Dynamic Host Configuration Protocol
How Dynamic Host Configuration Protocol (DHCP) Works is a client/server protocol that gives an IP address to an IP host. additionally, to the IP address, the DHCP server also provides configuration-related information like the default gateway and subnet mask. When a Dynamic Host Configuration Protocol client device boots up, it participates in traffic broadcasting.
DHCP can assign IP configuration to hosts connecting to a network. The distribution of IP configuration to hosts simplifies the administrator’s work to take care of IP networks.
“We’re changing the world with technology”
DHCP servers maintain TCP/IP configuration information during a database like valid TCP/IP configuration parameters, valid IP addresses, and duration of the lease offered by the server. It provides address configurations to DHCP-enabled clients within the sort of a lease offer.
Related Product:- Certified Ethical Hacker | CEH Certification
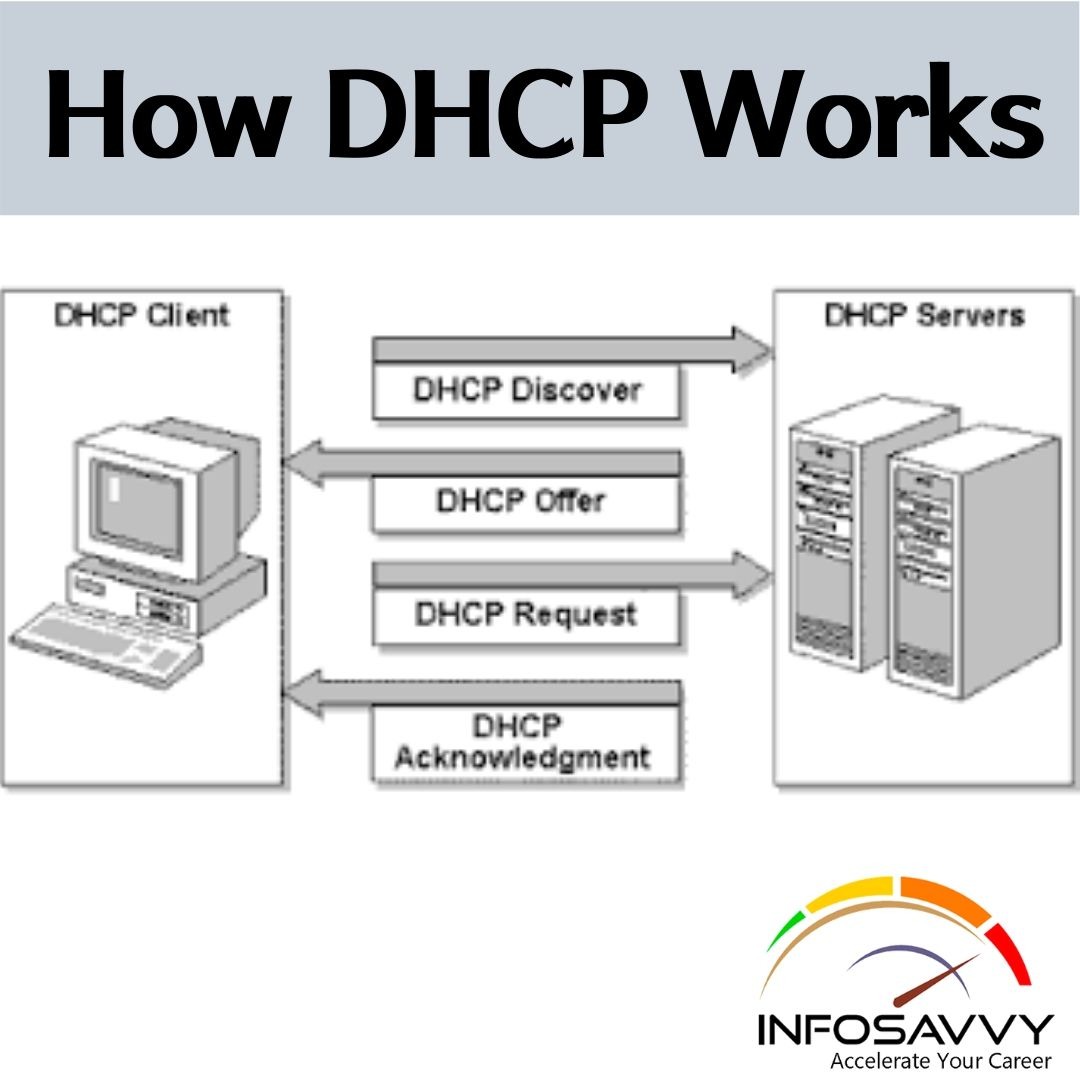
Working of DHCP:
- The client broadcasts DHCPDISCOVER/SOLICIT request asking for DHCP Configuration information.
- DHCP-relay agent captures the client request and unicasts it to the DHCP servers available within the network.
- Relay agent broadcasts DHCPOFFER/ADVERTISE within the client’s subnet.
- The client broadcasts DHCPREQUEST/REQUEST asking DHCP server to supply the DHCP configuration information.
- The DHCP server sends unicast DHCPACK/REPLY message to the client with the IP config and information.
Benefits of DHCP
DHCP provides the following benefits.
- Reliable IP address configuration. DHCP minimizes configuration errors caused by manual IP address configuration, such as typographical errors, or address conflicts caused by the assignment of an IP address to more than one computer at the same time.
- Reduced network administration. DHCP includes the following features to reduce network administration:
- Centralized and automated TCP/IP configuration.
- The ability to define TCP/IP configurations from a central location.
- The ability to assign a full range of additional TCP/IP configuration values by means of DHCP options.
- The efficient handling of IP address changes for clients that must be updated frequently, such as those for portable devices that move to different locations on a wireless network.
- The forwarding of initial DHCP messages by using a DHCP relay agent, which eliminates the need for a DHCP server on every subnet.
DHCP port number for the server is 67 and for the client is 68. It is a Client-server protocol which uses UDP services. An IP address is assigned from a pool of addresses. In Training ECIHv2 you learn How DHCP works join Infosavvy Chennai Location.
Also Read:- DHCP Request/Reply Messages
Questions related to this topic
- What are the steps a client uses to acquire an address from a DHCP server?
- What is the IP address of the DHCP server?
- What are the 4 steps of DHCP?
- How does DHCP assign IP addresses?
- How Dynamic Host Configuration Protocol (DHCP) Works?
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Foot printing Penetration Testing
- Different types of tools with Email Foot printing
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Foot printing tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grapping
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com