Learning MAC Addresses
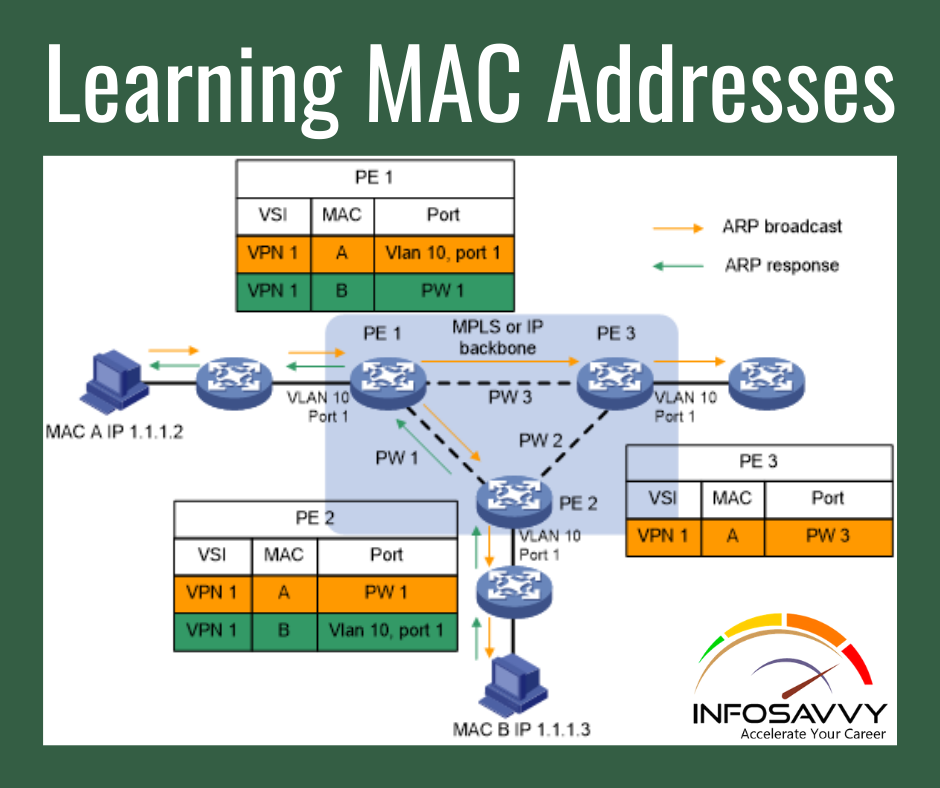
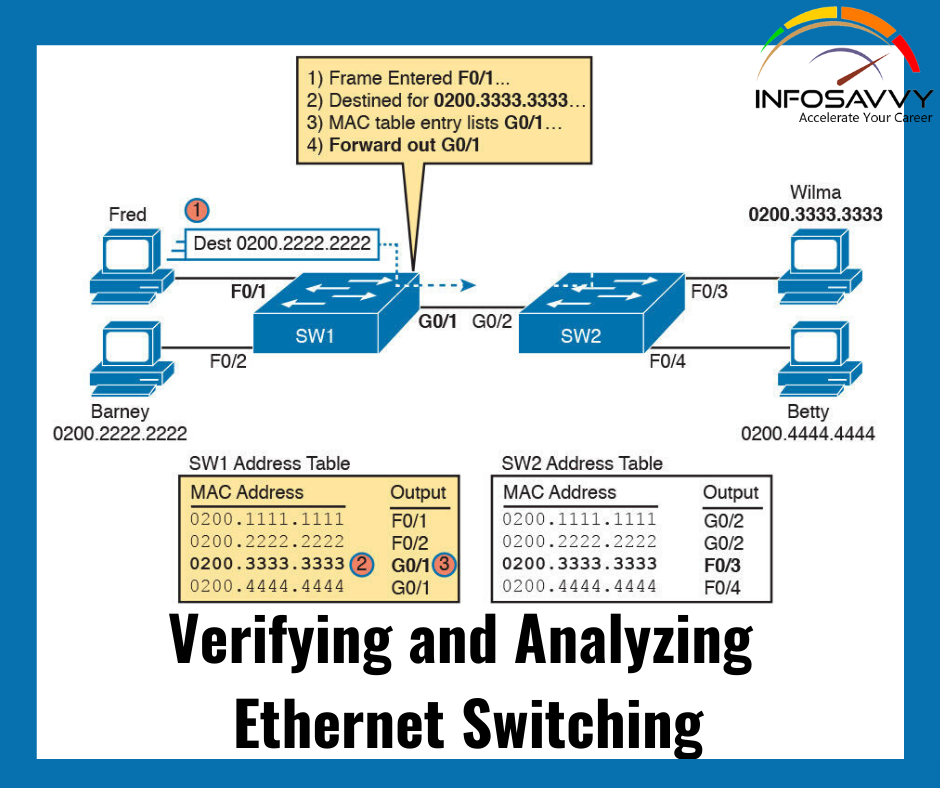
Learning MAC Addresses Thankfully, the networking staff doesn’t need to type altogether those MAC table entries. Instead, the switches do their second main function: to learn the MAC addresses and interfaces to place into its address table. With an entire MAC address table, the switch can make accurate forwarding and filtering decisions as just discussed. Switches build the address table by listening to incoming frames and examining the source MAC address within the frame. If …