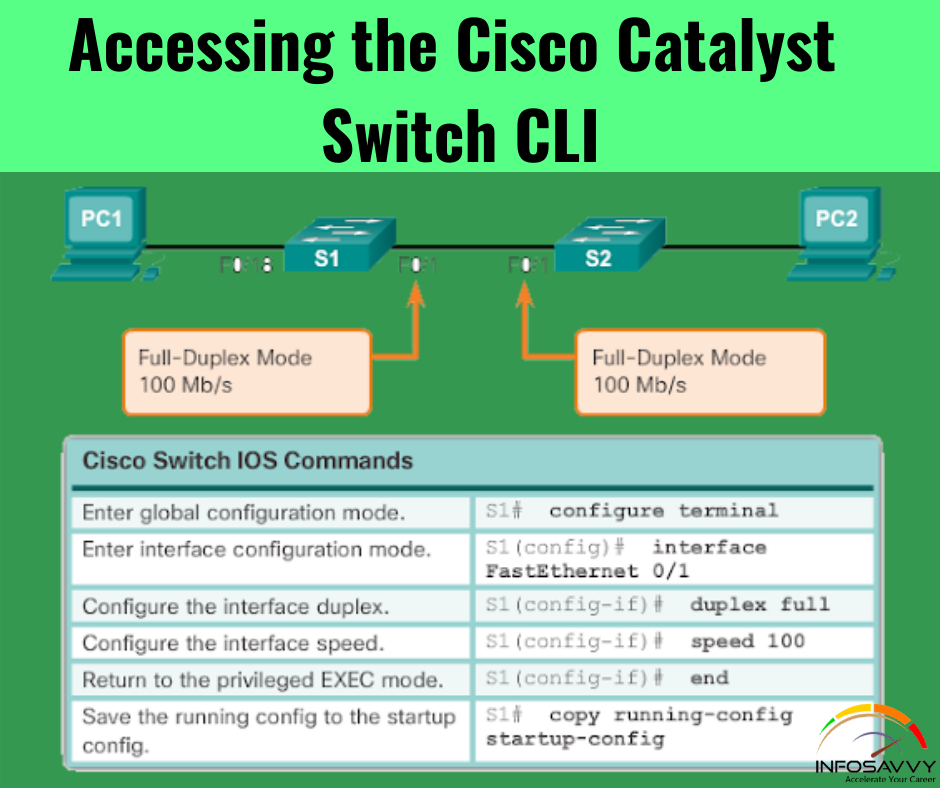
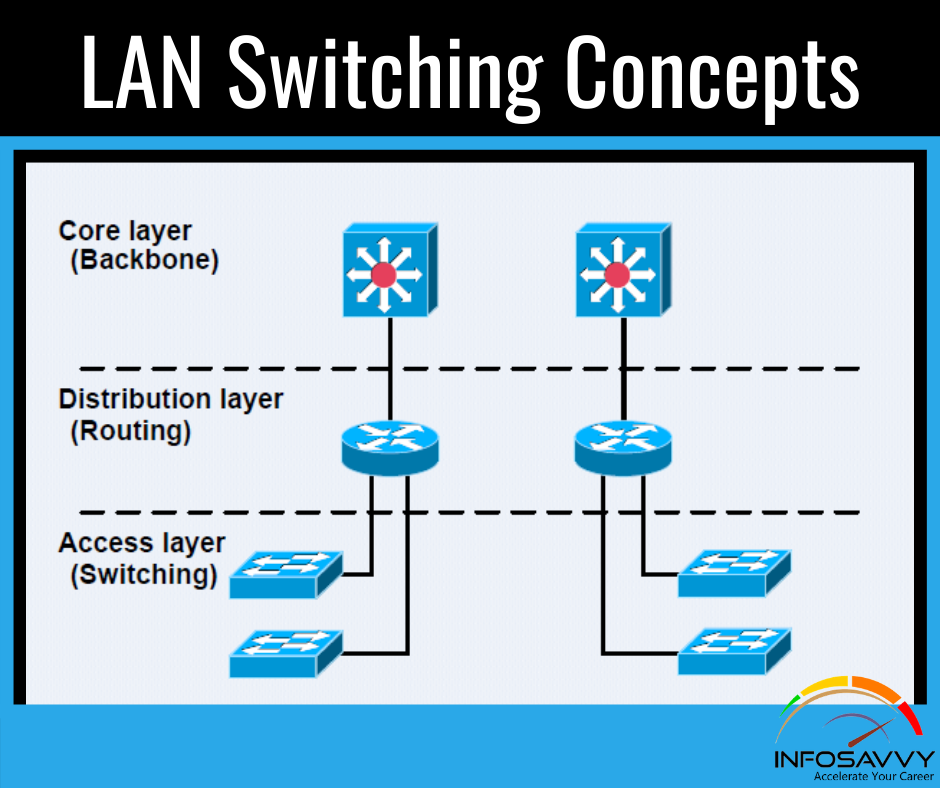
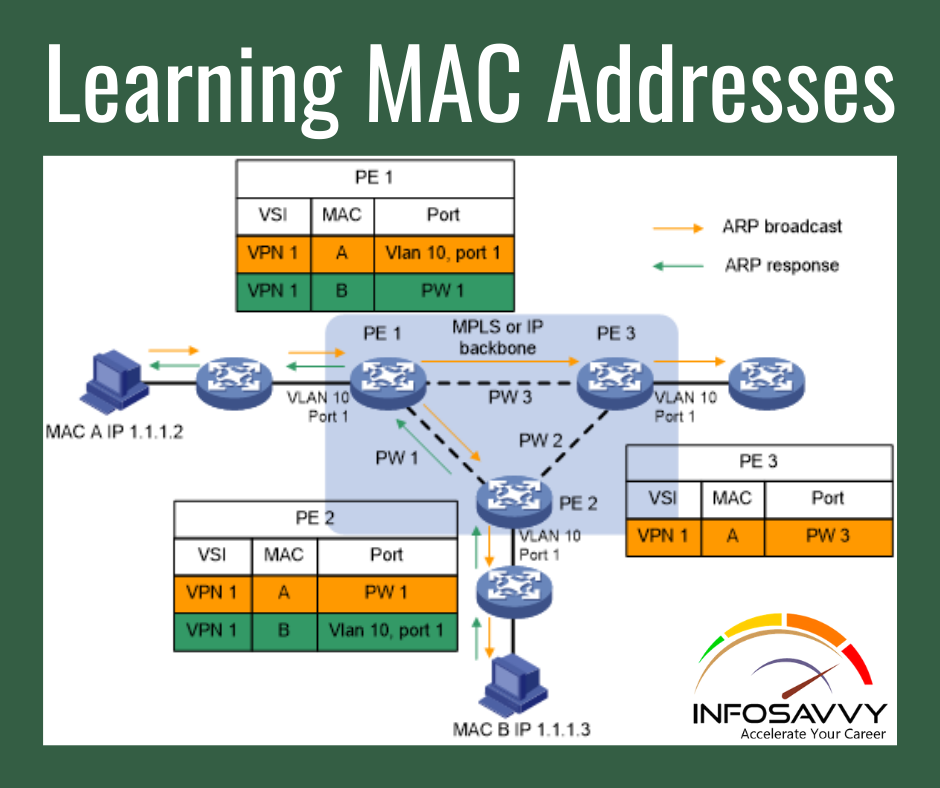
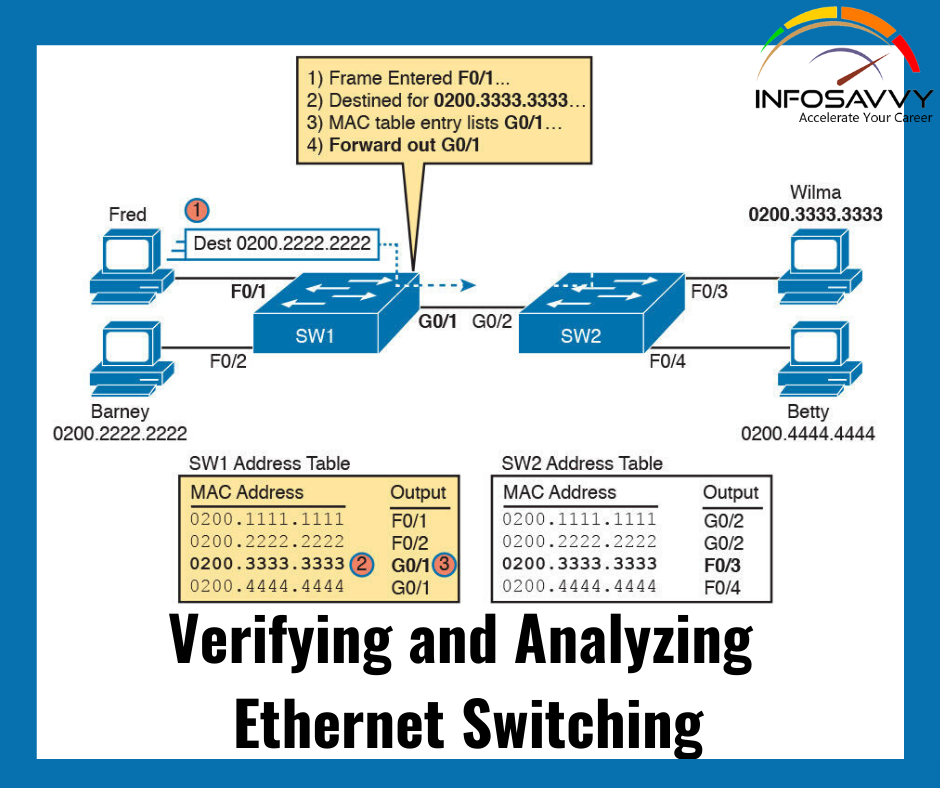
Robin, a professional hacker, targeted an organization’s network to sniff all the traffic. During this process, Robin plugged in a rough switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network. What is the attack performed by Robin in above scenario?
Robin, a professional hacker, targeted an organization’s network to sniff all the traffic. During this process, Robin plugged in a rough switch to an unused port in the LAN with a priority lower than any other switch in the network so that he could make it a root bridge that will later allow him to sniff all the traffic in the network. What is the attack performed by Robin in above scenario? Option 1 : …