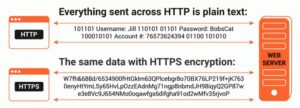
Bella, a security professional working at an IT firm, finds that a security breach has occurred while transferring important files. Sensitive data, employee username, and passwords are shared in plaintext, paving the way for hackers to perform successful session hijacking. To address this situation, Bella implemented a protocol that sends data using encryption and digital certifications. Which of the following protocols is used by Bella?
Option 1 : HTTPS
Option 2 : FTP
Option 3 : IP
Option 4 : FTPS
1. HTTPS
HTTPS is the shortening for hypertext move convention secure, or secure hypertext move convention in the event that you are not a fanatic for semantics.
How Does HTTPS Work?
Dissimilar to HTTP, HTTPS utilizes a protected testament from an outsider seller to make sure about an association and confirm that the site is genuine. This safe authentication is known as a SSL Certificate (or “cert”).
SSL is a truncation for “secure attachments layer”. This is the thing that makes a safe, encoded association between a program and a worker, which secures the layer of correspondence between the two.
This declaration encodes an association with a degree of insurance that is assigned at your season of the acquisition of a SSL endorsement.
A SSL endorsement gives an additional layer of security for touchy information that you don’t need outsider aggressors to get to. This extra security can be critical with regards to running online business sites.
A few Examples:
- When you need to make sure about the transmission of Mastercard information or other delicate data, (for example, somebody’s genuine location and actual personality).
- When you run a lead age site that depends on somebody’s genuine data, wherein case you need to utilize HTTPS to protect against malevolent assaults on the client’s information.
There are numerous advantages to HTTPS that merit the slight expense. Keep in mind, if the declaration is absent, an outsider could undoubtedly check the association for delicate information.
What is TLS? How it Applies to HTTPS
TLS represents transport layer security. It encodes HTTPS and can be utilized to make sure about email and different conventions. It utilizes cryptographic methods that guarantee information has not been altered since it was sent, that interchanges are with the real individual the correspondence came from, and to keep private information from being seen.
Things kick off with a TLS handshake, the cycle that commences a correspondence meeting that utilizes TLS encryption. This is the place where verification happens, and meeting keys are made. Shiny new meeting keys are produced when two gadgets impart, from the two unique keys cooperating. The consequence of this is more profound, more encoded correspondence.
A Critical Step for HTTPS — Authenticating the Web Server
The most basic advance for a HTTPS secure association is guaranteeing that a web worker is who they say they are.
That is the reason the SSL authentication is the main piece of this arrangement; it guarantees the proprietor of the webserver is who they say the declaration says it is. It working correspondingly to how a driver’s permit functions — it affirms the character of the proprietor of the worker.
A layer of assurance from specific kinds of assaults exists when you actualize HTTPS, making this an important staple of your site.
2. FTP
FTP is a record move convention that does exclude any alternatives for scrambling information on the way. It was initially intended for use in private logical and examination organizations and depends on a particular characterized in 1985 by the Internet Engineering Task Force in RFC 959. FTP utilizes two associations with send information. Validation information (e.g., usernames and passwords) is traded on an order channel. Information records are sent on a different channel that is set up after the verification is finished.
Secure FTP is a wide term that alludes to two distinct advancements that can encode both confirmation data and information records on the way.
FTPS alludes to make sure about FTP that utilizes SSL or TLS for encryption. FTPS is fundamentally the same as FTP and uses expansions to FTP that add uphold for the Transport Layer Security (TLS RFC 4217) and Secure Socket Layer (SSL RFC 2228) conventions. Like FTP, FTPS utilizes two associations – an order channel and an information channel. You can pick whether to encode the two associations or just the information channel.
SFTP alludes to the utilization of Secure Shell or SSH network convention to trade information over a safe channel. Dissimilar to FTP and FTPS, the SFTP convention is just a draft determination, which can cause little incongruencies between SFTP customer and working usage. SFTP utilizes just a single association and scrambles both verification data and information records being moved.
