacker should perform N numbers of cushioning oracle attacks. These attacks are chained along so that correct plaintext is made in reverse order, from finish of message (CN) to starting message (C0, IV). In every step, padding oracle attack beginning to construct the IV to the previous chosen ciphertext.
The CBC-R attack won’t work against an encryption theme that authenticates ciphertext (using a message authentication code or similar) before decrypting.
2. DUHK attack
DUHK (Don’t Use Hard-coded Keys) could be a vulnerability that affects devices victimization the ANSI X9.31 Random number Generator (RNG) in conjunction with a hard-coded seed key. The ANSI X9.31 RNG is AN rule that till recently was usually wont to generate cryptographic keys that secure VPN connections and web browsing sessions, preventing third parties from reading intercepted communications.
DUHK allows attackers to recover secret secret writing keys from vulnerable implementations and rewrite and skim communications passing over VPN connections or encrypted internet sessions. The encrypted information might include sensitive business information, login credentials, credit card information and alternative confidential content.
The affected implementations were all traditionally compliant with FIPS, the Federal IP Standards.
Who is vulnerable?
Traffic from any VPN using FortiOS four.3.0 to FortiOS four.3.18 can be decrypted by a passive network someone who will observe the encrypted handshake traffic. alternative key recovery attacks on completely different protocols may additionally be possible.
We additionally found eleven alternative historically FIPS-certified implementations that document hard-coded X9.31 RNG seed keys in their product. we offer the total list in our paper.
Users of affected product should apply the latest software updates.
A device is at risk of DUHK if:
- It uses the X9.31 random variety generator
- The seed key used by the generator is hard-coded into the implementation
- The output from the random number generator is directly used to generate cryptographic keys
- At least a number of the random numbers before or once those wont to make the keys are transmitted unencrypted. this is typically the case for SSL/TLS and IPsec.
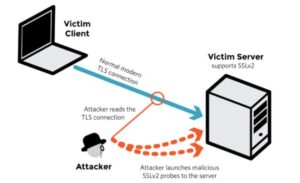
3. DROWN attack
DROWN is a serious vulnerability that affects HTTPS and other services that deem SSL and TLS, some of the essential cryptographic protocols for net security. These protocols allow everyone on the net to browse the net, use email, look on-line, and send instant messages while not third-parties being able to browse the communication.
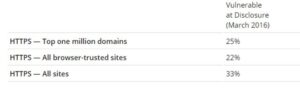
DROWN allows attackers to break the encryption and read or steal sensitive communications, as well as passwords, credit card numbers, trade secrets, or financial data. At the time of public disclosure on March 2016, our measurements indicated thirty third of all HTTPS servers were vulnerable to the attack. fortuitously, the vulnerability is much less prevalent currently. As of 2019, SSL Labs estimates that one.2% of HTTPS servers are vulnerable.
What will the attackers gain?
Any communication between users and the server. This typically includes, however isn’t limited to, usernames and passwords, credit card numbers, emails, instant messages, and sensitive documents. under some common scenarios, an attacker can also impersonate a secure web site and intercept or change the content the user sees.
Who is vulnerable?
Websites, mail servers, and other TLS-dependent services are in danger for the DROWN attack. At the time of public disclosure, many popular sites were affected. we used Internet-wide scanning to live how many sites are vulnerable:
Operators of vulnerable servers got to take action. there’s nothing practical that browsers or end-users will do on their own to protect against this attack.
Is my site vulnerable?
Modern servers and shoppers use the TLS encryption protocol. However, because of misconfigurations, several servers also still support SSLv2, a 1990s-era precursor to TLS. This support did not matter in practice, since no up-to-date clients really use SSLv2. Therefore, despite the fact that SSLv2 is thought to be badly insecure, until now, simply supporting SSLv2 wasn’t thought of a security problem, is a clients never used it.
DROWN shows that merely supporting SSLv2 may be a threat to fashionable servers and clients. It modern associate degree attacker to modern fashionable TLS connections between up-to-date clients and servers by sending probes to a server that supports SSLv2 and uses the same private key.
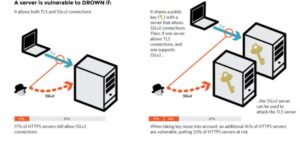
A server is vulnerable to DROWN if:
- It allows SSLv2 connections. This is surprisingly common, due to misconfiguration and inappropriate default settings.
