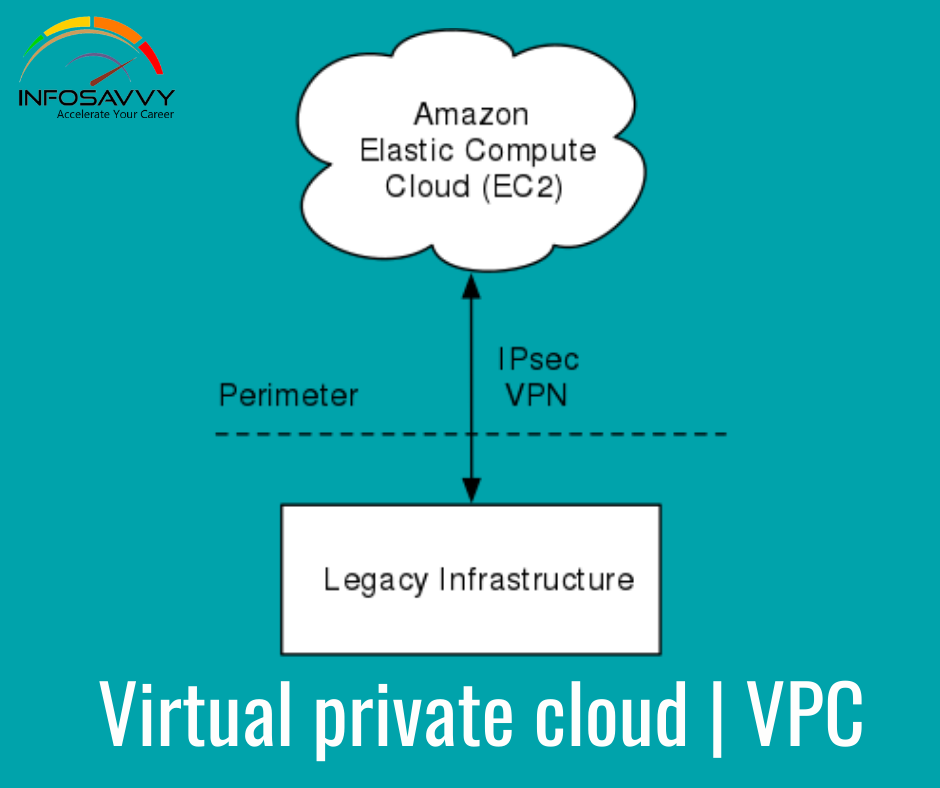
CISSP Security and Risk Management – Bk2D1
Overview Security and Risk Management in this Domain 1 of the (ISC)2® CBK lays the foundation for the entire course, introducing concepts and principles that will be utilized throughout. It is imperative that the candidate learn and understand these thoroughly, if the candidate is not already familiar with the material from professional practice. NOTE: Throughout this domain and much of the rest of the course material, the term “organization” will be used to describe operational entities; …