Secure FTP conventions ensure information just while it is being communicated. When information records have been kept in touch with a safe FTP working, the information is not, at this point secured except if the documents were scrambled before transmission. A commonplace situation is to scramble records utilizing a device like PGP and afterward communicate utilizing either SFTP or FTPS.
3. IP
The Internet Protocol (IP) is the primary interchanges convention in the Internet convention suite for handing-off datagrams across network limits. Its directing capacity empowers internet working, and basically sets up the Internet.
IP has the undertaking of conveying bundles from the source host to the objective host exclusively dependent on the IP addresses in the parcel headers. For this reason, IP characterizes bundle structures that embody the information to be conveyed. It likewise characterizes tending to strategies that are utilized to mark the datagram with source and objective data.
Generally, IP was the connectionless datagram administration in the first Transmission Control Program presented by Vint Cerf and Bob Kahn in 1974, which was supplemented by an association arranged assistance that turned into the reason for the Transmission Control Protocol (TCP). The Internet convention suite is thusly frequently alluded to as TCP/IP.
4. FTPS
The File Transfer Protocol (FTP) is a standard organization convention utilized for the exchange of PC records from a worker to a customer on a PC organization. FTP is based on a customer worker model engineering utilizing separate control and information associations between the customer and the server.[1] FTP clients may validate themselves with an unmistakable book sign-in convention, ordinarily as a username and secret key, however can interface namelessly if the worker is designed to permit it. For secure transmission that ensures the username and secret phrase, and scrambles the substance, FTP is frequently made sure about with SSL/TLS (FTPS) or supplanted with SSH File Transfer Protocol (SFTP).
The primary FTP customer applications were order line programs created prior to working frameworks had graphical UIs, are as yet dispatched with most Windows, Unix, and Linux working systems.[2][3] Many FTP customers and mechanization utilities have since been created for working areas, workers, cell phones, and equipment, and FTP has been fused into profitability applications, for example, HTML editors.
Learn CEH & Think like hacker
- What is Ethical Hacking? & Types of Hacking
- 5 Phases of Hacking
- 8 Most Common Types of Hacker Motivations
- What are different types of attacks on a system
- Scope and Limitations of Ethical Hacking
- TEN Different Types Of Hackers
- What is the Foot-printing?
- Top 12 steps for Footprinting Penetration Testing
- Different types of tools with Email Footprinting
- What is “Anonymizer” & Types of Anonymizers
- Top DNS Interrogation Tools
- What is SNMP Enumeration?
- Top vulnerability scanning tools
- Information Security of Threat
- Footprinting tools:
- What is Enumeration?
- Network Security Controls
- What is Identity and Access Management?
- OWASP high TEN web application security risks
- Password Attacks
- Defend Against Key loggers
- Defend Against Spyware
- Covering Tracks
- Covering Track on Networks
- Everything You Need To Know About Sniffing – Part 1
- Everything You Need To Know About Sniffing – Part 2
- Learn more about GPS Spyware & Apparatuses
- Introduction of USB Spyware and It’s types
- 10 Types of Identity Theft You Should Know About
- Concepts of Denial-of-Service Attack & Distributed Denial of Service Attack
- Most Effective Ways to Overcome Impersonation on the Social Networking Site’s Problem
- How Dynamic Host Configuration Protocol (DHCP) Works
- DHCP Request/Reply Messages
- DHCP Starvation Attack
- Rogue DHCP Server Attack
- IOS Switch Commands
- Web Server Concept
- Web Server Attacks
- Web Server Attack Tools
- Web Server Security Tools
- 6 Quick Methodology For Web Server Attack
- Learn Skills From Web Server Foot Printing / Banner Grabbing
- The 10 Secrets You Will Never Know About Cyber Security And Its Important?
- Ways To Learn Finding Default Content Of Web Server Effectively
- How will Social Engineering be in the Future
- Understand The Background Of Top 9 Challenges IT Leaders Will Face In 2020 Now
- Learning Good Ways To Protect Yourself From Identity Theft
- Anti-phishing Tools Guide
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092
Contact us – www.info-savvy.com



