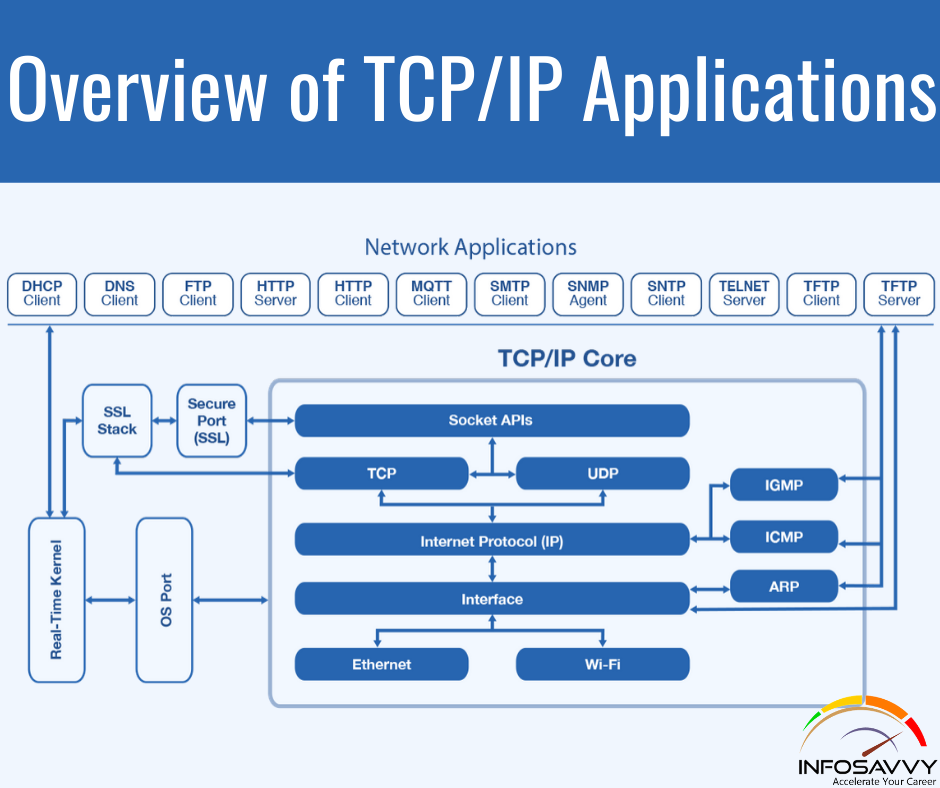
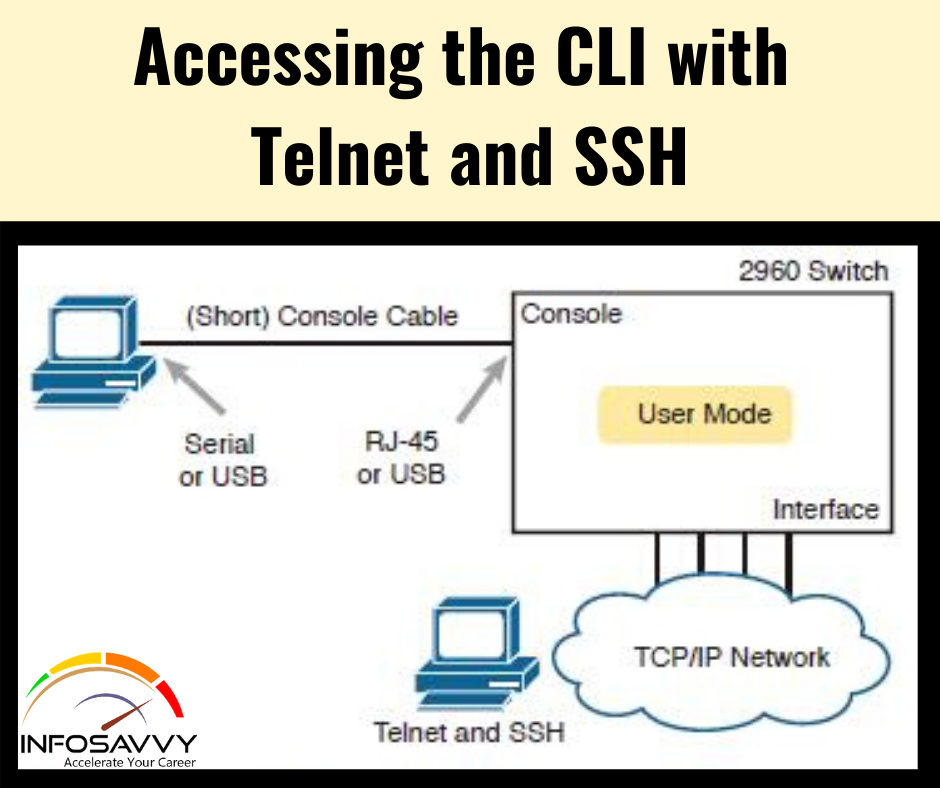
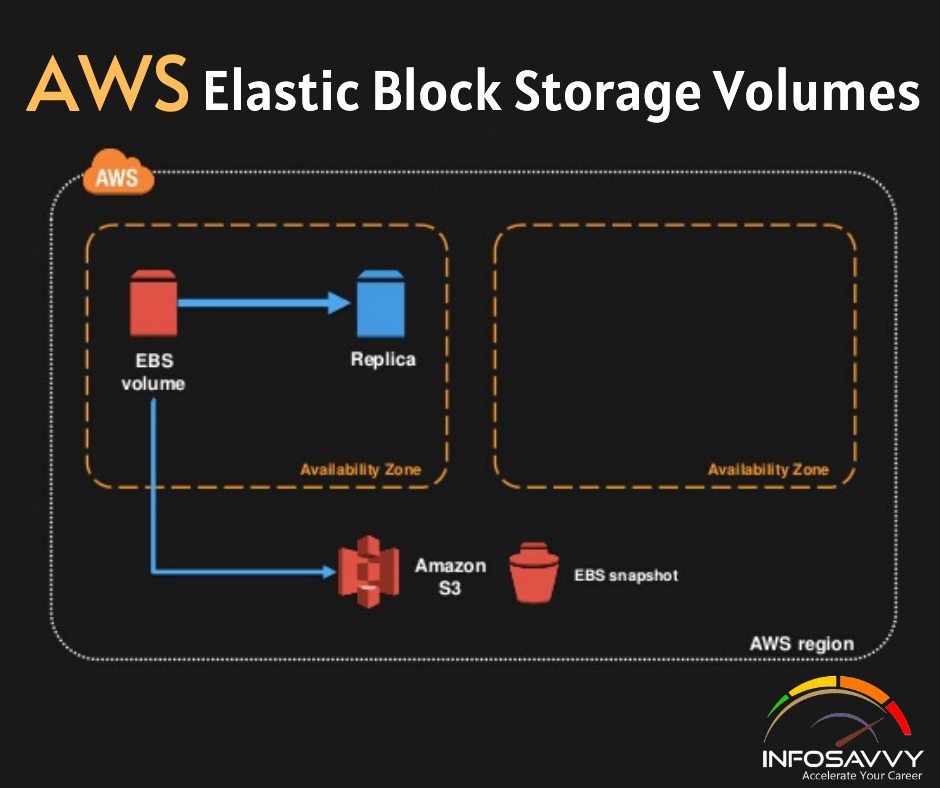
Top 12 Common Cybersecurity Analyst Interview Questions with Answers
This article is based on Top 12 Common cybersecurity analyst Interview Questions with Answers as well as job related Introduction. Introduction Cybersecurity jobs became one among the foremost in-demand jobs within the IT industry today. With demand, there’s also competition, and to urge employment in Cybersecurity, you would like to be one among the simplest . While having the required Cybersecurity skills is half job done, cracking the interview is another chapter altogether. And to …
Top 12 Common Cybersecurity Analyst Interview Questions with Answers Read More »