- Its private key is used on any other serverthat allows SSLv2 connections, even for another protocol. Many companies reuse the same certificate and key on their web and email servers, for instance. In this case, if the email server supports SSLv2 and the web server does not, an attacker can take advantage of the email server to break TLS connections to the web server.
How do I protect my server?
To protect against DROWN, server operators need to ensure that their private keys software used anyplace with server computer code that enables SSLv2 connections. This includes net servers, SMTP servers, IMAP and POP servers, and the other software that supports SSL/TLS.
Disabling SSLv2 is difficult and depends on the particular server software. we offer instructions here for many common products:
OpenSSL: OpenSSL may be a science library employed in several server merchandise. For users of OpenSSL, the simplest and recommended solution is to upgrade to a recent OpenSSL version. OpenSSL 1.0.2 users ought to upgrade to 1.0.2g. OpenSSL 1.0.1 users ought to upgrade to one.0.1s. Users of older OpenSSL versions ought to upgrade to either one in every of these versions. (Updated March thirteenth, 16:00 UTC) Microsoft IIS (Windows Server): Support for SSLv2 on the server aspect is enabled by default only on the OS versions that correspond to IIS 7.0 and IIS seven.5, particularly Windows scene, Windows Server 2008, Windows seven and Windows Server 2008R2. This support is disabled within the appropriate SSLv2 subkey for ‘Server’, as outlined in KB245030. albeit users haven’t taken the steps to disable SSLv2, the export-grade and 56-bit ciphers that build DROWN possible don’t seem to be supported by default.
Network Security Services (NSS): NSS may be a common science library designed into several server merchandise. NSS versions three.13 (released back in 2012) and higher than ought to have SSLv2 disabled by default. (A little variety of users might have enabled SSLv2 manually and can got to take steps to disable it.) Users of older versions ought to upgrade to a more moderen version. we tend to still advocate checking whether or not your non-public secret is exposed elsewhere
Other affected software and in operation systems:
Instructions and data for: Apache, Postfix, Nginx, Debian, Red Hat
Browsers and other consumers: practical nothing practical that net browsers or different client computer code will do to stop DROWN. only server operators ar ready to take action to guard against the attack.
4. Side-channel attack
A side-channel attack (SCA) may be a security exploit that involves collecting info about what a machine will once it’s performing science operations and using that info to reverse engineer the device’s cryptography system. In computing, a aspect channel is any communication channel that’s incidental to another communication channel. Security investigator Paul Kocher is attributable with coining the term side-channel attack within the credited once he discovered it had been potential to reverse engineer security tokens by watching a computer’s power consumption and magnetic force emissions.
Unlike several different styles of security exploits, side-channel attacks ar hardware and software agnostic. rather than targeting a software vulnerability caused by a coding error or configuration drift, the aggressor exploits the method the device’s OS (OS) accesses the hardware upon that the OS runs. Side-channel attacks is launched against any OS, as well as Windows and linux.
Types of Side-Channel Attacks
Side-channel attacks work by monitoring the emissions produced by electronic circuits once the victim’s pc is getting used. in addition to exploiting data concerning power consumption and electromagnetic fields, an attacker may very well hear the sounds a central process unit (CPU) produces and use that data to reverse engineer what the pc is doing. this sort of side-channel attack is named an acoustic cryptanalysis attack. alternative types of side-channel attack include:
Cache attacks that exploit however and once cache is accessed in a physical system.
Differential fault analysis attacks that ask for to gleam data from a system by introducing faults into the system’s computations.
Timing attacks that track the movement of data to and from a system’s electronic equipment and memory.
Thermal-imaging attacks that use infrared images to watch the surface of a cpu chip and collect dead code.
Optical side-channel attacks that collect data concerning disc activity by employing a audio/visual recorder, like a video camera.
Van Eck phreaking may be a style of eavesdropping that involves observance the magnetic attraction fields made by information because it moves through the pc.
How to forestall Side-Channel Attacks
To prevent side-channel attacks, users have 2 choices: they need to either cut back the discharge of electromagnetic data that might be wont to launch associate attack or they need to build it not possible for an attacker to link data concerning what the electronic equipment is doing with specific work out operations. as an example, a pc engineer might want to vary the order of operations used on information among the system by employing a method known as randomization to form it tougher for an attacker to launch a side-channel attack.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com




I blog quite often and I genuinely thank you for your information. Your article has truly
peaked my interest. I’m going to take a note of your site
and keep checking for new information about once per week.
I subscribed to your Feed too.