Introduction of Amazon Elastic Compute Cloud (EC2)
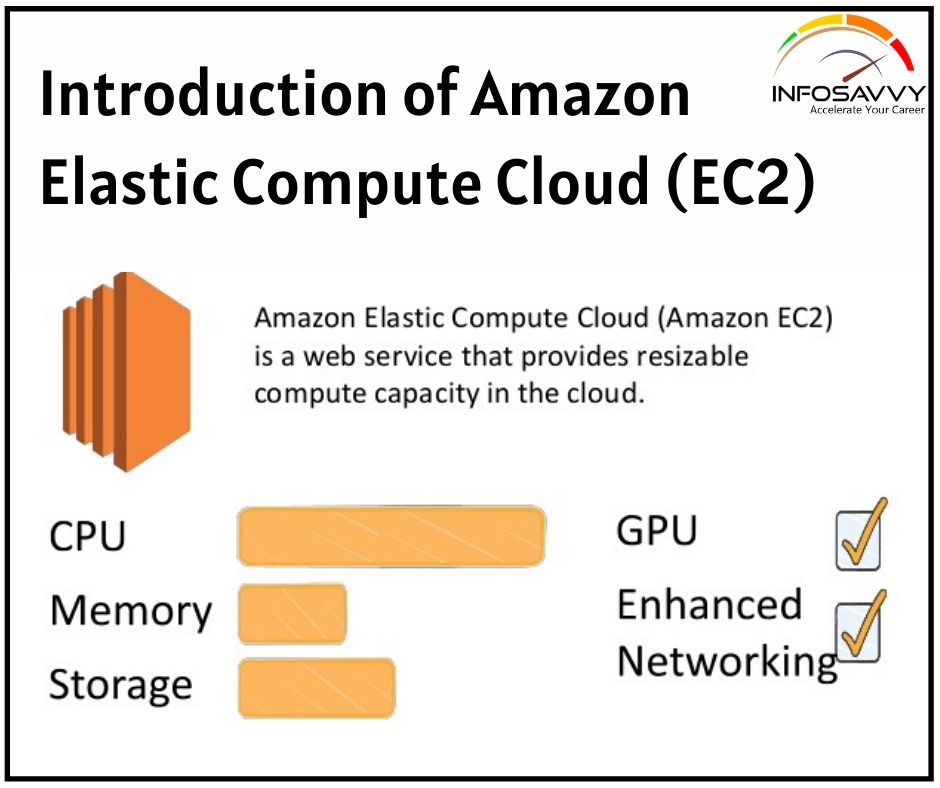
Introduction of Amazon Elastic Compute Cloud (EC2) in this blog You will learn EC2 It’s an Amazon Elastic Compute Cloud and will explore the tools and practices wont to fully leverage the ability of the EC2 ecosystem. Amazon Elastic Compute Cloud (EC2) The ultimate focus of a standard data centre/server room is its precious servers. But, to create those servers useful, you’ll got to add racks, power supplies, cabling, switches, firewalls, and cooling. AWS’s Elastic …
Introduction of Amazon Elastic Compute Cloud (EC2) Read More »