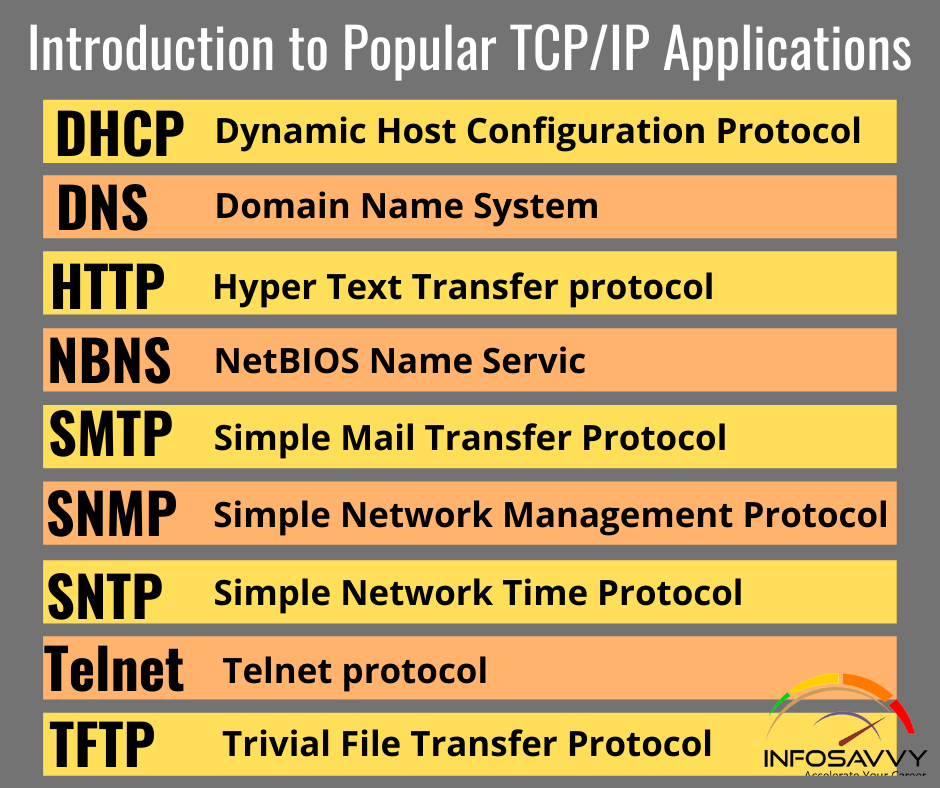
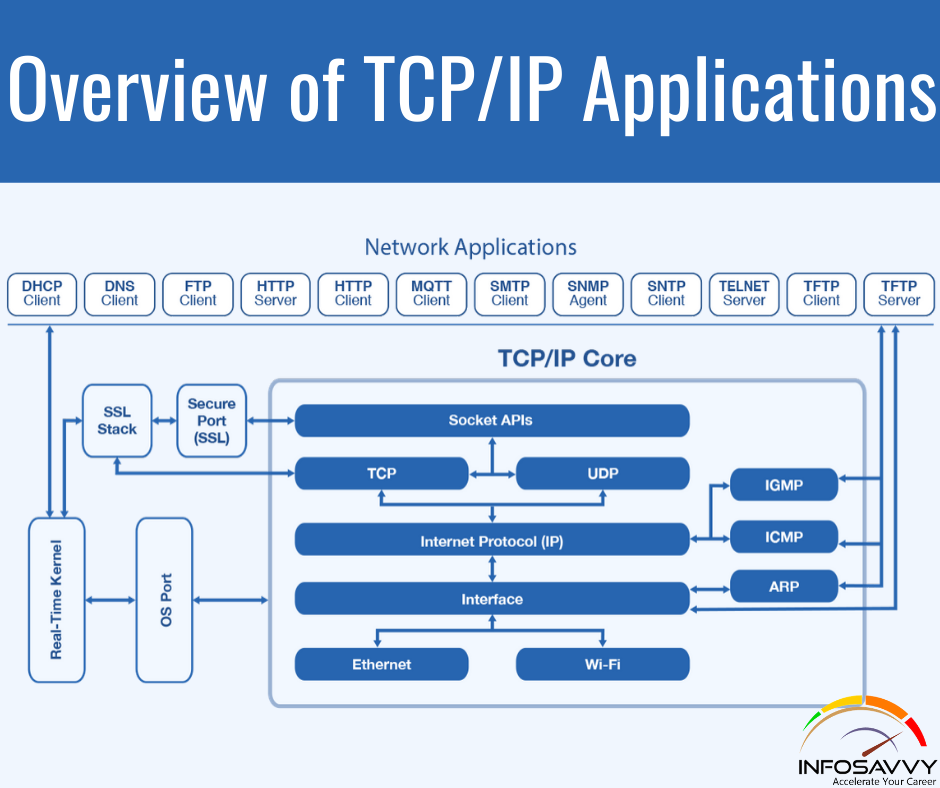
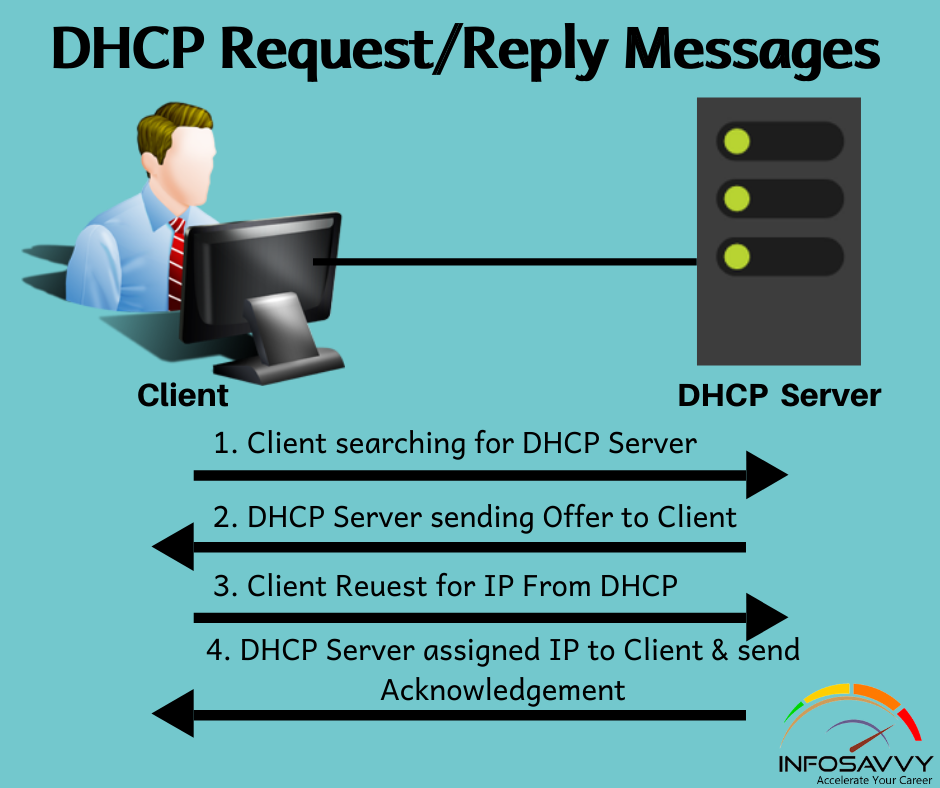
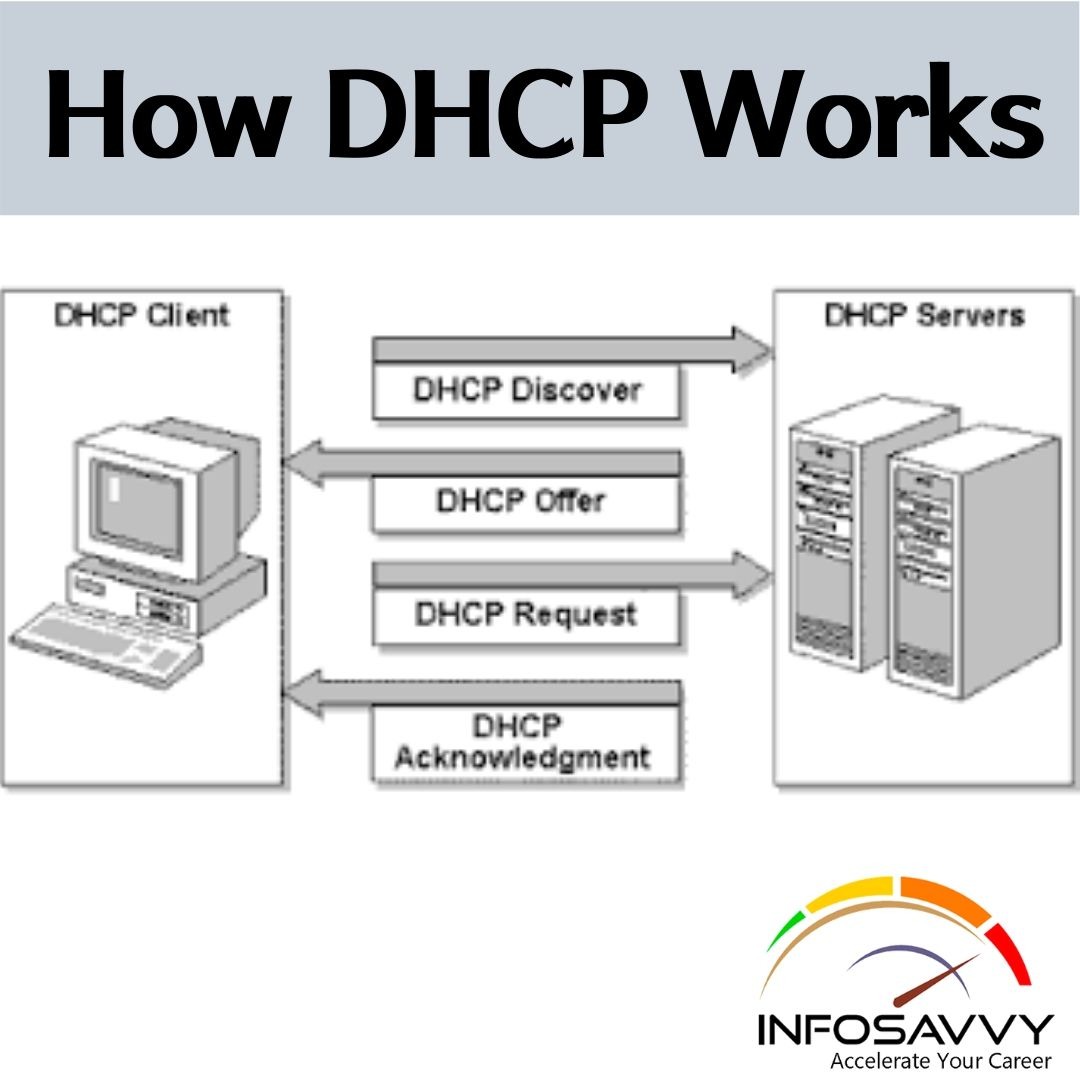
Introduction to Popular TCP/IP Applications
Introduction to Popular TCP/IP Applications in this article throughout your preparation for the CCNA Routing and Switching exams, you’ll come across a variety of TCP/IP applications. you ought to a minimum of remember of some of the applications which will be wont to help manage and control a network. The World Wide Web (WWW) application exists through web browsers accessing the content available on web servers. Although it’s often thought of as an end-user application, …