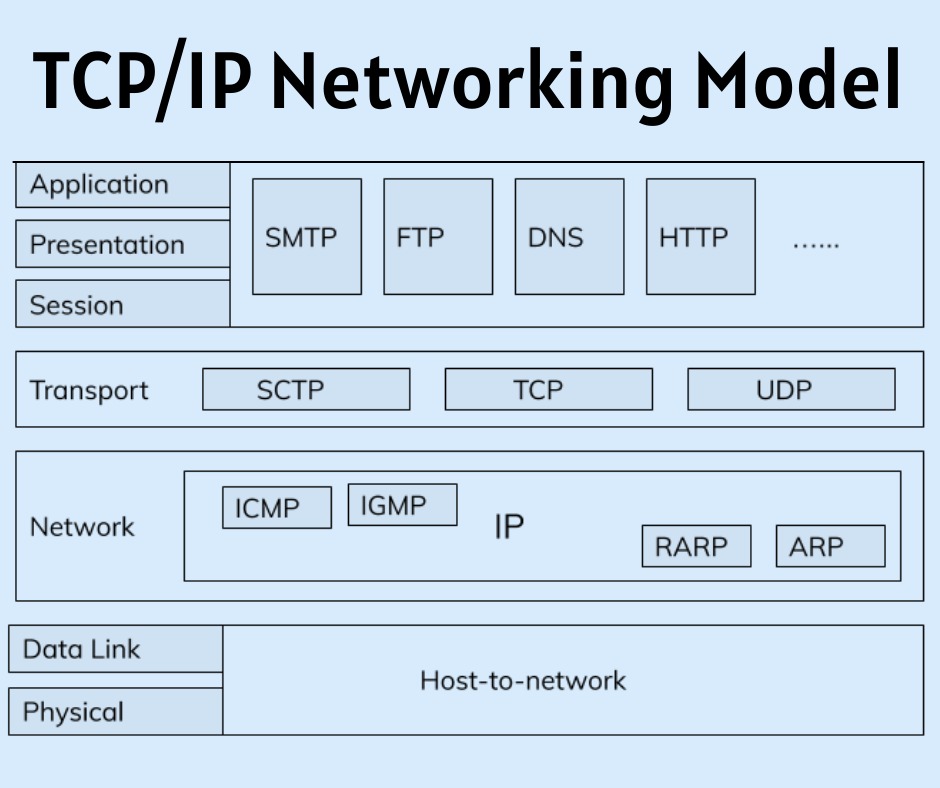
Overview of the TCP/IP Networking Model
This blog is on TCP/IP networking model in that Overview has given as well as there different layer has been explained. Overview The TCP/IP model both defines and references a large collection of protocols that allow computers to communicate. To define a protocol, TCP/IP uses documents called Requests For Comments (RFC). (You can find these RFCs using any online search engine.) The TCP/IP model also avoids repeating work already done by another standards body or …